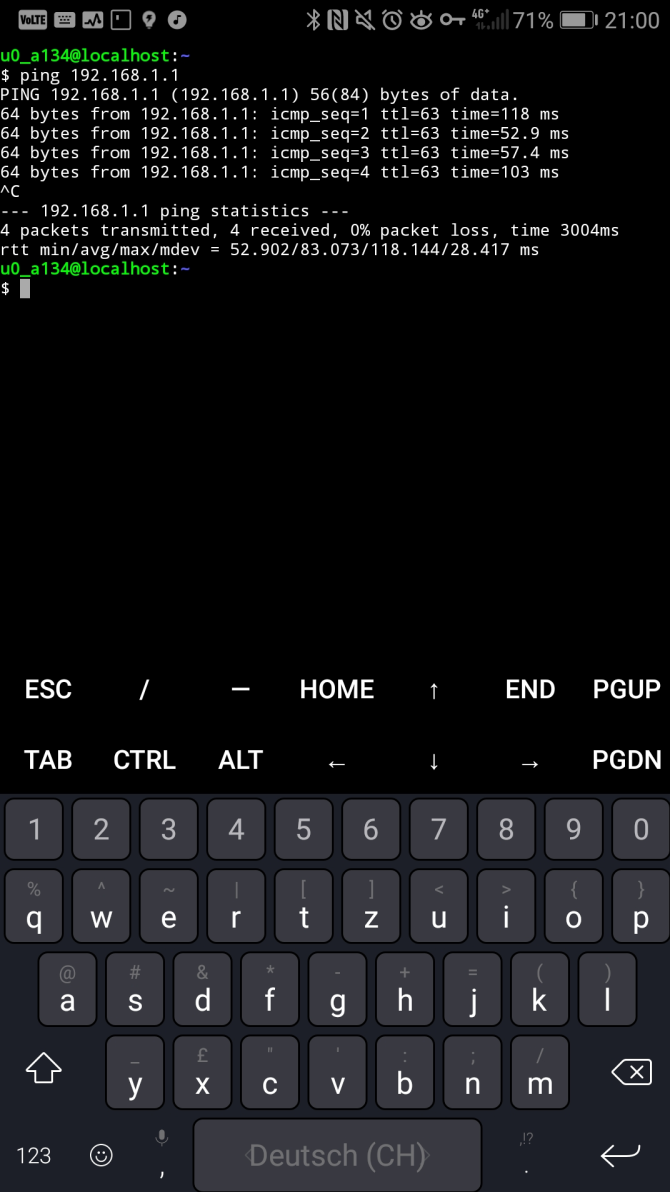
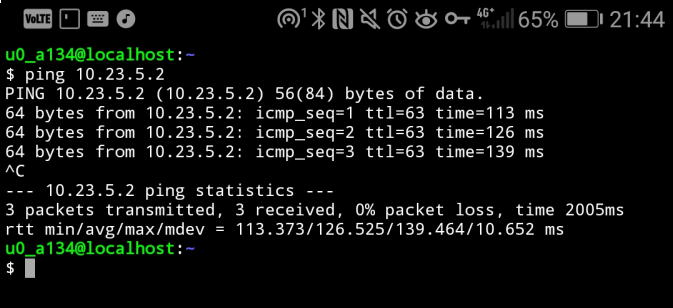
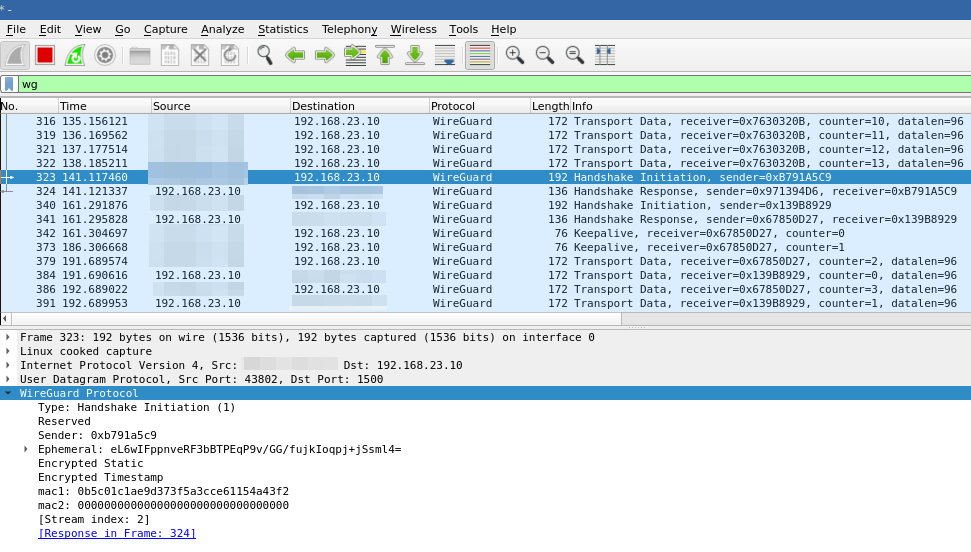
Wireguard qr code generate
Wireguard qr code generate
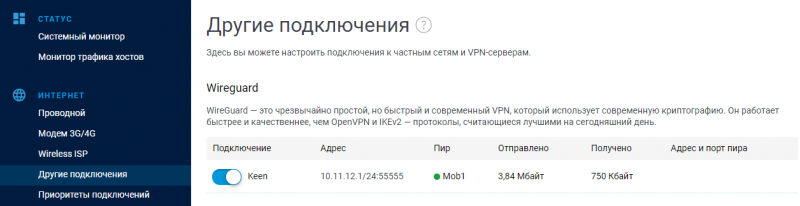
WireGuard + QR-code конфиг файла для мобильной версии клиента
0. для быстрой конфигурации
1. Установка WireGuard
установка простецкая, одна и та же, что на сервак, что на клиент: команды все от root
подготовим систему к форвардингу (делаем только на сервере)
исправим на след. параметры:
применим изменения «на лету»
2. Создание ключей для сервера и клиента и конфиг сервера
Генерация ключей сервера, приватного и публичного
Генерация ключей клиента, приватного и публичного
Настройка конфигурации сервера:
перед настройкой, узнайте имя интерфейса с публичным адресом, обычно eth0
вставим следующие строки:
3. Создание конфига клиента
Конфиг клиента практически похож на серверный:
Описание файла клиента:
4. Запуск сервера
Запуск сервера и клиента это по сути поднятие VPN туннеля
отразится информация о пирах и о объеме полученных данных.
Остановка сервера или клиента.
