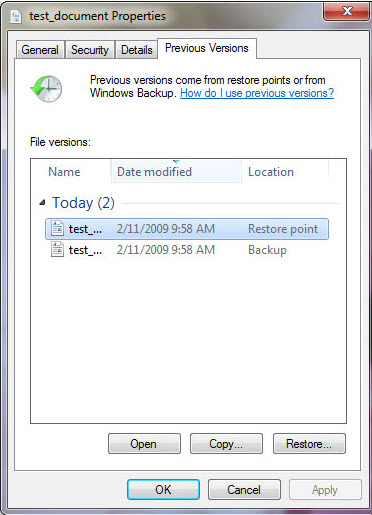
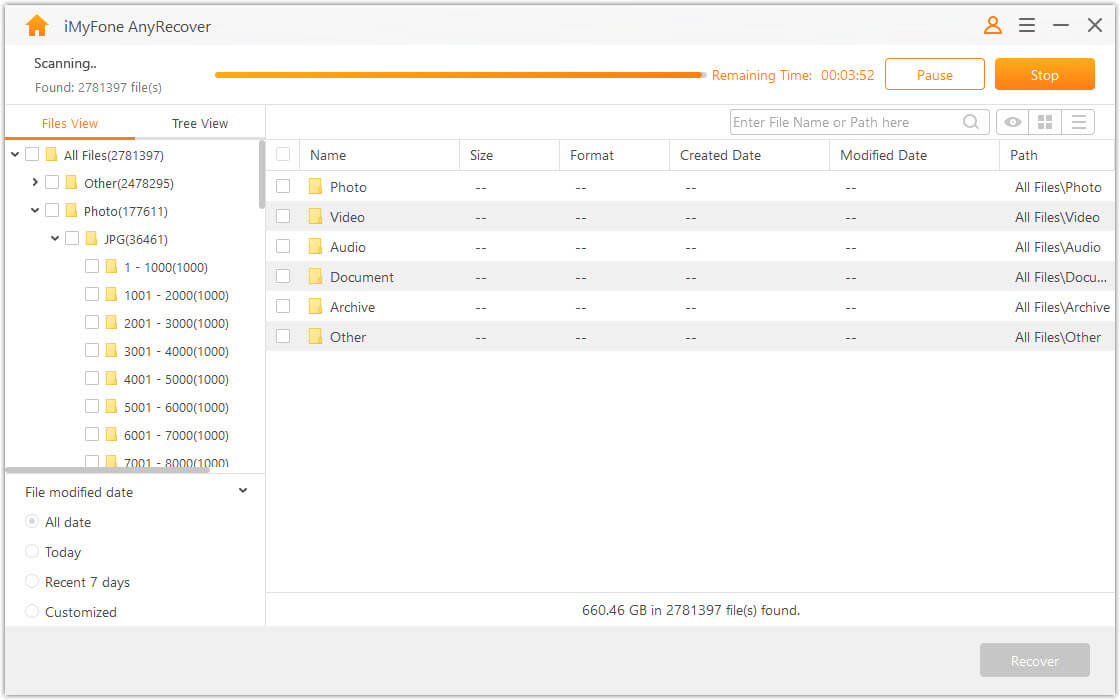
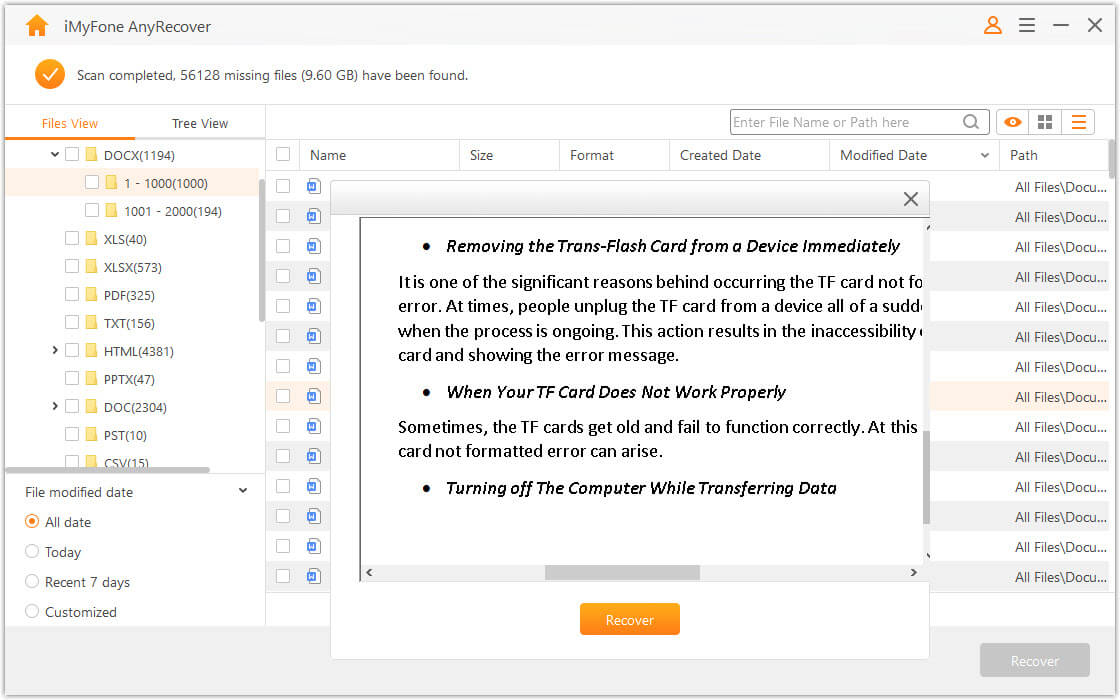
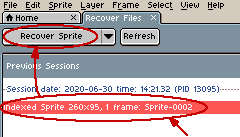
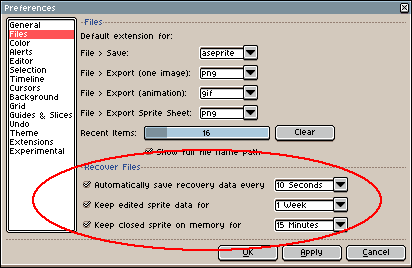
Enter a previously saved recovery code
Enter a previously saved recovery code
Two-Factor Authentication
Two-factor Authentication (2FA) provides an additional level of security to your GitLab account. Once enabled, in addition to supplying your username and password to login, you’ll be prompted for a code generated by an application on your phone.
By enabling 2FA, the only way someone other than you can log into your account is to know your username and password and have access to your phone.
Overview
Note: When you enable 2FA, don’t forget to back up your recovery codes.
In addition to a phone application, GitLab supports U2F (universal 2nd factor) devices as the second factor of authentication. Once enabled, in addition to supplying your username and password to login, you’ll be prompted to activate your U2F device (usually by pressing a button on it), and it will perform secure authentication on your behalf.
The U2F workflow is only supported by Google Chrome at this point, so we strongly recommend that you set up both methods of two-factor authentication, so you can still access your account from other browsers.
Enabling 2FA
There are two ways to enable two-factor authentication: via a mobile application or a U2F device.
Enable 2FA via mobile application
In GitLab:
On your phone:
In GitLab:
If the pin you entered was correct, you’ll see a message indicating that Two-Factor Authentication has been enabled, and you’ll be presented with a list of recovery codes.
Enable 2FA via U2F device
In GitLab:
You will see a message indicating that your device was successfully set up. Click on Register U2F Device to complete the process.
Recovery Codes
Note: Recovery codes are not generated for U2F devices.
Should you ever lose access to your phone, you can use one of the ten provided backup codes to login to your account. We suggest copying or printing them for storage in a safe place. Each code can be used only once to log in to your account.
If you lose the recovery codes or just want to generate new ones, you can do so from the Profile settings ➔ Account page where you first enabled 2FA.
Logging in with 2FA Enabled
Logging in with 2FA enabled is only slightly different than a normal login. Enter your username and password credentials as you normally would, and you’ll be presented with a second prompt, depending on which type of 2FA you’ve enabled.
Log in via mobile application
Enter the pin from your phone’s application or a recovery code to log in.
Log in via U2F device
You will see a message indicating that your device responded to the authentication request. Click on Authenticate via U2F Device to complete the process.
Disabling 2FA
This will clear all your two-factor authentication registrations, including mobile applications and U2F devices.
Personal access tokens
When 2FA is enabled, you can no longer use your normal account password to authenticate with Git over HTTPS on the command line or when using GitLab’s API, you must use a personal access token instead.
Recovery options
To disable two-factor authentication on your account (for example, if you have lost your code generation device) you can:
Use a saved recovery code
Enabling two-factor authentication for your account generated several recovery codes. If you saved these codes, you can use one of them to sign in.
To use a recovery code, enter your username/email and password on the GitLab sign-in page. When prompted for a two-factor code, enter the recovery code.
Note: Once you use a recovery code, you cannot re-use it. You can still use the other recovery codes you saved.
Generate new recovery codes using SSH
Users often forget to save their recovery codes when enabling two-factor authentication. If an SSH key is added to your GitLab account, you can generate a new set of recovery codes with SSH.
You are prompted to confirm that you want to generate new codes. Continuing this process invalidates previously saved codes.
Go to the GitLab sign-in page and enter your username/email and password. When prompted for a two-factor code, enter one of the recovery codes obtained from the command-line output.
Note: After signing in, visit your Profile settings > Account immediately to set up two-factor authentication with a new device.
Ask a GitLab administrator to disable two-factor authentication on your account
If you cannot use a saved recovery code or generate new recovery codes, ask a GitLab global administrator to disable two-factor authentication for your account. This will temporarily leave your account in a less secure state. Sign in and re-enable two-factor authentication as soon as possible.
Note to GitLab administrators
The GitLab U2F implementation does not work when the GitLab instance is accessed from multiple hostnames, or FQDNs. Each U2F registration is linked to the current hostname at the time of registration, and cannot be used for other hostnames/FQDNs.
Восстановление пароля в Роблокс — как вернуть аккаунт
Автор: Юрий Белоусов · 30.12.2020

В этой статье рассмотрим инструкцию, в которой подробно пошагово описано, как восстановить пароль в Роблокс и аккаунт, в случае взлома.
Как восстановить пароль в Роблокс, если забыл
Одна из самых распространенных причин утраты доступа к своему аккаунту – забытый пароль. Зачастую, пользователи не запоминают его и не записывают, а попросту доверяют его сохранность встроенному в браузер менеджеру паролей.
Если вы точно помните пароль, а он не подходит, то возможно на клавиатуре активирован режим Caps Lock. Необходимо его отключить.
Как восстановить пароль в Роблокс, если забыл:
Обратите внимание! Вполне возможно, что аккаунт создавался посредством входа в систему с помощью социальной сети Facebook. В таком случае на странице входа следует выбрать соответствующий способ.
Как восстановить пароль в Роблоксе с помощью телефона
Часто в качестве средства восстановления указывается не почта, а – номер телефона. Это куда более удобно и надежно.
Как восстановить пароль в Роблоксе с помощью телефона:
Как вернуть аккаунт в Роблокс, если нет почты и телефона
Как восстановить пароль от аккаунта Роблокс на телефоне
Рассмотрим, как восстановить пароль от аккаунта Роблокс на телефоне. Стоит понимать, что есть 2 инструкции: одна – для мобильной версии, то есть через браузер, а вторая – для приложения.
Восстановление пароля в Роблокс через браузер на мобильном телефоне:
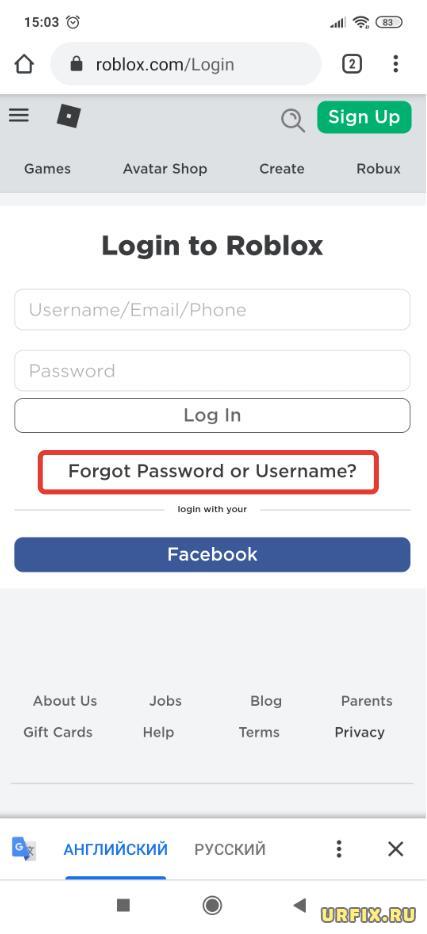
Восстановление пароля в Роблокс в приложении Android, IOS:
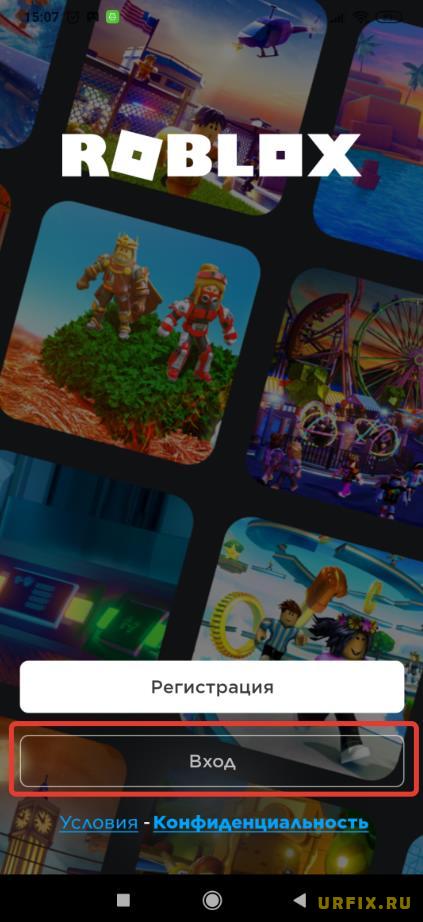
Как восстановить аккаунт в Роблокс, если взломали
Процедура восстановления аккаунта в Роблокс, в случае, если он был взломан, ничем не отличается от описанной выше. В любом случае пользователю необходимо пройти процедуру восстановления пароля стандартным методом, описанным тут.
Если возникают сложности, то можно обратиться в службу поддержки. Русский язык недоступен, поэтому обращение нужно составить на английском. Для удобства можно воспользоваться Google переводчиком.
Как восстановить пароль Роблокс без почты
Восстановить пароль в Роблокс без почты можно только в том случае, если к аккаунту привязан актуальный номер телефона. Подробную инструкцию по восстановлению можно найти тут.
Как восстановить удаленный аккаунт в Роблокс
Что делать, если старый аккаунт был удален и его нужно вернуть, как в таком случае восстановить акк в Роблокс?
Ответ: никак! Удаленные аккаунты не подлежат восстановление. Ни на компьютере, ни на телефоне.
Как зайти в Роблокс, если забыл пароль
Чтобы зайти в аккаунт Роблокс, если забыл пароль, необходимо пройти процедуру восстановления, описанную тут.
Как сбросить пароль в Роблоксе
Чтобы сбросить пароль в Роблоксе нужно пройти процедуру, описанную вначале статьи.
Не нашли ответ? Тогда воспользуйтесь формой поиска:
Recovering your account if you lose your 2FA credentials
In this article
If you lose access to your two-factor authentication credentials, you can use your recovery codes, or another recovery option, to regain access to your account.
Warnings:
Using a two-factor authentication recovery code
Type your username and password to prompt authentication.
Warning: If you protect your personal account with two-factor authentication but do not know your password, you will not be able to follow these steps to recover your account. GitHub can send a password reset email to a verified address associated with your account. For more information, see «Updating your GitHub access credentials.»
Under «Having problems?», click Use a recovery code or request a reset.
Type one of your recovery codes, then click Verify.
Authenticating with a fallback number
If you lose access to your primary TOTP app or phone number, you can provide a two-factor authentication code sent to your fallback number to automatically regain access to your account.
Authenticating with a security key
If you configured two-factor authentication using a security key, you can use your security key as a secondary authentication method to automatically regain access to your account. For more information, see «Configuring two-factor authentication.»
Authenticating with a verified device, SSH token, or personal access token
If you know your password for GitHub.com but don’t have the two-factor authentication credentials or your two-factor authentication recovery codes, you can have a one-time password sent to your verified email address to begin the verification process and regain access to your account.
Note: For security reasons, regaining access to your account by authenticating with a one-time password can take up to three business days. GitHub will not review additional requests submitted during this time.
You can use your two-factor authentication credentials or two-factor authentication recovery codes to regain access to your account anytime during the 3-5 day waiting period.
Type your username and password to prompt authentication.
Warning: If you protect your personal account with two-factor authentication but do not know your password, you will not be able to follow these steps to recover your account. GitHub can send a password reset email to a verified address associated with your account. For more information, see «Updating your GitHub access credentials.»
Under «Having problems?», click Use a recovery code or request a reset.
To the right of «Locked out?», click Try recovering your account.
Click I understand, get started to request a reset of your authentication settings.
Click Send one-time password to send a one-time password to all eligible addresses associated with your account. Only verified emails are eligible for account recovery. If you’ve restricted password resets to your primary and/or backup addresses, these addresses are the only addresses eligible for account recovery.
Under «One-time password», type the temporary password from the recovery email GitHub sent.
Click Verify email address.
Choose an alternative verification factor.
A member of GitHub Support will review your request and email you within three business days. If your request is approved, you’ll receive a link to complete your account recovery process. If your request is denied, the email will include a way to contact support with any additional questions.
Help us make these docs great!
All GitHub docs are open source. See something that’s wrong or unclear? Submit a pull request.
Enter a previously saved recovery code
If you lose your code generation device (such as your mobile phone) and you need to disable two-factor authentication on your account, you have several options.
Use a saved recovery code
When you enabled two-factor authentication for your account, a series of recovery codes were generated. If you saved those codes somewhere safe, you may use one to sign in.
First, enter your username/email and password on the GitLab sign in page. When prompted for a two-factor code, enter one of the recovery codes you saved previously.
Note: Once a particular recovery code has been used, it cannot be used again. You may still use the other saved recovery codes at a later time.
Generate new recovery codes using SSH
It’s not uncommon for users to forget to save the recovery codes when enabling two-factor authentication. If you have an SSH key added to your GitLab account, you can generate a new set of recovery codes using SSH.
Next, go to the GitLab sign in page and enter your username/email and password. When prompted for a two-factor code, enter one of the recovery codes obtained from the command line output.
Ask a GitLab administrator to disable two-factor on your account
If the above two methods are not possible, you may ask a GitLab global administrator to disable two-factor authentication for your account. Please be aware that this will temporarily leave your account in a less secure state. You should sign in and re-enable two-factor authentication as soon as possible after the administrator disables it.
Two-factor authentication (FREE)
Two-factor authentication (2FA) provides an additional level of security to your GitLab account. For others to access your account, they would need your username and password and access to your second factor of authentication.
GitLab supports as a second factor of authentication:
If you set up a device, also set up a TOTP so you can still access your account if you lose the device.
Use personal access tokens with two-factor authentication
When 2FA is enabled, you can’t use your password to authenticate with Git over HTTPS or the GitLab API. You can use a personal access token instead.
Git Credential Manager
For Git over HTTPS, Git Credential Manager (GCM) offers an alternative to personal access tokens. By default, GCM authenticates using OAuth, opening GitLab in your web browser. The first time you authenticate, GitLab asks you to authorize the app. If you remain signed in to GitLab, subsequent authentication requires no interaction.
So you don’t need to reauthenticate on every push, GCM supports caching as well as a variety of platform-specific credential stores that persist between sessions. This feature is useful whether you use personal access tokens or OAuth.
GCM supports GitLab.com out the box. To use with self-managed GitLab, see GitLab support documentation.
Git Credential Manager is developed primarily by GitHub, Inc. It is an open-source project and is supported by the community.
Enable two-factor authentication
You can enable 2FA:
In GitLab 14.3 and later, your account email must be confirmed to enable 2FA.
Enable one-time password
To enable 2FA with a one-time password:
If you entered the correct pin, GitLab displays a list of recovery codes. Download them and keep them in a safe place.
Enable one-time password using FortiAuthenticator
You can use FortiAuthenticator as a one-time password (OTP) provider in GitLab. Users must:
You need a username and access token for FortiAuthenticator. The access_token shown below is the FortAuthenticator access key. To get the token, see the REST API Solution Guide at Fortinet Document Library. GitLab 13.5 has been tested with FortAuthenticator version 6.2.0.
Configure FortiAuthenticator in GitLab. On your GitLab server:
Open the configuration file.
For Omnibus GitLab:
For installations from source:
Add the provider configuration:
For Omnibus package:
For installations from source:
Save the configuration file.
Reconfigure (Omnibus GitLab) or restart (GitLab installed from source).
Enable one-time password using FortiToken Cloud
You can use FortiToken Cloud as a one-time password (OTP) provider in GitLab. Users must:
You need a client_id and client_secret to configure FortiToken Cloud. To get these, see the REST API Guide at Fortinet Document Library.
Configure FortiToken Cloud in GitLab. On your GitLab server:
Open the configuration file.
For Omnibus GitLab:
For installations from source:
Add the provider configuration:
For Omnibus package:
For installations from source:
Save the configuration file.
Reconfigure (Omnibus GitLab) or restart (GitLab installed from source).
Set up a U2F device
GitLab officially supports YubiKey U2F devices, but users have successfully used SoloKeys and Google Titan Security Key.
U2F is supported by the following desktop browsers:
Firefox 67+. For Firefox 47-66:
To set up 2FA with a U2F device:
A message displays indicating that your device was successfully set up. Select Register U2F Device to complete the process. Recovery codes are not generated for U2F devices.