Создание автозапуска для поднятия соединения:
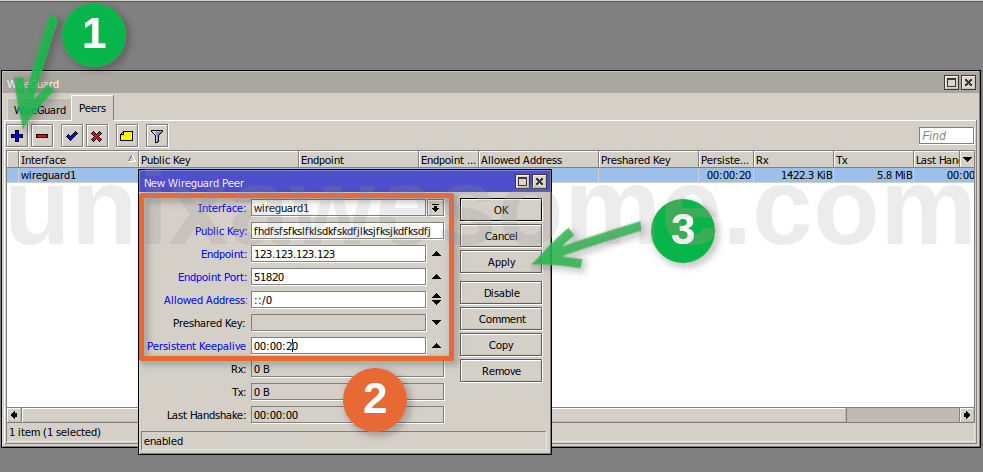
Создание QR кода для подключения клиентов WireGuard
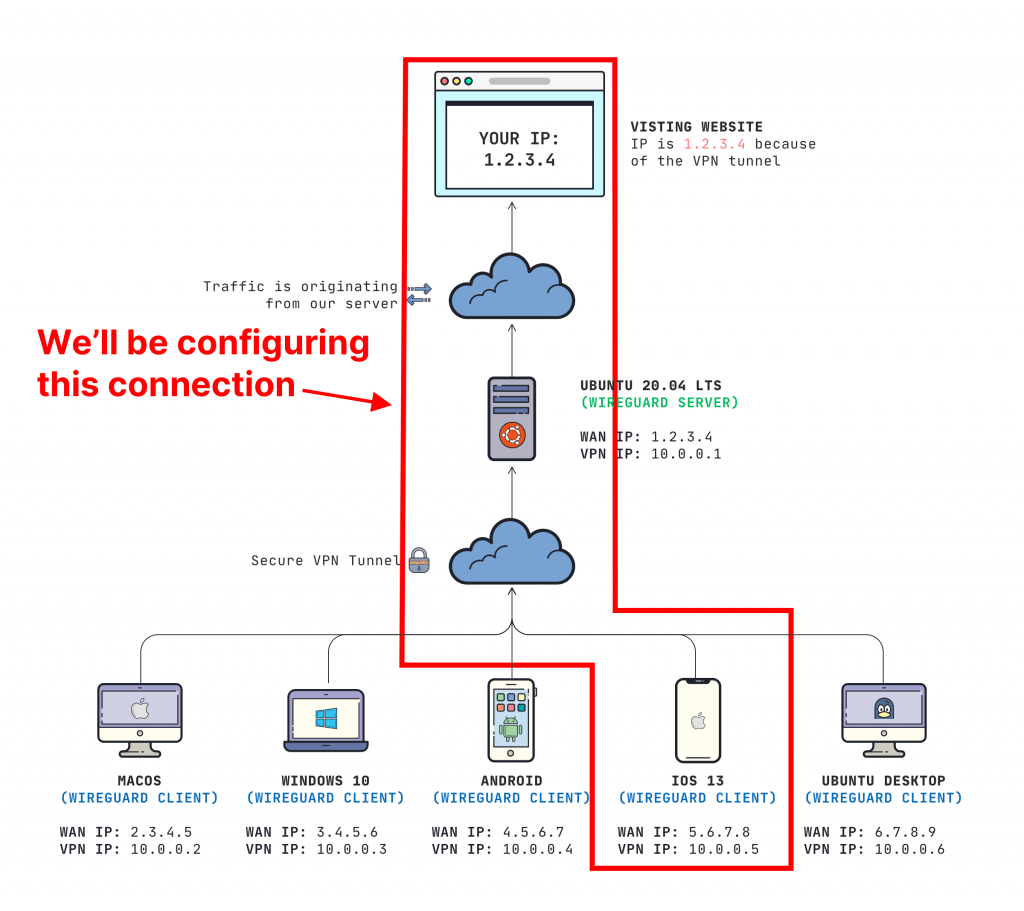
Для настройки подключения к WireGuard с мобильного телефона можно создать QR код с конфигурацией. В этом материале мы узнаем как это можно будет сделать.
Подключимся к нашему WireGuard серверу через ssh и выполним следующие действия.
Обновим список пакетов на установленной системе:
Теперь можно установить утилиту qrencode, которая и будет создавать нам QR коды:
Создадим тестовую конфигурацию для телефона example-client.conf. Выполним следующую команду:
Вставим в редактор приведенный ниже текст:
Для сохранения нажмем комбинацию клавиш Ctrl + O, а затем Ctrl + X, чтобы закрыть редактор.