Set up a WebAuthn device
To set up 2FA with a WebAuthn-compatible device:
A message displays indicating that your device was successfully set up. Recovery codes are not generated for WebAuthn devices.
Recovery codes
Introduced in GitLab 13.7, Copy codes and Print codes buttons.
Immediately after successfully enabling 2FA with a one-time password, you’re prompted to download a set of generated recovery codes. If you ever lose access to your one-time password authenticator, you can use one of these recovery codes to sign in to your account.
WARNING: Each code can be used only once to sign in to your account.
NOTE: Recovery codes are not generated for U2F or WebAuthn devices.
If you lose the recovery codes, or want to generate new ones, you can use either:
Regenerate two-factor authentication recovery codes
To regenerate 2FA recovery codes, you need access to a desktop browser:
NOTE: If you regenerate 2FA recovery codes, save them. You can’t use any previously created 2FA codes.
Sign in with two-factor authentication enabled
Signing in with 2FA enabled is only slightly different than the normal sign-in process. Enter your username and password and you’re presented with a second prompt, depending on which type of 2FA you’ve enabled.
Sign in using a one-time password
When asked, enter the pin from your one time password authenticator’s application or a recovery code to sign in.
Sign in using a U2F device
To sign in by using a U2F device:
A message displays indicating that your device responded to the authentication request, and you’re automatically signed in.
Sign in using a WebAuthn device
In supported browsers, you should be automatically prompted to activate your WebAuthn device (for example, by touching or pressing its button) after entering your credentials.
A message displays indicating that your device responded to the authentication request and you’re automatically signed in.
Disable two-factor authentication
This clears all your 2FA registrations, including mobile applications and U2F or WebAuthn devices.
Recovery options
If you don’t have access to your code generation device, you can recover access to your account:
Use a saved recovery code
To use a recovery code:
After you use a recovery code, you cannot re-use it. You can still use the other recovery codes you saved.
Generate new recovery codes using SSH
Users often forget to save their recovery codes when enabling 2FA. If you added an SSH key to your GitLab account, you can generate a new set of recovery codes with SSH:
On self-managed instances, replace gitlab.com in the command above with the GitLab server hostname ( gitlab.example.com ).
You are prompted to confirm that you want to generate new codes. This process invalidates previously-saved codes. For example:
Go to the GitLab sign-in page and enter your username or email, and password. When prompted for a two-factor code, enter one of the recovery codes obtained from the command-line output.
After signing in, immediately set up 2FA with a new device.
Have two-factor authentication disabled on your account (PREMIUM SAAS)
If other methods are unavailable, submit a support ticket to request a GitLab global administrator disable 2FA for your account:
Information for GitLab administrators (FREE SELF)
Take care that 2FA keeps working after restoring a GitLab backup.
To ensure 2FA authorizes correctly with a time-based one time passwords (TOTP) server, synchronize your GitLab server’s time using a service like NTP. Otherwise, authorization can always fail because of time differences.
The GitLab U2F and WebAuthn implementation does not work when the GitLab instance is accessed from multiple hostnames or FQDNs. Each U2F or WebAuthn registration is linked to the current hostname at the time of registration, and cannot be used for other hostnames or FQDNs.
For example, if a user is trying to access a GitLab instance from first.host.xyz and second.host.xyz :
To enforce 2FA at the system or group levels see, Enforce two-factor authentication.
Troubleshooting
If you receive an invalid pin code error, this can indicate that there is a time sync issue between the authentication application and the GitLab instance itself. To avoid the time sync issue, enable time synchronization in the device that generates the codes. For example:
Two-factor authentication (FREE)
Two-factor authentication (2FA) provides an additional level of security to your GitLab account. For others to access your account, they would need your username and password and access to your second factor of authentication.
GitLab supports as a second factor of authentication:
If you set up a device, also set up a TOTP so you can still access your account if you lose the device.
Use personal access tokens with two-factor authentication
When 2FA is enabled, you can’t use your password to authenticate with Git over HTTPS or the GitLab API. You can use a personal access token instead.
Git Credential Manager
For Git over HTTPS, Git Credential Manager (GCM) offers an alternative to personal access tokens. By default, GCM authenticates using OAuth, opening GitLab in your web browser. The first time you authenticate, GitLab asks you to authorize the app. If you remain signed in to GitLab, subsequent authentication requires no interaction.
So you don’t need to reauthenticate on every push, GCM supports caching as well as a variety of platform-specific credential stores that persist between sessions. This feature is useful whether you use personal access tokens or OAuth.
GCM supports GitLab.com out the box. To use with self-managed GitLab, see GitLab support documentation.
Git Credential Manager is developed primarily by GitHub, Inc. It is an open-source project and is supported by the community.
Enable two-factor authentication
You can enable 2FA:
In GitLab 14.3 and later, your account email must be confirmed to enable 2FA.
Enable one-time password
To enable 2FA with a one-time password:
If you entered the correct pin, GitLab displays a list of recovery codes. Download them and keep them in a safe place.
Enable one-time password using FortiAuthenticator
You can use FortiAuthenticator as a one-time password (OTP) provider in GitLab. Users must:
You need a username and access token for FortiAuthenticator. The access_token shown below is the FortAuthenticator access key. To get the token, see the REST API Solution Guide at Fortinet Document Library. GitLab 13.5 has been tested with FortAuthenticator version 6.2.0.
Configure FortiAuthenticator in GitLab. On your GitLab server:
Open the configuration file.
For Omnibus GitLab:
For installations from source:
Add the provider configuration:
For Omnibus package:
For installations from source:
Save the configuration file.
Reconfigure (Omnibus GitLab) or restart (GitLab installed from source).
Enable one-time password using FortiToken Cloud
You can use FortiToken Cloud as a one-time password (OTP) provider in GitLab. Users must:
You need a client_id and client_secret to configure FortiToken Cloud. To get these, see the REST API Guide at Fortinet Document Library.
Configure FortiToken Cloud in GitLab. On your GitLab server:
Open the configuration file.
For Omnibus GitLab:
For installations from source:
Add the provider configuration:
For Omnibus package:
For installations from source:
Save the configuration file.
Reconfigure (Omnibus GitLab) or restart (GitLab installed from source).
Set up a U2F device
GitLab officially supports YubiKey U2F devices, but users have successfully used SoloKeys and Google Titan Security Key.
U2F is supported by the following desktop browsers:
Firefox 67+. For Firefox 47-66:
To set up 2FA with a U2F device:
A message displays indicating that your device was successfully set up. Select Register U2F Device to complete the process. Recovery codes are not generated for U2F devices.
Set up a WebAuthn device
To set up 2FA with a WebAuthn-compatible device:
A message displays indicating that your device was successfully set up. Recovery codes are not generated for WebAuthn devices.
Recovery codes
Introduced in GitLab 13.7, Copy codes and Print codes buttons.
Immediately after successfully enabling 2FA with a one-time password, you’re prompted to download a set of generated recovery codes. If you ever lose access to your one-time password authenticator, you can use one of these recovery codes to sign in to your account.
WARNING: Each code can be used only once to sign in to your account.
NOTE: Recovery codes are not generated for U2F or WebAuthn devices.
If you lose the recovery codes, or want to generate new ones, you can use either:
Regenerate two-factor authentication recovery codes
To regenerate 2FA recovery codes, you need access to a desktop browser:
NOTE: If you regenerate 2FA recovery codes, save them. You can’t use any previously created 2FA codes.
Sign in with two-factor authentication enabled
Signing in with 2FA enabled is only slightly different than the normal sign-in process. Enter your username and password and you’re presented with a second prompt, depending on which type of 2FA you’ve enabled.
Sign in using a one-time password
When asked, enter the pin from your one time password authenticator’s application or a recovery code to sign in.
Sign in using a U2F device
To sign in by using a U2F device:
A message displays indicating that your device responded to the authentication request, and you’re automatically signed in.
Sign in using a WebAuthn device
In supported browsers, you should be automatically prompted to activate your WebAuthn device (for example, by touching or pressing its button) after entering your credentials.
A message displays indicating that your device responded to the authentication request and you’re automatically signed in.
Disable two-factor authentication
This clears all your 2FA registrations, including mobile applications and U2F or WebAuthn devices.
Recovery options
If you don’t have access to your code generation device, you can recover access to your account:
Use a saved recovery code
To use a recovery code:
After you use a recovery code, you cannot re-use it. You can still use the other recovery codes you saved.
Generate new recovery codes using SSH
Users often forget to save their recovery codes when enabling 2FA. If you added an SSH key to your GitLab account, you can generate a new set of recovery codes with SSH:
On self-managed instances, replace gitlab.com in the command above with the GitLab server hostname ( gitlab.example.com ).
You are prompted to confirm that you want to generate new codes. This process invalidates previously-saved codes. For example:
Go to the GitLab sign-in page and enter your username or email, and password. When prompted for a two-factor code, enter one of the recovery codes obtained from the command-line output.
After signing in, immediately set up 2FA with a new device.
Have two-factor authentication disabled on your account (PREMIUM SAAS)
If other methods are unavailable, submit a support ticket to request a GitLab global administrator disable 2FA for your account:
Information for GitLab administrators (FREE SELF)
Take care that 2FA keeps working after restoring a GitLab backup.
To ensure 2FA authorizes correctly with a time-based one time passwords (TOTP) server, synchronize your GitLab server’s time using a service like NTP. Otherwise, authorization can always fail because of time differences.
The GitLab U2F and WebAuthn implementation does not work when the GitLab instance is accessed from multiple hostnames or FQDNs. Each U2F or WebAuthn registration is linked to the current hostname at the time of registration, and cannot be used for other hostnames or FQDNs.
For example, if a user is trying to access a GitLab instance from first.host.xyz and second.host.xyz :
To enforce 2FA at the system or group levels see, Enforce two-factor authentication.
Troubleshooting
If you receive an invalid pin code error, this can indicate that there is a time sync issue between the authentication application and the GitLab instance itself. To avoid the time sync issue, enable time synchronization in the device that generates the codes. For example:
Как восстановить свой аккаунт roblox запрещен в 2022 году
Как восстановить свою учетную запись Roblox без электронной почты или номера телефона Вы забыли свой пароль Roblox, но потеряли доступ к своей электронной почте и номеру телефона? Если у вас
Как восстановить свою учетную запись Roblox без электронной почты или номера телефона
Вы забыли свой пароль Roblox, но потеряли доступ к своей электронной почте и номеру телефона?
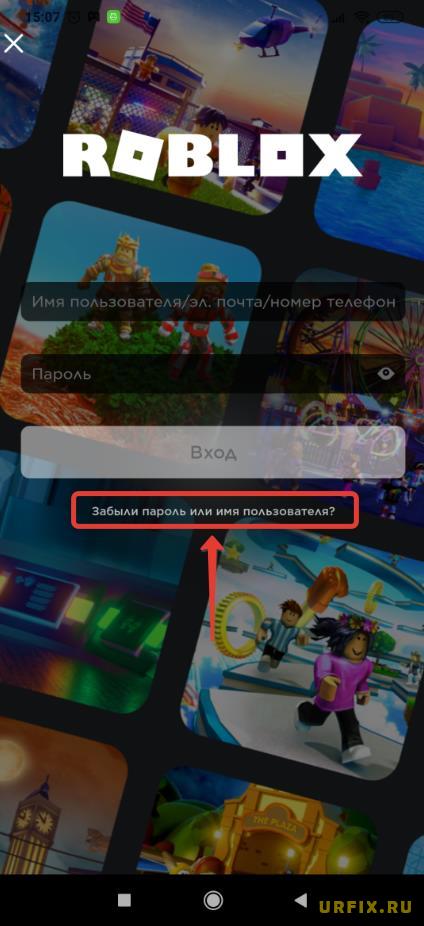
Если у вас все еще есть доступ к электронной почте и номеру телефона, вы можете сбросить пароль, нажав на «Забыли пароль или имя пользователя?» ссылка.
Ссылка находится на странице входа Роблокса.
Затем вы можете использовать свой адрес электронной почты или номер телефона, чтобы сбросить пароль.
Однако, если у вас нет к ним доступа, вы не можете использовать этот метод.
Вместо этого вам придется обратитесь в службу поддержки Roblox для оказания помощи.
В противном случае вы не сможете восстановить свою учетную запись Roblox и сбросить пароль.
В этом руководстве вы узнаете, как восстановить свою учетную запись Roblox без адреса электронной почты или номера телефона.
Пошаговое руководство по вопросу восстановления учетной записи Roblox (2022 г.)
Как сбросить и изменить пароль Roblox с помощью электронной почты и номера телефона?
1. Как сбросить пароль с помощью электронной почты Roblox?
2. Как изменить пароль с помощью номера телефона?
После всего этого вы сможете войти в свой аккаунт Roblox. Помните, что пароль нужно менять часто, чтобы сохранить аккаунт в безопасности.
3. Восстановление аккаунта Roblox без электронной почты или номера телефона
убедитесь, что вы точно знаете, какой email вы использовали для создания аккаунта.
4. Как вернуть аккаунт Roblox без электронной почты или номера телефона?
Восстановление учетной записи Roblox без электронной почты или номер телефона
Если вы считаете, что ваша учетная запись Roblox была взломана, и вы хотите восстановить ее без доступа к электронной почте или номеру телефона, есть способ сделать это. Для этого убедитесь, что вы точно знаете, какой адрес электронной почты вы использовали для создания учетной записи.
Как получить учетную запись Roblox Вернуться без электронной почты или номера телефона?
Для получения дополнительных советов и кодов посетите наш раздел Roblox на Guideer.
Как вернуть аккаунт в Роблокс, если нет почты и телефона
Что делать, если профиль в Roblox забанли или удалили
Если геймера забанили и страничку удалили несправедливо, вернуть доступ к ней можно только в том случае, если вы не совершали неправомерных действий в игре. Для этого следует обратиться в службу поддержки и заполнить специальную форму. Здесь вводится такая информация как имя, адрес электронной почты, а также описание ситуации.
В ближайшее время письмо будет рассмотрено и принято решение. Апелляция будет в пользу игрока только в том случае, если он не нарушал правил Roblox. В противном случае решение будет вынесено не в пользу геймера.
Защитите свою учетную запись Roblox
Перейти к вашей Настройки аккаунта Roblox и нажмите » Безопасность«.
Доступны несколько вариантов:
Если все эти шаги будут выполнены, ваша учетная запись будет в безопасности, и у вас не возникнет никаких проблем. Удачной вам игры, не забудьте поделиться своим опытом в комментариях!
Почему не работает Roblox? Что за сбой 10 мая?
На большей части России сегодня 10 май 2022 не работает Роблокс. Сбои зарегистрированы в следующих регионах страны:
Add a Recovery Email Address to Your Microsoft Account
Don’t be locked out of your Outlook.com or Hotmail email account
What to Know
This article explains how to add an alternate email address on Outlook.com in case you need to recover your Microsoft Account.
How to Add a Recovery Email Address to Outlook.com
Including a recovery email address is easy to do:
Log on to your email account at Outlook.com in a browser.
Select your avatar or initials on the far right side of the menu bar to open your My Account screen.
Press View account.
Select the Security tab at the top of the My Account screen.
Choose Update Info in the Update your security info area.
Verify your identity, if asked to do so. For example, you may be asked to enter a code sent to your phone number, if you previously entered a recovery phone number.
Select Add security info.
Choose An alternate email address from the first drop-down menu.
Enter an email address to serve as your recovery email address for your Microsoft account.
Press Next. Microsoft will email the new recovery address with a code.
Enter the code from the email in the Code area of the Add security info window.
Press Next to save the changes and add the recovery email address to your Microsoft account.
Verify that the email password recovery address was added by returning to the Update your security info section. Your Microsoft email account should also receive an email that says you updated your security information.
You can add multiple recovery addresses and phone numbers by repeating these steps. When you want to reset your password, you can choose which alternate email address or phone number the code should be sent to.
Why Do You Need a Recovery Email Address?
Outlook.com is home to your Outlook, Hotmail, and other Microsoft email accounts. Your password is the key to all your email there. If you forget your password though, you’ll need to recover your account and create a new one. To simplify the password change, add a secondary email address or phone number to Outlook.com, so that you can reset your password and access your account while keeping your account secure.
A recovery email address makes it easy to change your password and more difficult for your account to be hacked. Microsoft sends a code to an alternate email address to validate you are who you say you are. You enter the code in a field and then you are allowed to make changes to your account—including a new password.
Select a Strong Password
Microsoft encourages its email users to use a strong password with their Microsoft email address. Microsoft’s recommendations include:
Also, Microsoft recommends turning on two-step verification to make it difficult for someone else to sign in to your Microsoft account. With two-step verification activated, whenever you sign in on a new device or from a different location, Microsoft sends a security code that you must enter on the sign-in page.
Как разблокировать аккаунт после 5 неудачных попыток входа
Как разблокировать аккаунт после 5 неудачных попыток входа
Наверное, каждый сталкивался с ошибкой при попытке авторизации с не валидными данными, которая по-английски звучит так
Sorry, there have been more than 5 failed login attempts for this account. It is temporarily blocked. Try again later or request a new password.
Аккаунт временно заблокирован по причине более чем 5 неудачных попыток входа. Попробуйте войти позже, или запросите новый пароль.
Это простая самооборона Друпала, которая активируется после 5 (по умолчанию) попыток входа. Таким образом, система не позволяет злоумышленникам забрутофорсить (англ. brute force. Cм. Полный перебор) сайт. Работает она достаточно просто: во время каждой авторизации, Друпал сохраняет ip-адрес пользователя, запоминая при этом, точную дату события и дату окончания «срока годности» попытки.
Вот некоторые нюансы:
Вот еще один интересный факт:
Вы можете имя пользователя указать верно, но при этом 5 раз ошибиться с паролем. В таком случае, попытки авторизации будут запрещены на 6 часов. При этом, через 60 минут можно будет повторить попытку входа, но с другого ip-адреса.
Что касается простых смертных — мы разобрались. Администраторы, же или программисты могут сталкиваться с этой проблемой чаще, т.к. им хлеб в рот не клади, дай только что-нибудь сломать. К счастью, для тех у кого есть доступ к Драшу или напрямую к базе могут обойтись без сброса пароля или часового ожидания. Нужно просто почистить таблицу flood
. Вот восемь способов это сделать.
Проблемы, ошибки, неточности в тексте пишите в комментах.
Microsoft Account Recovery Code
What and why with instructions included
A Microsoft account recovery code
A Microsoft recovery code — more correctly, a recovery code for a Microsoft account — is a safety net. It’s a huge safety net, in fact. If you haven’t already done so, I strongly suggest you create one now.
It didn’t dawn on me until recently that these codes are very precious. Having one may be the ultimate proof of Microsoft account ownership.
Microsoft Account recovery codes
A Microsoft account recovery code is a magic number proving you’re authorized to access your account. Generate one via your Microsoft account’s security settings before you need it, and keep it in a safe place. If you ever get locked out it may be the only way you’ll be able to regain access to your account.
What a recovery code is
A recovery code is nothing more than a long, complex number. In fact, it looks very much like an old-style Microsoft product key.
Here’s an example: A Microsoft account recovery code. (Click for larger image.)
It’s a number that’s generated and assigned to you on request.
Possession is 99.999% of the law
I’ll put it differently: being able to provide the code when requested may be enough to regain access to your Microsoft account should you ever forget your password, be unable to recover it, or get locked out of the account (perhaps when travelling).
A recovery code, then, is very valuable. Once you get one, you need to keep it safe and secure. If you store it digitally, as I do, that means you encrypt it. If you store it physically, perhaps by printing it out, then you save that paper in a very safe and secure location.
There can be only one
If you note the wording of the dialog above closely, you’ll see that it says, “If you previously had a recovery code, it is no longer valid.”
Each time you generate a code for an account, it replaces the previous one. 2 Should you get a new one, make sure you replace any previous copies you’ve kept.
My understanding is that a code can be used only once. Make sure to get a new one should you ever use yours.
Get it before you need it
A Microsoft account recovery code is useful only if it’s been created before you need it. You need to be able to log in to your account to create it.
If you can’t log in, you can’t create a code. Without a code, you’ll need to find some other way to log in or recover your account.
How to get a Microsoft recovery code
While signed in to your Microsoft account, click on your profile icon (or initials, if you haven’t set a profile image) in the upper right, and then click on My account.
Microsoft “My account” link (via Outlook.com).
You may then need to scroll down to click on Update underneath “Update your security info”.
Update your security info.
Next you’ll reconfirm either your password, PIN, or other authentication method to confirm you’re authorized to make changes.
Look for “Advanced security options” and click Get started.
Advanced Security Options
You’ll then be presented with your new code. A Microsoft account recovery code. (Click for larger image.)
How to save your code
As I mentioned above, this code needs to be saved so it’s available to you when you need it, but it also needs to be saved securely so it doesn’t fall into the hands of someone who could use it to hack
Most importantly, make sure you have access when you need it.
One common scenario where a Microsoft account recovery code comes in handy is if you find yourself locked out because you’re traveling. Possession of the recovery code should prove that you are who you say you are, even if you’re in another country, and should allow you back into your account.
If you get hacked
If someone else gains unauthorized access to your account, they could change the recovery code, and the one you have will no longer work. Not all hackers do this, but some are savvy enough to change all of your recovery information, including this code.
Then you’ll have to follow account recovery instructions to manually regain access to your account, and hope that the process works. (Sadly, it’s not uncommon that it does not.)
And, of course, make sure that you’re always backing up your email, just in case.
Hopefully you’ll never need your recovery code, but if you found this article helpful, you’ll love Confident Computing! My weekly email newsletter is full of articles that help you solve problems, stay safe, and increase your confidence with technology.
Related Questions
How do I find my Microsoft recovery code?
You cannot find your Microsoft recovery code if you have not created it ahead of time. You must create it before you need it and store it in a safe place. Then, when the time comes that you do need it, you’ll find your Microsoft recovery code in the secure place you placed it.