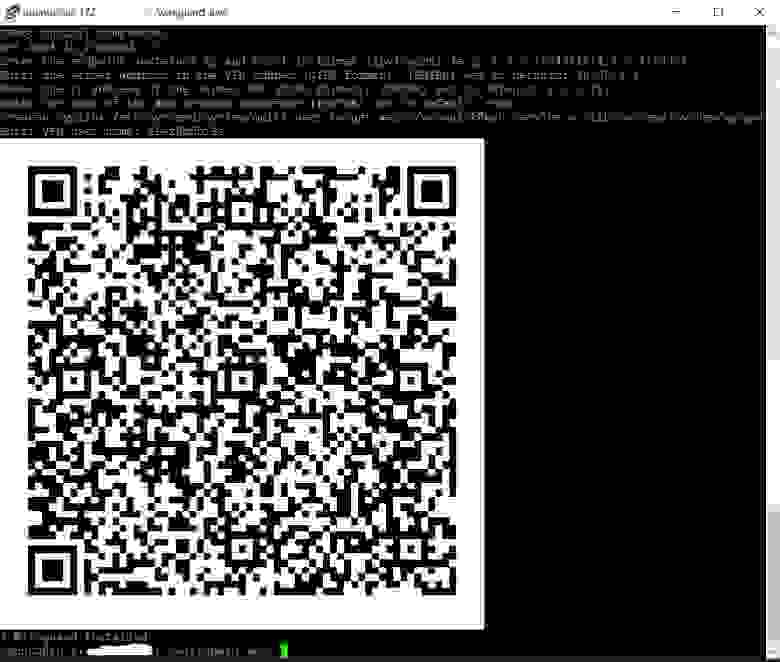
Теперь можно создать QR код на основе нашего конфига. Для этого выполним команду:
Используя параметры ––foreground и ––background можно задать цвета QR кода и его фона. Цвет задается в шестнадцатеричном виде. Например:
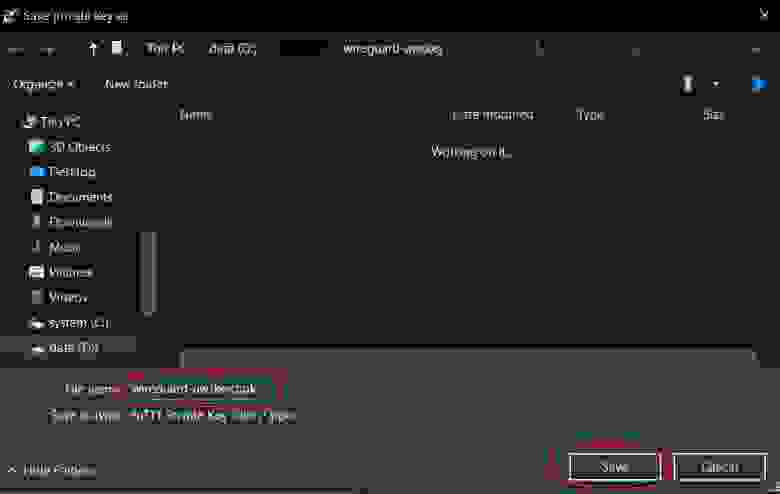
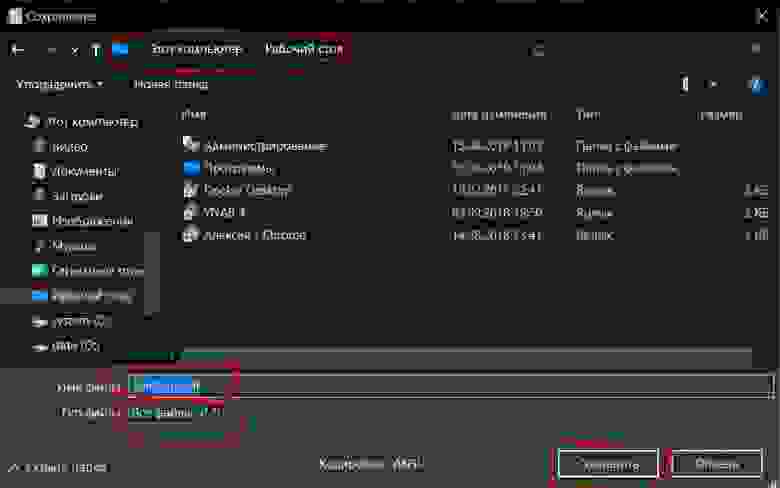
Теперь созданное изображение можно скачать с сервера и отправить клиенту. Чтобы скачать изображение можно воспользоваться утилитой scp входящей в Windows 10. Открываем PowerShell и вводим следующую команду:
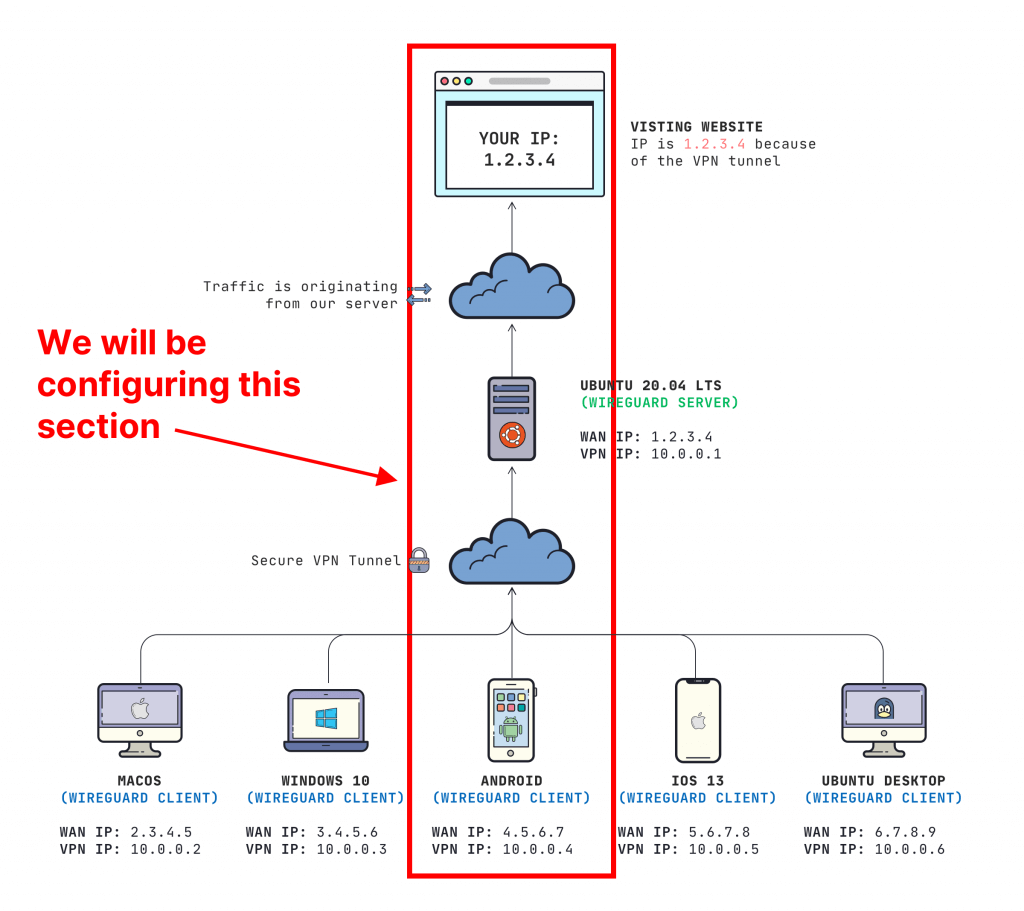
Настраиваем собственный сервер VPN WireGuard (с IPv4 и IPv6) для настольного компьютера и смартфона Android
14 Сентябрь, 2021 00:00 • Александр Котов
wireguard vpn блокировки технологии
Что такое WireGuard и почему именно он?