How can I recover my Microsoft account without email?
In general, you cannot recover a Microsoft account for which you do not know the email address. The email address uniquely identifies each account and is fundamental to both use and recovery. If for some reason, you cannot access your Microsoft account you can create a new, temporary one, that can be used to communicate with Microsoft as part of their account recovery process for your lost account.
Why did I get Microsoft verification code?
If you’re attempting to sign in you may get a Microsoft verification code via SMS [Short Message Service]
Recover Your Microsoft Account Later by Setting Up a Recovery Code NOW – Step by Step Instructions
Here at Ask Leo!, I hear from people with lost, hacked and inaccessible accounts daily.
Nowhere does this seem to happen more frequently than with Hotmail and Outlook.com accounts (now known simply as Microsoft accounts).
Given the increased importance of Microsoft accounts for everything from email to cloud
Microsoft has instituted a fairly obscure security measure that can help you regain access to your account should you lose it: the recovery code. The only “catch” is that you have to set it up before you need it.
So let’s set it up right now.
Setting Up a Recovery Code
A recovery code can get you back in to your Microsoft account when other techniques, like alternate email addresses and phones, cannot. Set one up before you need it by signing into your account, and visiting More security settings. Save the security code in a secure location such that it’s available whenever and wherever you might need it to sign in to your account later.
Getting a recovery code
Recovery codes are generated by Microsoft, and must be retrieved before you need them. Once you have a recovery code, you keep it in a safe place until you need it.
To get a recovery code, begin by logging into your account 1 and clicking on your avatar/picture (or the default placeholder) in the upper right. Then click on View account.
Depending on the width of your display window, you’ll either have a full menu bar across the top, or you’ll need to click a small down-arrow next to the word Account on the menu bar. In either case, click on Security & privacy.
On the resulting page, click on More security settings.
At this point, you may be asked to confirm your identity again, using a text or phone message or alternate email address. This added layer of security is important, as it confirms that you are indeed the person who owns the account, and that you are the person who can rightfully create and hold the account recovery code.
Once you’ve passed this additional layer of security, you’ll land on the “Security settings” page.
Scroll down and look for the section labeled “Recovery code”.
Click on Get recovery code (or Replace recovery code if you already have one).
Your new recovery code is displayed. The code is lengthy, and actually looks a little like a product key. Any previous recovery code you may have had for this account is no longer valid.
Storing your recovery code
Your recovery code is important, but also sensitive. It should not be shared with anyone, and must be stored securely. Anyone with the recovery code could be able to hijack your account.
I save it to a file (so I can copy/paste it when needed, instead of having to type it in) and keep that file in an encrypted location.
Using your recovery code
There are various scenarios in which you can use your recovery code to regain access to your Microsoft account.
As we saw in How do I get into my Hotmail/Outlook.com account if I don’t have the recovery phone or email any more?, Microsoft may ask you if you have one as one of your account recovery options.
If you do have one, it’s kind of like a free pass to regaining control of your account.
And if you’ve followed the instructions above, you now have one.
Hopefully you’ll never need it, but if you found this article helpful, you’ll love Confident Computing! My weekly email newsletter is full of articles that help you solve problems, stay safe, and increase your confidence with technology.
Podcast audio
Note: This article does get updated from time to time, as Microsoft changes the interface to access your Microsoft Security Settings (though there’s typically a delay).
Footnotes & references
1 : You must be able to log in to your account. If you cannot log in to your account, you cannot generate this type of recovery code. This is why I stress that you need to set this up before you need it. Posted: October 21, 2016 in: Outlook.com
This is an update to an article originally posted May 8, 2015
Shortlink: https://askleo.com/16142
Tagged: account recovery, account security, recovery code
Leo Who?
120 comments on “Recover Your Microsoft Account Later by Setting Up a Recovery Code NOW – Step by Step Instructions”
You could also keep it as a secure note in a password manager. LastPass has such facility, I assume that Roboform, Keepass and others have something similar.
Thanks for this tip Leo. I found that one of the best places to store this code and other important bits of information is in RoboForm’s “Safe Notes”. They are always to hand, they are backed up in RoboForm’s “cloud” and you can sync them with your RoboForm on portable devices too.
In your browser, go to http://www.outlook.com and you’ll be presented with the login interface. This is where Leo is getting his screenshots. 🙂
Took me a while too. I normally only use my Microsoft account for OneDrive and account management isn’t under options in the gear menu there. However, by selecting my name to the right of the gear I found Account Settings. There are quite a few other changes too. The code isn’t on-screen now. You can arrange how to get it.
Well, they sent me a 7 digit number, but that was just to verify it was me. Then I found the Recovery Code setting as above, so sorry for jumping in too quickly.
Dear Gabe, my problem was that I never acces to http://www.hotmail.com, now I hav e my code, this is the first time I open http://www.hotmail.com
Going to hotmail.com should automatically redirect you to Outlook.com where you can login with your account credentials.
To save the code in a SAFE place, print it on paper and file it in a place known only to you with a note on a index card placed inside the computer as a key to finding the code print out in case you forgot where you put it and tell a trusted friend what you did and why in case your memory needs a jog to find the code if you forget. Don’t rely on a computer to recover your security codes or email addresses or other sensitive info. Crashes can be disastrous.
To verify that this is your email address, complete the hidden part and click “Send code” to receive your code.
so i can’t know the email i have that broplem. my email is blocket is
One issue you may be having is from posting your email address in public forums. That increases your level of spam. Here is an article that you may find informative: http://askleo.com/giving-away-our-privacy/
Your ability to remember what you set it to is part of what “proves” you are the rightful owner. If you can’t remember it, then you can’t prove that.
Hi Leo,
I’m not happy with keeping codes/product keys. I prefer to do it only out of compulsion. The reason is that after sometime, I usually forget where I’ve kept it. This is the reason that I’m scared whenever I need to secure anything. Now, when a code is required after 5 years, what is my position?
I’ve provided alternate phone numbers and other information for recovery to all my mail accounts, including for hotmail. Is it sufficient?
I personally use 3 recovery emails in addition to my phone number for my important accounts. This way I’m protected in case I lose one of my recovery accounts or am in an area where I can’t get phone verification. As for product keys and codes, I have an envelope at home where I keep them all. In addition I keep them encrypted in a DropBox folder and backed up on my external hard drive and additional cloud storage. Overkill? Maybe, but it’s simple and inexpensive and more than worth the effort.
Recovery my fb account
I can,t get into my facebook page on my new mobile phone..I have tried all my passwords it won,t take any of them.. Badly disappointed…
sir how can i recover my lost account and password pls help me:(:(
Another excellent article, thanks Leo!
I have a question, before I set this all up.
My ISP provides us with multiple email addresses. Is it safe to use one of the other addresses as an alternate for each of the addresses we use, or do we need addresses from totally different entity?
It should be OK to use your ISP’s email address as a recovery address. I personally have four email addresses and three phone numbers for recovery. The more the merrier.
This recovery code is in addition to all that. You should be able to use this Recovery Code anywhere in the world even if your phones don’t work and you’ve lost access to your recovery email addresses. I have mine in an encrypted Dropbox folder which I can access from anywhere. If you uses that, don’t forget that password.
I’m thinking that people who don’t see that gear icon…..and I’m one of them….will just stop right there, thinking this isn’t for them. I’m not sure where that gear icon is, myself, so I stopped right there.
Dell, I believe that you will see the “gear” only after you have logged into Outlook.com with your Microsoft/Live/Outlook/etc account.
I’m confused. You imply that you are using Outlook.com and yet you have no gear icon?
Most interesting and I definitely will get that recovery code thanks Leo. A question on the subject of getting from both Hotmail and Gmail messages that they noticed unusual activities and therefore block access to the account. This happens when I use a VPN such as Hotspot, how can I avoid getting those messages? Its always a lot of time loss to get through their procedures. Maybe you have a solution?
I have no solution. The problem that Hotmail and Gmail are battling is absolutely huge – account theft is rampant, it really is. These measures are their way of attempting to prevent that from happening.
Thank you for the directions. I now have a Recovery Code. I keep a list of all my accounts, sitenames, URLs, usernames, passwords ( 290 as of today) for work and home in an Excel spreadsheet. I change my passwords at least once a year. More for work because we have to every 4 months. The spreadsheet is encrypted with a serious password. I have a printout stored in my bankbox in case of my death or a disaster. What do you think?
Great article. I did generate a recovery code a while back. In fact, at some time I replaced it (generated a new one). I think I know which one is which. Is there any way to verify or test that I am using the right one? I only see a button to generate another new one.
No. You can only replace it.
Like Pablo, I can’t get to my account. Outlook.com does not recognize my email and/or my administrator password and the gear icon does not give me any of the options in your description.
It’s not your administrator password it wants – you login to outlook.com with your outlook.com email address and your outlook.com password.
I followed your instructions where I was eventually taken to a page that said
Help us protect your account.
Before you can access sensitive info, you need to verify your identity with a security code. How would you like to receive your code?
To verify that this is your email address, complete the hidden part and click “Send code” to receive your code.
I entered the ***** part and was told “That doesn’t match the alternate email associated with your account. The correct email starts with “rj”. Clearly, one portion of the instructions says to enter only the hidden (*****) part and the other says to enter “rj” PLUS the hidden part. I find this typical of Microsoft. Details are often not checked leading to errors and confusion. As a former computer professional I know that if you haven’t verified that a process works (especially a recovery process) then you don’t have a recovery process. In this case this was a mistake that was easily correccted, but this type of error should never have made it to a production (online) environment. Microsoft has once again dropped the (very important) ball.
I have not used my Hotmail account in ages and don’t plan to. It’s not clear what other uses this recovery code is good for. Please illuminate me.
None… and it also would be of no use to someone who does not have a Hotmail (outlook.com) account.
Any Microsoft service for which you use that Hotmail address to login to. If you don’t use any, then you don’t need it.
Following your route does NOT take me to where I can set a RECOVERY CODE.
It takes me to where if necessary I would enter a SECURITY CODE which I know from bitter personal experience, many times, is discontinued in a very short space of time —– so quickly that it has often expired before I can enter it into my Tablet, so I have had to repeat the exercise several times until with luck I manage to beat the system and enter it before it expires!
So, given that I end up in a different place to the one you describe, where do I find the RECOVERY CODE page? I will start doing a search for it now!
The security code is a step on the way. In other words if you are asked for it you need to enter it before your proceed. This confirms that you are the authorized account owner. Once you enter the security code you’ll be taken to the correct place.
I like this idea and will try again later, but the first three attempts failed. It wants to pair with a smart phone, and believe it or not, some of us don’t have one. It might not work with an old flip p;hone, at least I can’t get it to work.
I have just had a long and fruitless Chat with a Microsoft advisor who insisted there was no such thing as a Recovery code —- he kept confusing it with the Product ID and then with activation and then the very temporary Security Code (which I have used many times when resetting my Microsoft account password>. Here is a directly copied quote:
‘Recovery key and product key is the same.
Actually no such thing recovery key, we from Microsoft called it as Product key.
You seeking help where you can find a recovery or product to store for future use.’ And so on. I thought you might be interested.
Since Microsoft doesn’t offer support for their email accounts, he wouldn’t be expected to give any advice on it. Therefore there’s no reason for him to know about it.
They seem to have accounts and products confused. There’s no such thing as a recovery code for a product (like Windows or Office). Make sure they understand that you’re talking about an outlook.com account.
I’m assuming that this is not the thing to do if you are using WIN XP SP 3 32 bit.
Also, I am using it on an aged desktop computer, no gearbox anywhere for me, except on Firefox….no-one mentioned a Browser, so I guess that isn’t the one you are talking about,
In Microsoft Office Outlook I did find a button that asked, “do I want a Digital ID?’
It appears this is so one can sign documents by proving who you are?
My question is, is this for me or not? and if not, why not? and, if not is there an alternative?
Good idea, great article….but mightily confused, as usual…(sorry, novice here).
Peace & Love
Sylvia
This should work on any OS including XP, MacOS, Linux or any phone or tablet OS. This is all done on the website and has nothing to do with which OS or browser you use.
Unless you know what a digital ID is, you probably don’t need one. You would need to send a copy of the public key to your recipients for them to verify your digital signature.
Microsoft Office Outlook is in no way related to Outlook.com. This article is all about your Microsoft account accessed via Outlook.com. What OS you are using has no bearing – if you have a Microsoft account online it applies.
Thanks for that, Leo. The only slight problem I had with following your instructions was that I couldn’t find a “More security settings” link. However in the same place was “Managed advanced security”, which took me to the right page.
This was extremely helpful. Hotmail/MSN/Outlook did not, to the best of my knowledge, have this in their help area. Yea! I will be able to access email while traveling. Thanks Leo.
My question is when they wanted me to verify my identity with a security code. They wanted to know how to send my code and it wanted me to fill in my email address to get the code. My problem is I tried this several times but I never get a code to my email. How can I get a code when it doesn’t come to my email?
Was it an email address you entered as a recovery address? Otherwise they wouldn’t be able to send it. If they sent it to addresses not registered with that account, a hacker could steal the account.
ok; I got my code; but I’m confused about this. I use outlook on my computer without ever logging into anywhere. I use RCN for my computer access (high speed cable modem; it’s like Comcast; but a competitor in my area) and so I think my emails come through the RCN server technically and arrive into my outlook inbox.
so would this article apply to me? or is this only if you log in and use outlook ‘in the cloud’? I’m so confused (insert googly eyes here which I don’t know how to do) : )
Outlook – the program from Microsoft Office that runs on your PC – is not not not the same as outlook.com. Your Microsoft account is an email account that uses a Microsoft domain like @hotmail.com, @live.com, @msn.com and so on, or a different email account that you have somehow registered with Microsoft as your Microsoft account to access Microsoft online services.
oh! LOL; I guess that’s why we pay you the big bucks ; )
I’m back at outlook 101.
Check your spam folder.
Leo, You said to get a recovery code for my Microsoft account after you said to get it for Hotmail or Outlook which you then stated are Microsoft accounts.
I’m confused once again.
Sounds like you want EVERYONE with a Windows machine to do this recovery code thing.
But, I don’t use Hotmail or Outlook. I use Windows Live Mail which is also a Microsoft product (I think)
So are you saying that I should be able to find my way to getting this code with WLM or what because I can’t figure out how to do that with your instructions.
Outlook.com, Hotmail, msn.com and Live.com accounts are all Microsoft accounts. They’re all accessed through the outlook.com webmail interface. All of them should be able to be protected with a recovery code in the same manner as described in the article. This wouldn’t work with other email service providers (ESP) on a Windows machine unless that ESP provided a similar service.
Other Microsoft type accounts that I use and need a recovery code are: Office 365 and OneDrive. I think the one Microsoft account (login.live.com) that uses my email as account number, covers all my subaccounts and subscriptions. And I think the one recovery code I acquired will work with all of them. My only problem is finding out how to verify the recovery code I wrote down was the most current. I can’t find a verify button.
There is no verify. You can only create a new one and replace your old one. If you login to all those other services with the same email and password, then they are all the same, single, Microsoft account and the one recovery code would apply.
Your machine login is not neccesarily a online account and it is not a “microsoft” account. Those accounts are local to your machine.
If you have an email address with Microsoft – like @hotmail.com or @live.com or @msn.com or you have registered your other email address with a Microsoft online service then those are Microsoft accounts.
Microsoft has further confused this with Windows 8 and on which allows you to set up your local machine so that you can login to it using your online account. Unless you login to your PC with an email address then this is NOT you.
Leo, this inspired me to create a recovery code. Problem is, my screen looks nothing like your screen captures. I have windows 8.1 and there is no gear icon. There is, on the dropdown under my login name, a list of options for Profile, Order History, Return History, Digital Content, and Payment, plus an item that says “looking for Microsoft Account Settings?” and when I click that it takes me to generic support for Windows. Not very helpful. I poked around and see no links for security. The Profile link only allows me to edit my name and email address.
Can you confirm that you are a) logged into Outlook.com, and b) looking at the outlook.com inbox when you don’t see a gear icon?
I use W8.1 and the Mail App does not have the gear icon. Like all such apps, the user is restricted as to what they can configure. The use of a browser on the desktop, not the ‘modern’ interface, should access outlook.com and show the gear icon.
My wife’s hotmail was blocked when we went on holiday to France from our UK home (both in EU countries). I used the Recovery Code issued by Microsoft last year – but it failed! I have eventually managed, after spending 3 days of our holiday, to get it working again. But this is so unnecessary and may be considered as being illegal as in the EU we have unrestricted movement across border within the EU, same as US citizens do between states.
I gather that the way the MS system works is to use a list of recognised devices for your account – but how do we add a new device to that list?
Likewise, it seems they use the IP address to determine which country you’re in and perhaps a rough location too (rough because that can be several hundred miles out if the ISP uses a randomised list as some do). Seems like a typical MS approach by not securing the real problem but making users life unnecessarily frought just because they take a holiday!
I don’t believe companies are required to give that kind of access between countries in the EU. This is a security issue for MS, and they even sometimes block access in different areas in the US. I have half a dozen recovery emails for my Hotmail account. Not that I need so many, but I usually add another one when I need to give instructions to people on how to do it, so I take the opportunity to add a new address each time :). One tip is to use an alternative email address which doesn’t have that kind of security in place as you can lock yourself into a verification loop when your alternate email provider send your verification code to your Hotmail address :(.
On my Windows 8.1 laptop, there is a Microsoft Store app that wants a MS account to be setup in order to down;load any app on the store.
Does this code recovery article apply to that account as well?
That is a Microsoft account, so yes this article applies.
When I logged in to set up a Recovery Code a message unexpectedly indicated my Microsoft account was “temporarily blocked” (no idea why b/c I’ve never had a problem with the account or access to it). So I opted to get a reset code by text to my phone. Nothing had arrived after 5 minutes so I tried again. After another 5 minutes I opted to have them call me (a robo call, I assume) with the code. But the MS site indicated that exceeded my allowed number of attempts (apparently just two). Moments later two texts arrived in quick succession, with two different codes. Figuring the last one was still good I went back to log in but found there is no way to get to the enter code page without going through the text/phone call routne which, of course, it refused to allow. Grrrr! For anyone in the same blocked status just be patient after requesting a code…wait ’till Miami freezes over if that’s how long it takes. Good luck setting up a Recovery Code.
I followed your directions and found that I already had a recovery code, since it said “replace” (when I got to that spot). News to me…!! Anyways, I am confused after reading all the comments above. What are all these “accounts” and “emails” – Hotmail, live, outlook, msn, etc.. I see that they are all Microsoft accounts, but I thought I only had the emails that I normally use – the one that I get my internet service from, and (2) free accounts, used for different purposes.
OK, so then I went to outlook.com and 2 of those accounts are listed on the left and the emails in the inbox are so old, they’ve long been deleted from the actual account from which they came… Can you explain this system and how it works? Thanks!
One other question – what apps need passwords? I got the following in an email just now and I don’t understand what to do – maybe I don’t use any apps?
“App passwords need to be updated
You changed your password recently. Since you turned on two-step verification for the Microsoft account ( deleted ), you need to create new app passwords for any apps or devices that don’t support two-step verification. Any existing app passwords will no longer work. “
Not sure, but it sounds like you turned on two-step verification for your email account. If you pick up that email using a phone or table, even a computer, then those are probably the apps the message is telling you about.
You apparently have two-step verification turned on. App passwords are used when you have a specific app (or application) that needs a password but can’t do two-step. An example might be a desktop email program.
WHEN I DID THE PROCEDURE DESCRIBED IN THIS TUTORIAL OUTLOOK ASK MY PHONE NUMBER AND SEND A 4 NUMBER CODE VIA SMS TO VERIFY MY ACCOUNT MY QUESTION IS HOW DOES I SKIP IT OR IF I KEEP THIS CODE COULD HELP ME TO RECUPERATE MY ACCOUNT.
You don’t skip it – it’s an important part of confirming you are the rightful account owner.
help my mail outlook sending code by this phone number
It’s not good to post phone numbers or email address in a public forum. Though this may not seem on topic, it would be helpful to read this article: https://askleo.com/internet_safety_8_steps_to_keeping_your_computer_safe_on_the_internet/
One thing to add, follow the instructions as Leo put it. Don’t choose to save the key on Microsoft’s servers, this weakens the provided security. If Microsoft’s servers were to become cracked, the thief would have hundreds of millions, if not billions, of user’s credentials, as some users has more than one Microsoft Account.
This is another reason why I use a Local account on Windows 8.1 & don’t bother with 10 at all. Rather, I run Linux MInt as my primary OS & that’s where I perform transactions, check emails, etc.
There is no longer an “account details” under Options to click on, and the screen shots are no longer accurate. I don’t know how to insert a screenshot of what I’m seeing here. I get locked out every year when I travel to Europe, and I don’t have a cell phone over there to have a code texted to, so this is a huge annoyance every year, so I’d really like to get a security code before I leave this year.
Companies constantly change their web interface – but it’s still helpful to know what to look for, often takes a bit more looking to find it
When I got down to putting in my other email acct for recovery & clicked send code nothing happened. Did it several times & nada?
What now?
Unfortunately, this doesn’t work anymore. Microsoft has removed much of this functionality. I was only able to create the code on my ‘old interface’ Live account. I couldn’t do it on my ‘new interface’ Outlook account. When it came time to use the code, it wasn’t accepted.
It might be time to archive this one!
I just checked, and I was able to get a new recovery code from outlook.com for my Hotmail account.
Yes, I know– I was able to make one, too. And then when I was overseas and locked out, it wouldn’t accept the code. Try to use the code and see if it works.
Will the security code help when I can’t access my hotmail because I am traveling? This happens even in the US. I set up my account so long ago that I am apparently unable to answer enough of their security questions to satisfy them (and I answered a LOT!) Can someone let me know if this works for when I’m traveling and using a computer other than my own? Thanks!