Судя по всему, блокировка пока осуществляется по IP-адресам серверов конкретных известных поставщиков услуг VPN или по протоколу, но далеко не на всех портах. Это нас пока не волнует, поскольку мы будем настраивать собственный сервер и сможем указать альтернативный порт. Данное решение может оказаться временным, но тогда философия WireGuard тоже сыграет нам на руку, потому что мы сможем пробросить трафик в другой, уже более скрытный тоннель, например TCP, Tor или Shadowsocks с опциональной обфускацией. Гибкость такого подхода позволит нам выбрать решение в зависимости от ситуации. Мы постараемся предоставить соответствующие инструкции позже, а пока перейдём к настройке сервера WireGuard.
Настраиваем сервер WireGuard
Для начала нужно разрешить пересылку пакетов IP. В файле /etc/sysctl.conf раскомментируем следующие строки (удалим символ # в начале строки):
Применим новую конфигурацию:
Установим WireGuard и другие нужные пакеты:
Далее мы создадим файлы ключей и конфигурации. В целях безопасности необходимо ограничить доступ к ним только для суперпользователя, поэтому установим маску текущей сессии командной оболочки:
Сгенерируем ключи для сервера и пары клиентов (в дальнейшем мы будем подключать к VPN домашний компьютер и смартфон):
Выведем на экран сгенерированные ключи:
После окончания настройки сервера и клиентов или сейчас, если вы не собираетесь очищать экран, эти файлы можно удалить:
Теперь включим и запустим сервис:
Настраиваем WireGuard на настольном компьютере
Здесь мы рассмотрим настройку WireGuard на настольном компьютере под управлением операционной системы Ubuntu 20.04 или подобной. Если вы используете другую операционную систему, то воспользуйтесь инструкциями из Интернета.
Повторим команды, которые мы уже использовали на сервере:
Если вы использовали графический текстовый редактор, то файл нужно защитить явно:
Теперь включим и запустим сервис:
Узнать свой IP-адрес можно следующей командой:
Он должен совпадать с IP-адресом вашего сервера.
Если на вашем сервере настроен IPv6, то у вас он тоже будет работать, даже если ваш поставщик услуг Интернета не поддерживает его:
Настраиваем WireGuard на смартфоне Android
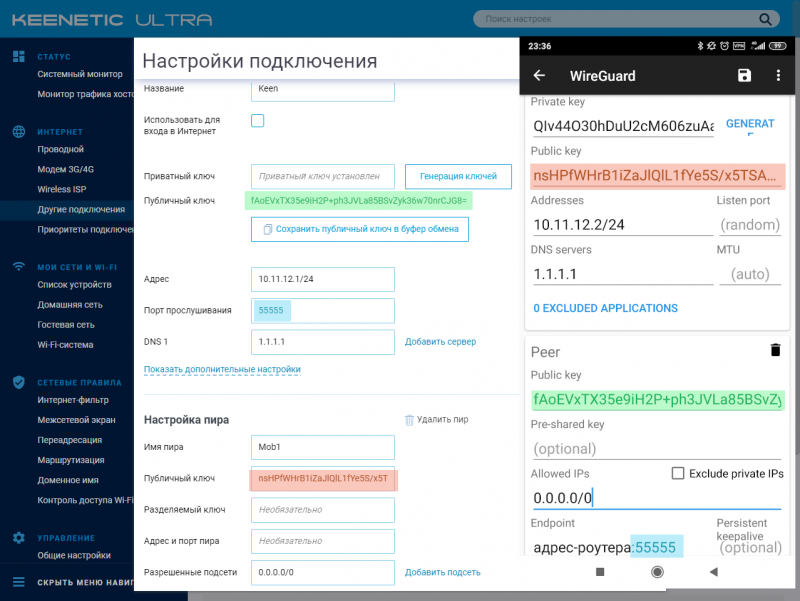
Интерфейс настройки повторяет структуру уже созданного нами ранее файла конфигурации для настольного компьютера, но мы всё-таки приведём пример заполнения полей. Опять же, нужно заменить ключи, IP-адрес и порт сервера на те, которые вы сгенерировали.
В секции “Interface”:
В секции “Peer” (нужно нажать кнопку “ADD PEER”):
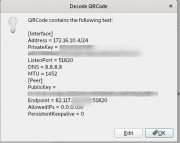
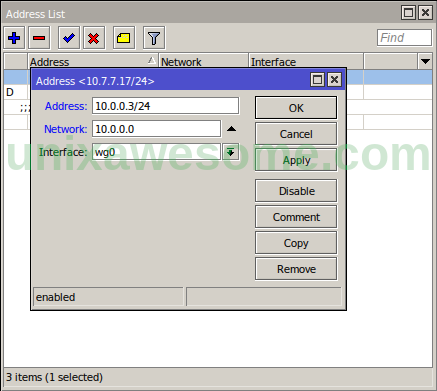
Также вы можете сгенерировать QR-код с вашей конфигурацией, который удобно считывать с помощью приложения WireGuard для смартфона. Для этого создайте где угодно файл конфигурации wg0.conf аналогичный тому, который мы создавали для настольного компьютера:
Теперь установить программу для генерации QR-кодов и запустите её:
Считайте этот QR-код с помощью приложения WireGuard для смартфона. Не забудьте после этого удалить файл конфигурации, так как он содержит ваш приватный ключ:
Безопасность
Теперь ваш VPN должен работать. Однако мы совсем не рассматривали вопросы безопасности.
Категорически важно обновить пакеты на вашем сервере и делать это регулярно (хотя бы раз в неделю):
Столь же важно включить аутентификацию в SSH по ключу вместо пароля или использовать очень длинный пароль (минимум 32 большие и маленькие цифры и буквы), а также сменить стандартный порт 22 на какой-нибудь другой (строка Port 22 в файле /etc/ssh/sshd_confg и команда sudo systemctl restart ssh.service для перезапуска).
Обычной практикой является использование сетевого экрана. В данном случае мы не видим в этом серьёзной необходимости, но всё-таки рекомендуем настроить его. Можно воспользоваться сетевым экраном вашего поставщика услуг VPS и самой операционной системы. Необходимо открыть порты SSH и WireGuard и запретить всё остальное. Следующие команды сохранят настройки и применят их даже после перезагрузки:
В большинстве других случаев также рекомендуются такие практики, как настройка Fail2ban для предотвращения множественных попыток подключения по SSH или включение доступа по SSH только после простукивания портов (англ. port knocking), настройка мониторинга и сбора журналов. Однако это выходит за рамки данной статьи.
Есть три основные опасности, которые может представлять для вас незащищённый сервер VPN в случае его взлома:
Мы не считаем эти опасности очень критичными. При следовании советам из данной статьи они менее вероятны, чем, например, взлом домашнего маршрутизатора (англ. router), за безопасностью которых редко кто следит, насмотря на риски. Так что мы считаем, что если вы смогли выполнить указанные здесь инструкции, то вы вполне можете пользоваться собственным сервером VPN и не беспокоиться. Однако мы всё-таки надеемся, что вы не остановитесь на прочтении данного материала и подробнее изучите работу сетей и операционных систем. Хотя бы потому, что в современных условиях это может вам пригодиться, чтобы просто не потерять доступ в Интернет.
pbengert/wireguard-config-generator
Use Git or checkout with SVN using the web URL.