It should. That’s one of the things it’s designed for. It’s also a good idea to have more than one recovery email as those can also get you in when you travel. A good alternate email address is with a company like gmx.com (gmx.de/at or ch in Europe). They don’t require second factor authentication when you travel.
Thanks Mark, I appreciate it, will definitely set up the security code.
Hi. My Outlook email address is:
1. My last sent email subjects (4 nos.)______I hardly can remember the exact email subject of my recently send emails as my last sent email maybe about 20 days ago. But still some of them I managed to get from the receivers I sent before.
2. Additional folders I created so far (4 nos.)_____So far I didn’t created any additional folders.
3. Passwords I used so far (4 nos.)_____I’m using this password for about 10 years now, so I can’t remember others.
4. Country/Region: I opened this account at Bangladesh and later I moved to Singapore 4 years ago. I don’t know which one they are asking for.
5. Postal Code: I changed my apartment several times. So I don’t know which one they are asking for. It should be among them (120346, 120340, 120326)
6. Credit Card Information: So far I used 2 credit cards so I don’t know which one they are asking for. But I have both credit cards information.
Please let me know how I can recover my account now.
Thanks
You may not be able to. This simply underscores the importance of backing up your account contents, and keeping recovery information up to date always. Sorry I don’t have better news for you.
None of the above even exists. There is no managing my account option. It is now 2016. Is this option even available anymore?
Yes. On my Microsoft account I still see the Gear, and options, and Account Details. It looks mostly the same. So try again.
“If you previously had a recovery code, it is no longer valid”
If someone hacks my account, and changes the code, won’t this render my recovery code useless?
Yes. This is one reason that recovering your account quickly is important, and one reason that recovery codes are only a part of your overall security.
Good write up. And still viable.
To avoid confusion though you might want to update the document, as is often the case, documentation about websites is a moving target. Microsoft has changed the page layout, so the screen captures in this document no longer match their site.
I *just* updated this last week.
thanks Leo, I have finally generated a recovery code from Microsoft. None of the options you mentioned came up; it took a half hour chat with a microsoft chap to help me out and get me that code. I have two step verification, but as part of it was my phone no it didn’t seem the best security! But I’ve got the verification code now, written down in a safe place, so lest the worst happens, I have it. Thanks again Leo.
JD
Leo. I followed the steps. The windows matched those in your article (I’m on 8.1) and the process worked without a hitch. Thank you
I’ve printed the code, and I will store one copy in my filing cabinet, and another copy with my out-of-house backup (in a plastic bag in a box in the garage, down the bottom of the garden – safe if the house burns down).
Расшифровка меню recovery на андроид
Recovery Mode (режим восстановления) — специальный режим загрузки аппарата, который позволяет делать сброс до заводских настроек, бэкапы и другие системные действия.
Чаще всего его используют для полного сброса, когда нет доступа к стандартным настройкам системы. Процедура входа в Recovery разная для каждого производителя. Например, на смартфонах Samsung нужно зажать «кнопка питания + Home + качелька регулировки громкости вверх». На Nexus-устройствах — «кнопка включения + регулировки громкости вниз». Управление в самом рекавери осуществляется с помощью кнопок регулировки громкости и кнопки питания.
Внимание! Открытие Recovery не является опасной процедурой и не лишает пользователя гарантии, но дальнейшие действия могут привести к разным последствиям, ответственность за которые несете исключительно вы.
Есть несколько видов режима восстановления: стоковое и кастомное. Рассмотрим их более подробно.
Стоковое
Стоковый Recovery Mode идет вместе с устройством изначально и не отличается особой функциональностью. В большинстве случаев в нем присутствуют следующие пункты:
Во многих смартфонах на Android 7.0 Nougat в меню Recovery появились и такие функции:
Кастомное
Кастомное рекавери включает гораздо большее количество функций. Чаще всего его используют для установки сторонних прошивок и создания образа восстановления системы (nandroid backup), также есть возможность сделать вайп (очистить) отдельные разделы, например, data, dalvik cache, вернуть телефон в исходное состояние без потери данных, восстановить права системных приложений и так далее. Самыми популярными являются CWM и TWRP.
Мобильные устройства уже довольно плотно вошли в нашу жизнь. Теперь человек не представляет себе существования без смартфона или планшета. Огромной популярностью пользуются устройства на базе операционной системы “Андроид”. Эта ОС была разработана компанией Google, и сейчас ее доля на рынке невероятно высока. У iOS от Apple и Windows Phone ничтожный процент присутствия на мобильных рынках по сравнению с “Андроид”. Однако, как и вся техника, устройства на этой платформе имеют свойство “глючить”. Различные системные сбои – отличительная черта любой операционной системы. Какой бы продвинутой она ни была. Очень часто девайсы приходится перепрошивать. Но не все знают, что можно обойтись и без столь радикальных мер. Ведь в любом гаджете на “Андроид” есть Android System Recovery 3e. Как пользоваться им и что это вообще такое? Об этом мы и поговорим.
Что это за зверь?
Что означает Android System Recovery 3e? Это своеобразный БИОС мобильного устройства. Любая операционная система имеет свой БИОС – базовую систему ввода-вывода, которая способна работать даже при повреждении основной ОС. Иногда БИОС непохож на стандартный (как, например, в девайсах на “Андроид”). Он служит для того, чтобы восстановить работоспособность смартфона или планшета, применить критические обновления или сделать сброс на заводские настройки. Меню Android System Recovery 3e имеет множество пунктов, которым соответствует то или иное действие. Но беда в том, что названия написаны на английском языке. Поэтому многие и знать не знают, как правильно пользоваться рекавери.
Именно поэтому написана эта статья. Android System Recovery, инструкция к которому совершенно необходима, является мощным инструментом для настройки и реанимации смартфона. Нужно все знать о том, как пользоваться этим рекавери для того, чтобы не тратить деньги на мастеров. Сделать все самому куда проще и дешевле. Мы разберем каждый пункт меню рекавери и расскажем о нем все, что только можно. Итак, начинаем.
Как войти в рекавери?
Это зависит от конкретной модели устройства. В некоторых аппаратах нужно зажать кнопку включения и клавишу “Громкость +”. Но иногда встречаются смартфоны, которым этого недостаточно. Старые модели с механической кнопкой “Домой” требуют нажатия и этой кнопки. Некоторые девайсы требуют одновременного нажатия кнопок включения и “Громкость”. Есть и такие, которым обязательно зажатие клавиши включения и обеих кнопок регулирования громкости. Это касается только оригинальных устройств от известных производителей.
Но есть также и откровенно “китайские” гаджеты с непонятной операционной системой и “кривым” переводом. Стандартные методы входа в рекавери в этих случаях могут и не сработать. Здесь есть несколько вариантов. Первый: изучить документацию смартфона (если она имеется) и найти искомую комбинацию клавиш. Но этот вариант подойдет далеко не всем. У большинства таких устройств либо нет вообще никаких документов, либо в документах вообще нет русского языка. Второй вариант: найти нужную комбинацию путем поочередного нажатия всех кнопок. А теперь перейдем к пунктам меню Android System Recovery 3e.
Reboot system now
Этот пункт меню выполняет полную перезагрузку устройства. После выбора этой опции смартфон загрузит стандартную операционную систему “Андроид” без всяких изменений. Обычно этот пункт используют по завершении всех манипуляций в рекавери. Или же в том случае, если загрузились в этот режим случайно. Хотя, как это сделать можно случайно – неизвестно. Как бы то ни было, Android System Recovery 3e, инструкция по эксплуатации которого просто жизненно необходима пользователю, имеет такой пункт. И с этим приходится считаться.
Пункт меню Reboot system now нужно использовать в самую последнюю очередь. То есть тогда, когда все операции выполнены, все компоненты обновлены, заводские настройки сброшены и прошивки установлены. В этом и есть суть перезагрузки: дать устройству применить все сделанные изменения. Правда, после некоторых из них смартфон может вообще не загрузиться. Но это уже совсем другая история.
Apply Update from External Storage
Этот пункт меню позволяет применить обновление, которое находится на карте памяти. Кстати, через этот пункт устанавливают и новые прошивки в том случае, если основная ОС не грузится. Есть несколько подпунктов в этом меню Android System Recovery 3e. Как прошить новую ОС? Для этого нужно зайти в данное меню и выбрать пункт Choose ZIP from SD Card, если прошивка в формате ZIP. Если же это просто файл обновления, то следует выбрать Apply Update From SD Card. Именно так прошивается любой аппарат с помощью рекавери. Достаточно просто скопировать файл прошивки в корень карты памяти, зайти в рекавери и выбрать нужный пункт.
В этом пункте есть и другие подпункты, которые применяются в нестандартных ситуациях. Есть возможность проверить MDSUM файла прошивки. Эта опция проверяет файл на целостность и если что-то не так, тут же выдает предупреждение. Также можно проверить файл прошивки на совместимость с устройством. Это информационные опции Android System Recovery 3e. Инструкции как таковой к ним не требуется. Если есть ошибки, то ставить данную прошивку не нужно. Вот и весь сказ.
Wipe Data. Factory Reset
Вот это очень важный пункт. Сия опция способна восстановить работоспособность аппарата без всяких прошивок. Этот инструмент сбрасывает операционную систему гаджета на заводские настройки. Естественно, все, что находилось на смартфоне будет удалено: приложения, фотографии, музыка. В общем, все то, что находилось во внутренней памяти телефона. Android System Recovery 3e, инструкция по эксплуатации которого здесь рассматривается, создан как раз для того, чтобы возродить аппарат без серьезного вмешательства в прошивку. И эта опция позволяет выполнить сию операцию.
Эта функция также используется перед установкой любой прошивки. Сбрасывать телефон на заводские настройки перед прошивкой необходимо. В противном случае новая операционная система будет работать нестабильно. Но это еще не самое худшее. Если не вернуться к заводским настройкам, то прошивка может вообще не установиться, и тогда пользователь получит совершенно “мертвый” смартфон. Инструкция на русском языке отсутствует, но та, что есть, ясно говорит, что использовать пункт Wipe Data & Factory Reset обязательно нужно перед каждой прошивкой устройства.
Wipe Cache Partition
Еще одна полезная команда в Android System Recovery 3e. Инструкция к рекавери говорит о том, что использовать эту опцию нужно в тандеме с Wipe Data. Если предыдущий пункт очищает внутреннюю память устройства, то этот очищает его кеш. А именно там хранятся рабочие файлы приложений. Конечно, если этого не сделать перед прошивкой, то ничего страшного не произойдет. Просто в дальнейшем, при установке новых программ, кеш устройства разрастется до неимоверных размеров. В результате чего смартфон будет очень медленно работать. Но это не так страшно, поскольку есть множество программ для чистки кеша ОС Андроид. И они прекрасно работают.
Также рекомендуется выбирать эту функцию после того, как был сделан сброс на заводские настройки. Это поможет смартфону стать еще “чище”, что положительно повлияет на работоспособность операционной системы. Инструкция на русском языке к Android System Recovery 3e рекомендует выполнять эту процедуру именно после сброса. До перезагрузки устройства. Тогда все будет так, как должно быть.
Wipe Battery Stats
Эта функция помогает обновить батарею устройства. После нажатия на этот пункт начинает очищаться кэш аккумулятора, в который записывается текущее состояние элемента питания, его номинальная емкость и прочие нужные параметры. Сбросив статистику использования аккумуляторной батареи, можно будет немного продлить ее жизнь. Да и новая прошивка будет работать с аккумулятором адекватнее. Почему-то многие “гуру” “Андроида” пренебрежительно относятся к этой опции. Но на самом деле она очень полезна. Однако применять ее слишком часто не рекомендуется. Только перед перепрошивкой устройства.
Mounts. Storage
Здесь находятся элементы управления внутренней и внешней памятью смартфона. Этот пункт позволяет очистить карту памяти или встроенную память, отформатировать ее или присоединить в качестве накопителя прямо из рекавери. Этот раздел может использоваться в том случае, если вы забыли скинуть на карту памяти файл прошивки, а перезагружать смартфон в операционную систему нет никакого желания. Для того, чтобы смонтировать карту памяти устройства в качестве накопителя нужно выбрать пункт Mount USB Storage. Как только соединение будет установлено, компьютер сам установит необходимые драйвера для работы.
После установки соединения можно делать с картой памяти все что угодно: форматировать, очищать, копировать нужные файлы и так далее. Для того чтобы размонтировать флешку, следует выбрать на экране смартфона в рекавери пункт Umount USB Storage. После этого можно будет переходить к другим пунктам рекавери и производить дальнейшую реанимацию устройства собственными силами.
Ошибки рекавери
Иногда возникает такая распространенная ошибка в Android System Recovery 3e, как отмена установки прошивки или пакета. Возникнуть она может по нескольким причинам: файл с прошивкой поврежден, неверная информация в бинарном файле или прошивка просто не подходит этому девайсу. Но есть и еще один вариант: перед прошивкой не был произведен сброс на заводские настройки. Хорошо, что их можно легко исправить в том же рекавери. Для этого существует несколько способов.
Итак, если ошибка возникает по вине битого файла прошивки, то следует перекачать ее, подключить смартфон к компьютеру, зайти в пункт меню Mount & Storage и выбрать Mount USB Storage. После этого можно заново копировать прошивку в корень карты памяти. Если вы забыли сделать “вайп”, то нет ничего проще, чем переместиться на несколько уровней выше и выбрать соответствующий пункт меню. А вот ошибка Android System Recovery 3e “Команды нет” встречается очень редко. Она появляется только тогда, когда пользователь пытается установить обновление по ADB. Обычно этот метод не работает. Вследствие чего и появляется сия ошибка. Так что использовать этот метод не имеет смысла. Все равно ничего не получится.
Заключение
Итак, подведем итоги. Мы попытались описать возможности Android System Recovery 3e. Инструкция, которая получилась в результате этой попытки, поможет начинающим пользователям операционной системы “Андроид” научиться восстанавливать работоспособность своего смартфона своими руками. Что в конечном итоге приведет к расширению кругозора и неплохой экономии денежных средств.
Help with the Microsoft account recovery form
We recommend following the steps in this order to assist you with resetting your Microsoft account password.




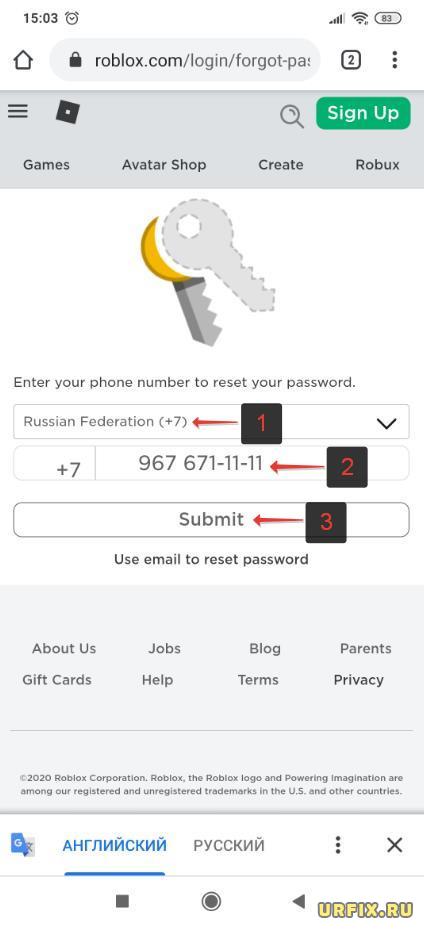
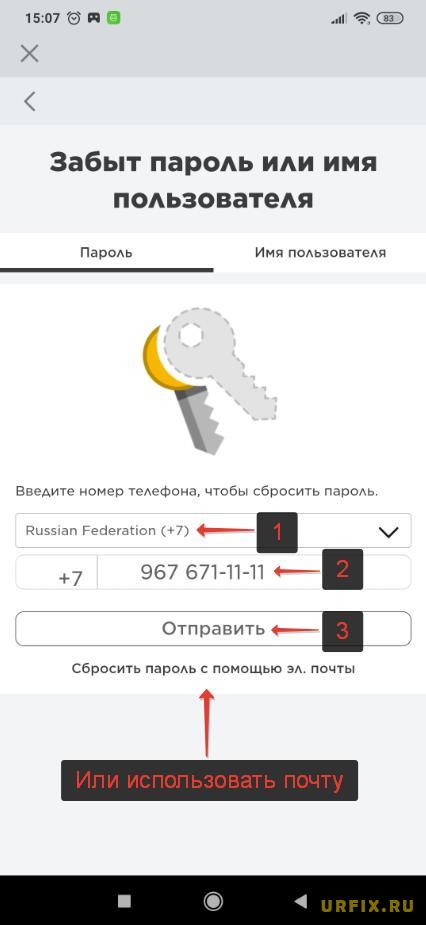















:max_bytes(150000):strip_icc()/Heinz-Tschabitsche-c6d01096ad5f47b8800846cebc7d99b1.jpg)
:max_bytes(150000):strip_icc()/WorkBadgePhoto-61c0b98ef5a74e4a85851a8f706dbd65.jpg)
:max_bytes(150000):strip_icc()/focused-college-student-studying-at-computer-485207563-59af2b10b501e8001181b6b1.jpg)
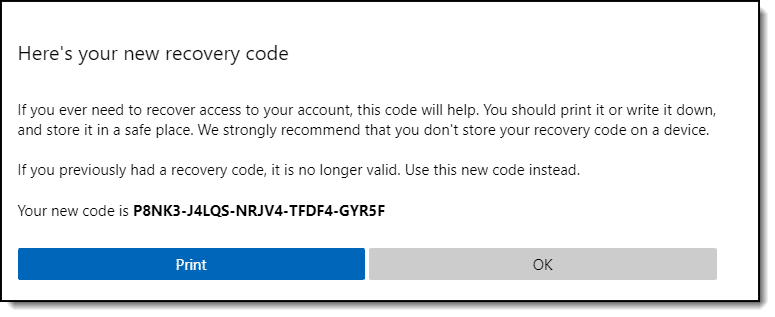


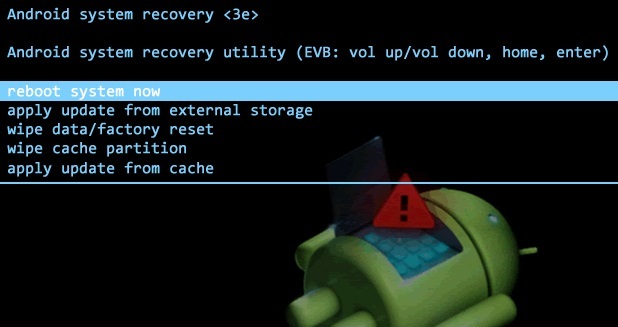




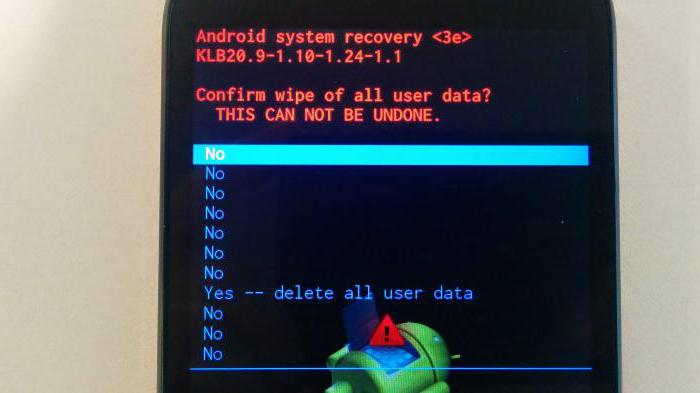
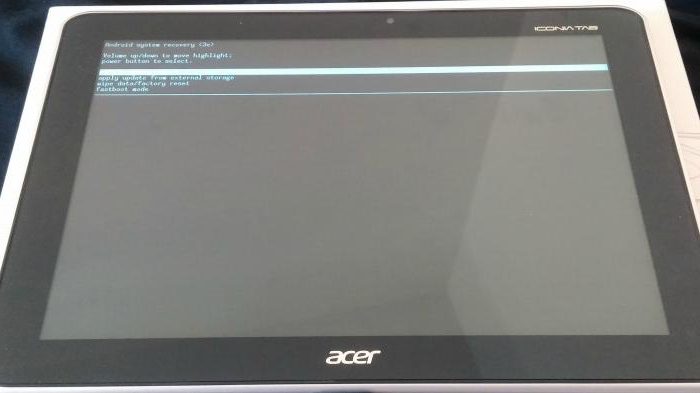










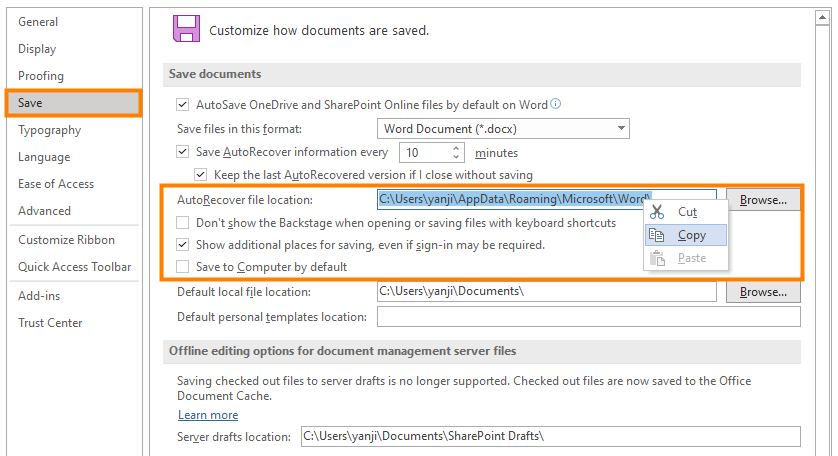
 Tip
Tip