Work fast with our official CLI. Learn more.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
wireguard config generator for python
Generate config files and qr codes for wireguard vpn
You will need to install qrcode and pillow in python and you need to install wireguard, so that you can call wg from your terminal
Edit your settings in the python file
About
Generate config files and qr codes for wireguard vpn
WireGuard
From the WireGuard project homepage:
WireGuard is an extremely simple yet fast and modern VPN that utilizes state-of-the-art cryptography. It aims to be faster, simpler, leaner, and more useful than IPsec, while avoiding the massive headache. It intends to be considerably more performant than OpenVPN. WireGuard is designed as a general purpose VPN for running on embedded interfaces and super computers alike, fit for many different circumstances. Initially released for the Linux kernel, it is now cross-platform (Windows, macOS, BSD, iOS, Android) and widely deployable.
A rough introduction to the main concepts used in this article can be found on WireGuard’s project homepage. WireGuard has been included in the Linux kernel since late 2019.
Contents
Installation
Install the wireguard-tools package for userspace utilities.
Alternatively, various network managers provide support for WireGuard, provided that peer keys are available. See #Persistent configuration for details.
Graphical clients
Usage

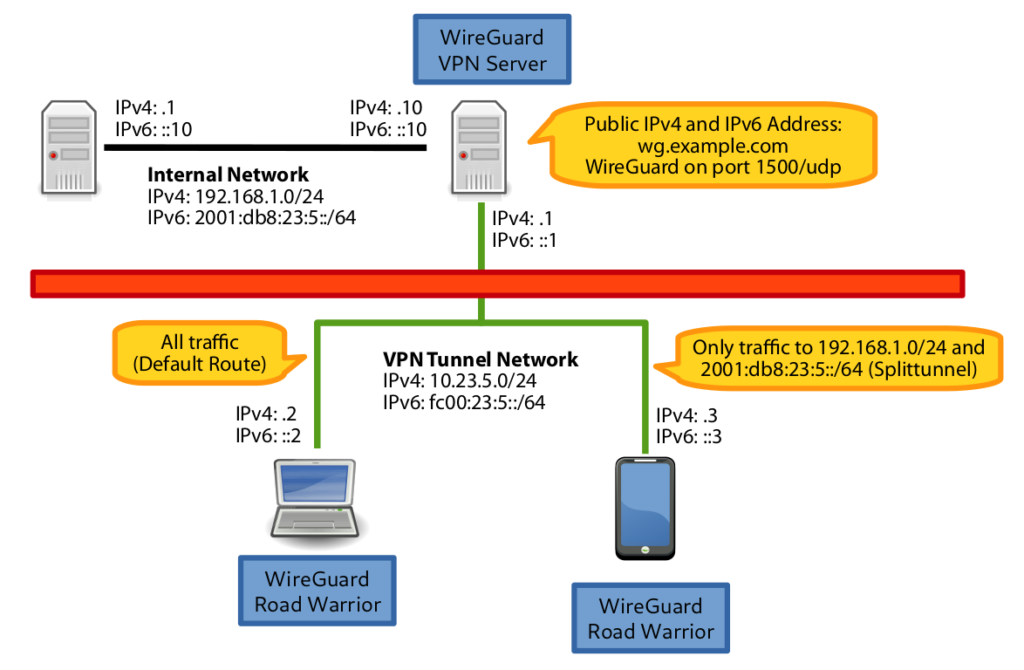
The commands below demonstrate how to set up a basic tunnel between two or more peers with the following settings:
| External (public) addresses | Internal IP addresses | Port | ||||
|---|---|---|---|---|---|---|
| Domain name | IPv4 address | IPv6 address | IPv4 address | IPv6 address | ||
| Peer A | 198.51.100.101 | 2001:db8:a85b:70a:ffd4:ec1b:4650:a001 | 10.0.0.1/24 | fdc9:281f:04d7:9ee9::1/64 | UDP/51871 | |
| Peer B | peer-b.example | 203.0.113.102 | 2001:db8:40f0:147a:80ad:3e88:f8e9:b002 | 10.0.0.2/24 | fdc9:281f:04d7:9ee9::2/64 | UDP/51902 |
| Peer C | dynamic | dynamic | 10.0.0.3/24 | fdc9:281f:04d7:9ee9::3/64 | UDP/51993 | |
The external addresses should already exist. For example, if ICMP echo requests are not blocked, peer A should be able to ping peer B via its public IP address(es) and vice versa.
The internal addresses will be new addresses, created either manually using the ip(8) utility or by network management software, which will be used internally within the new WireGuard network. The following examples will use 10.0.0.0/24 and fdc9:281f:04d7:9ee9::/64 as the internal network. The /24 and /64 in the IP addresses is the CIDR.
Key generation
Create a private and public key for each peer. If connecting dozens of peers optionally consider a vanity keypair to personalize the Base64 encoded public key string. See #Vanity keys.
To create a private key run:
To create a public key:
Alternatively, do this all at once:
One can also generate a pre-shared key to add an additional layer of symmetric-key cryptography to be mixed into the already existing public-key cryptography, for post-quantum resistance. A pre-shared key should be generated for each peer pair and should not be reused. For example, three interconnected peers, A, B, and, C will need three separate pre-shared keys, one for each peer pair.
Generate a pre-shared key for each peer pair using the following command (make sure to use umask 0077 for this as well):
Vanity keys
Currently, WireGuard does not support comments or attaching human-memorable names to keys. This makes identifying the key’s owner difficult particularly when multiple keys are in use. One solution is to generate a public key that contains some familiar characters (perhaps the first few letters of the owner’s name or of the hostname etc.), wireguard-vanity-address AUR does this.
Manual configuration
Peer setup

In this example peer A will listen on UDP port 51871 and will accept connection from peer B and C.
The keyword allowed-ips is a list of addresses that will get routed to the peer. Make sure to specify at least one address range that contains the WireGuard connection’s internal IP address(es).
Additional routes
To establish connections more complicated than point-to-point, additional setup is necessary.

Point-to-site
Site-to-point

If the intent is to connect a device to a network with WireGuard peer(s), set up routes on each device so they know that the peer(s) are reachable via the device.
Enable IP forwarding on the peer through which other devices on the network will connect to WireGuard peer(s):
See sysctl#Configuration for instructions on how to set the sysctl parameters on boot.
Site-to-site
To connect two (or more) networks, apply both #Point-to-site and #Site-to-point on all sites.
Routing all traffic over WireGuard

To use a peer as a DNS server, add its WireGuard tunnel IP address(es) to /etc/resolv.conf. For example, to use peer B as the DNS server:
Basic checkups
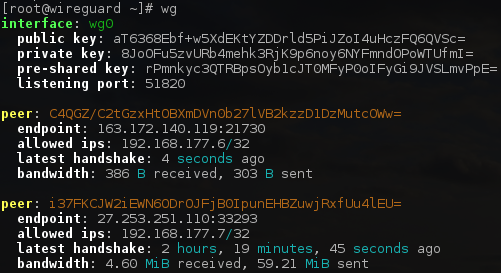
Invoking the wg(8) command without parameters will give a quick overview of the current configuration.
As an example, when peer A has been configured we are able to see its identity and its associated peers:
At this point one could reach the end of the tunnel. If the peers do not block ICMP echo requests, try pinging a peer to test the connection between them.
After transferring some data between peers, the wg utility will show additional information:
Persistent configuration
wg-quick
The current WireGuard configuration can be saved by utilizing the wg(8) utility’s showconf command. For example:
To start a tunnel with a configuration file, use
systemd-networkd
systemd-networkd has native support for setting up WireGuard interfaces. An example is provided in the systemd.netdev(5) § EXAMPLES man page.
. ) will prevent the DNS resolution of endpoints.
systemd-networkd: routing all traffic over WireGuard
In this example Peer B connects to peer A with public IP address. Peer B routes all its traffic over WireGuard tunnel and uses Peer A for handling DNS requests.
Assumes ufw, but you could do the same with iptables by using the rules outlined in the Server configuration section:
Exempting specific addresses
In order to exempt specific addresses (such as private LAN addresses) from routing over the WireGuard tunnel, add them to a higher-priority RoutingPolicyRule than the one that was just created. This will configure them to use the default routing table, and prevent them from using the WireGuard table.
Netctl
Netctl has native support for setting up WireGuard interfaces. A typical set of WireGuard netctl profile configuration files would look like this:
Then start and/or enable wg0 interface on every participating peer as needed, i.e.
To implement persistent site-to-peer, peer-to-site or site-to-site type of connection with WireGuard and Netctl, just add appropriate Routes= line into the netctl profile configuration file and add this network to AllowedIPs in the WireGuard profile, e.g. Routes=(‘192.168.10.0/24 dev wg0’) in the /etc/netctl/wg0 and AllowedIPs=10.0.0.1/32, 192.168.10.0/24 in /etc/wireguard/wg0.conf and then do not forget to enable IP forwarding.
NetworkManager
NetworkManager has native support for setting up WireGuard interfaces. For all details about WireGuard usage in NetworkManager, read Thomas Haller’s blog post—WireGuard in NetworkManager.
The following examples configure WireGuard via the keyfile format .nmconnection files. See nm-settings-keyfile(5) and nm-settings(5) for an explanation on the syntax and available options.
To use a peer as the only DNS server, set a negative DNS priority (e.g. dns-priority=-1 ) and add
. to the dns-search= settings.
Specific use-case: VPN server

The purpose of this section is to set up a WireGuard «server» and generic «clients» to enable access to the server/network resources through an encrypted and secured tunnel like OpenVPN and others. The «server» runs on Linux and the «clients» can run on any number of platforms (the WireGuard Project offers apps on both iOS and Android platforms in addition to Linux, Windows and MacOS). See the official project install link for more.
Server

On the peer that will act as the «server», first enable IPv4 forwarding using sysctl:
A properly configured firewall is HIGHLY recommended for any Internet-facing device.
If the server has a public IP configured, be sure to:
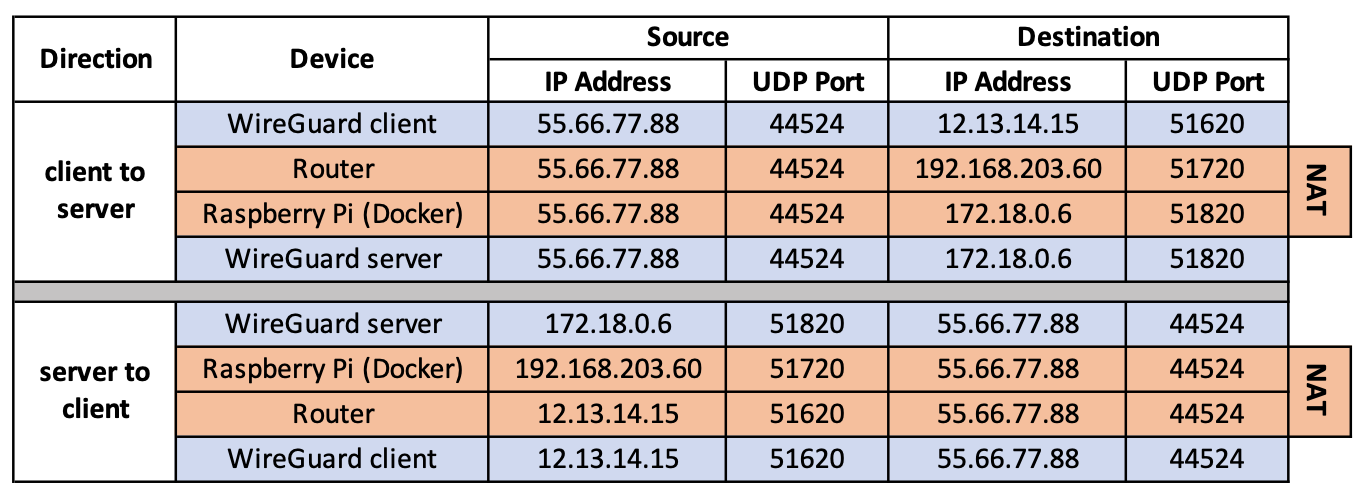
If the server is behind NAT, be sure to forward the specified port(s) on which WireGuard will be running (for example, 51820/UDP ) from the router to the WireGuard server.
Key generation
Generate key pairs for the server and for each client as explained in #Key generation.
Server configuration
Create the «server» configuration file:
Additional peers («clients») can be listed in the same format as needed. Each peer requires the PublicKey to be set. However, specifying PresharedKey is optional.
Client configuration
Create the corresponding «client» configuration file(s):
Using the catch-all AllowedIPs = 0.0.0.0/0, ::/0 will forward all IPv4 ( 0.0.0.0/0 ) and IPv6 ( ::/0 ) traffic over the VPN.
Testing the tunnel

Once a tunnel has been established, one can use netcat to send traffic through it to test out throughput, CPU usage, etc. On one side of the tunnel, run nc in listen mode and on the other side, pipe some data from /dev/zero into nc in sending mode.
In the example below, port 2222 is used for the traffic (be sure to allow traffic on port 2222 if using a firewall).
On one side of the tunnel listen for traffic:
On the other side of the tunnel, send some traffic:
Status can be monitored using wg directly.
Tips and tricks
Store private keys in encrypted form
where user is the Linux username of interest. See the wg-quick(8) man page for more details.
Endpoint with changing IP
After resolving a server’s domain, WireGuard will not check for changes in DNS again.
Also be aware, if the endpoint is ever going to change its address (for example when moving to a new provider/datacenter), just updating DNS will not be enough, so periodically running reresolve-dns might make sense on any DNS-based setup.
One needs to run the /usr/share/wireguard-tools/examples/reresolve-dns/reresolve-dns.sh /etc/wireguard/wg.conf periodically to recover from an endpoint that has changed its IP.
One way of doing so is by updating all WireGuard endpoints once every thirty seconds[6] via a systemd timer:
Afterwards enable and start wireguard_reresolve-dns.timer
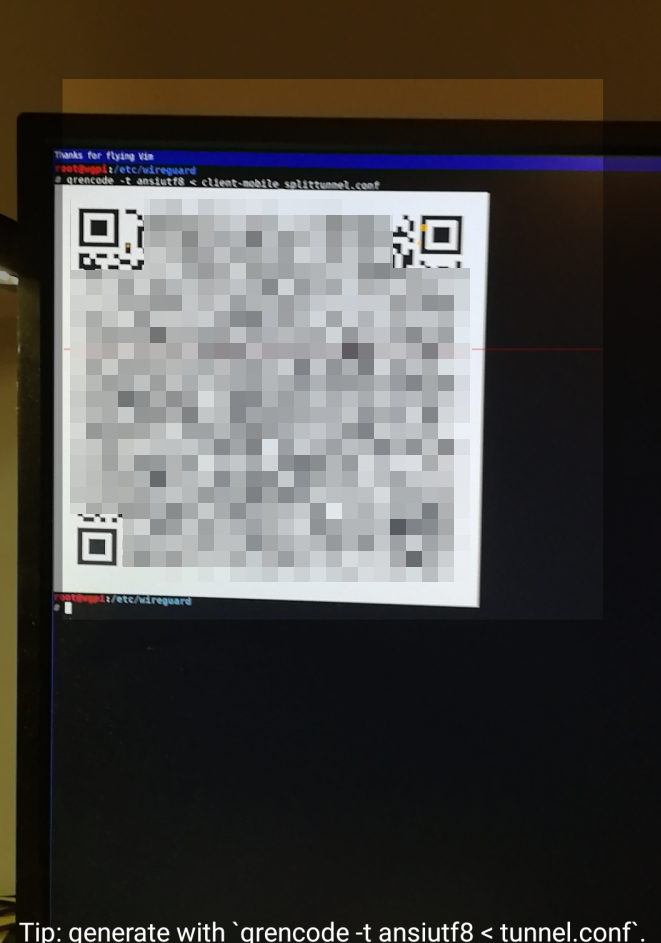
Generate QR code
If the client is a mobile device such as a phone, qrencode can be used to generate client’s configuration QR code and display it in terminal:
Enable debug logs
When using the Linux kernel module on a kernel that supports dynamic debugging, debugging information can be written into the kernel ring buffer (viewable with dmesg and journalctl) by running:
Reload peer (server) configuration
In case the WireGuard peer (mostly server) adding or removing another peers from its configuration and wants to reload it without stopping any active sessions, one can execute the following command to do it:

Troubleshooting
Routes are periodically reset
Users of NetworkManager should make sure that it is not managing the WireGuard interface(s). For example, create the following configuration file:
Broken DNS resolution
By default wg-quick uses resolvconf to register new DNS entries (from the DNS keyword in the configuration file). This will cause issues with network managers and DHCP clients that do not use resolvconf, as they will overwrite /etc/resolv.conf thus removing the DNS servers added by wg-quick.
The solution is to use networking software that supports resolvconf.
Users of NetworkManager should know that it does not use resolvconf by default. It is recommended to use systemd-resolved. If this is undesirable, install openresolv and configure NetworkManager to use it: NetworkManager#Use openresolv.
Low MTU
Due to too low MTU (lower than 1280), wg-quick may have failed to create the WireGuard interface. This can be solved by setting the MTU value in WireGuard configuration in Interface section on client.
Key is not the correct length or format
To avoid the following error, put the key value in the configuration file and not the path to the key file.
Unable to establish a persistent connection behind NAT / firewall
By default, WireGuard peers remain silent while they do not need to communicate, so peers located behind a NAT and/or firewall may be unreachable from other peers until they reach out to other peers themselves (or the connection may time out). Adding PersistentKeepalive = 25 to the [Peer] settings of a peer located behind a NAT and/or firewall can ensure that the connection remains open.
Loop routing
Adding the endpoint IP to the allowed IPs list, the kernel will attempt to send handshakes to said device binding, rather than using the original route. This results in failed handshake attempts.
As a workaround, the correct route to the endpoint needs to be manually added using
e.g. for peer B from above in a standard LAN setup:
Using NetworkManager, a more flexible solution is to start WireGuard using a dispatcher script. As root, create
mzpqnxow/generate-wireguard-allowed-qr
Use Git or checkout with SVN using the web URL.
Work fast with our official CLI. Learn more.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
Generate AllowedIPs Text / QR Code in Terminal For Granular WireGuard® Tunnel Exclusions
Hopefully you know by now, but WireGuard® is an extremely simple yet fast and modern VPN that utilizes state-of-the-art cryptography. You can read more about it here
Generate AllowedIPs Value As Text String or QR Code in Terminal For Granular WireGuard® Tunnel Exclusions
Given a list of IPv4 addresses (dotted quad, CIDR) print an inclusion list ( AllowedIPs string) suitable for the WireGuard® mobile app, optionally generating a QR code using ANSI escape characters in a standard terminal window. Useful for excluding only a partial set of LAN (or WAN) addresses from the WireGuard® tunnel. Currently, the only «easy» option for accessing a LAN is to opt all RFC1918/RFC3330 private addresses out of the tunnel, using the checkbox that the WireGuard® client provides. This script allows a more granular specification, and also allows the specification of specific WAN addresses as well
Quick-Start (See Usage For Detailed Instructions)
Generate a fine-grained AllowedIPs value that excludes only three specific LAN addresses to bypass the tunnel:
This command will generate a QR code which will be printed to your terminal/TTY containing the AllowedIPs value, and will also print a text version
Specific Use-Case (LAN + Security Concerns)
Consider a mobile user with an on-demand WireGuard® VPN connection for the purpose of both privacy and security that needs to access only a small subset of LAN hosts (or WAN hosts) outside of the tunnel. By using fine-grained addresses in the AllowedIPs parameter, this can be accomplished without hassle. The effect:
Natively Supported WireGuard® Options for LAN Access via Tunnel Bypass
One existing and very simple solution is to use the built-in «Exclude Private IPs» option in the WireGuard® mobile app, which generates a fixed list that simply generates an AllowedIPs address list that excludes all RFC1918/RFC3330 Private Addresses. However, this is a very broad range and is not trivial to tweak
Using this rinky-dink little app, you can specify granular exclusions, e.g. 192.168.1.2 192.168.1.3 192.168.1.4 for the WireGuard® tunnel and receive a list of networks suitable for the AllowedIPs
Allowing, e.g., only 192.168.1.2, 192.168.1.3 and 192.168.1.4 (as opposed to 192.168.0.0/16) effectively protects the rest of the 192.168.0.0/16 network from being exposed to the device. It also effectively protects the device from the rest of the 192.168.0.0/16 network (and 10/8 and 172.16/12 as well, if relevant)
Why Is Code Required? Can’t I Just Specify The List Myself?
In case it isn’t already clear, WireGuard® mobile only allows the client to specify IP addresses that are «allowed» to use the tunnel. It is an opt-in system, most easily used when performing a LAN-to-LAN tunnel. It does not allow the user to specify a blacklist- to do this, a long list of «non-blacklisted» networks must be generated. Because of this, you can’t briefly or easily say «all traffic except to/from host 192.168.1.3 should transit the tunnel easily». Instead, you need a list of CIDR notation networks that make up the entire IPv4 address space, excluding «192.168.1.3».
If you’re curious, the value for this specific example looks like this and is rather unwieldy, which is where the QR code functionality comes in handy:
This is a bit much to effectively specify just a single host for tunnel bypass, and is not so simple to construct in your head, unless you’re an advanced human subnet calculator
Caveat Emptor / NOTES
Given a list of dotted-quad and CIDR notation IPv4 networks on the command-line, generate the inverse in the format WireGuard® prefers. Optionally, produce a QR code on the terminal screen that scan be easily scanned into mobile devices
This was written to create an «Allowed IPs» list for the WireGuard® mobile app to allow granular tunnel bypass. WireGuard® currently doesn’t allow you to supply an «Excluded IPs» option, so you have to invert the networks that you want to bypass the tunnel. This overengineered app will do that for you. One very convenient feature is printing a QR code so that the Allowed IPs list will be easy to copy to a mobile device
Use WireGuard® tunnel for all networks except 192.168.1.0/24 and 192.168.2.0/24:
The same, but don’t route IPv6 through the tunnel (note the last network in the output):
Allow only 192.168.1.1 and 192.168.1.2 to bypass the tunnel:
NOTE: When using QR code, the ‘AllowedIPs =’ string literal will not be included in the QR data by design, so that the data can be pasted into the value box on the mobile app IMPORTANT: You may also need to specify the WireGuard® peer address as an exclusion, you should test this
QR Code Support Dependencies
There are two ways to generate QR codes. By default, the script will try to use the qrcode Python module if available. If not available, it will fall back to using the qrencode application if it is present on your system. If neither are found, it will report an error
(RECOMMENDED) Python Package: qrcode
The qrcode is a simple, excellent QR code generation Python package that supports output to terminal windows as well as image files
(RECOMMENDED) Install qrcode via pip
Install qrcode With Your OS Package Manager
This is not recommended as many distributions have dated versions of Python modules in their repositories. The distribution package is probably called python3-qrcode
OS Native / Package: qrencode
Use your distribution package manager to install qrencode
Debian / Ubuntu / Kali
$ sudo apt-get install qrencode
RHEL, Fedora, CentOS
$ sudo yum install qrencode
If you would like to use a different QR code generator, you can change the QR_ENCODE_COMMAND list in the script, or you can add code to use some other Python library. This isn’t recommended
Setting up WireGuard
I’ve been dying to try out WireGuard for a while now, and I finally got around to it. I was scouring tutorials and also checked the docs and figure it all out. It’s a new VPN protocol, that works similarly to ssh. I’ve put my desktop, iPhone, and MacBook Air on it. Here’s a few neat things it’s allowed me to try:
There’s so much more you can do, hopefully that gives you some ideas.
Here’s the fastest way to get it running on Ubuntu and iOS, while also persisting your configuration.
Server Setup
Get an Ubuntu server running 20.04, I like to use Digital Ocean. After setup, I tend to change the default SSH port in /etc/ssh/sshd_config and also disable root logins.
First, we need to enable ipv4 forwarding, so that traffic flows through our VPN:
Now let’s install WireGuard
Let’s generate keys for our server
the first command ensures that our outputted file can only be used by the current user, as a security precaution. The remaining piped commands come from the key generation docs from WireGuard. After that, I am copying the files into the wireguard directory for safe keeping.
Create our first peer’s keys
Let’s create our WireGuard interface configuration.
sudo vim /etc/wireguard/wg0.conf
Internal IP for the interface
Next, we enable the service, so that it runs on boot, and start it:
Run sudo wg and make sure you see your interface and peers listed with the correct addresses. You can create multiple interfaces, just make wg1.conf and enable that, instead of wg0 above. This can be useful if you have a lot of devices and networks you want to setup.
iOS config
Our server is good to go! Let’s make a config file for iOS now. There’s nothing special about this config, and it could be used on any type of device. But at the end we will encode it in a QR code for usage in the mobile WireGuard app.
Add to device
You’ll now see a QR code. Scan it using the WireGuard iOS app, and you should be connected!
Adding more peers
Here’s a quick reference for when you want to add a new client device to your VPN network.
Now we need to update our /etc/wireguard/wg0.conf file:
If your device is behind a firewall, and it is going to be routinely used as a server, you will want to use PersistentKeepalive, otherwise you can omit it.
My desktop doesn’t access anything from my iPhone, so my iPhone doesn’t use it. However, I do use PersistentKeepalive on my desktop, because my iPhone regularly connects to its development server, file share, etc and it is behind a router.
Now we run sudo systemctl restart wg-quick@wg0 and then sudo wg should show the peer we just added.
Copy the DESKTOP.conf file to your device, or use the QR method from above for mobile. Repeat these steps and replace DESKTOP with your real device name!
If you are serious about using this, it can be nice to setup a DNS server as well. This way you can alias all your device IP’s and just use macbook or iphone when connecting between devices. Follow this guide for more on that. I wanted to keep this tutorial to the bare minimum. Because of my interest in WireGuard, I’ve been following a tuturial on making a DNS server in Rust. So I may write about setting that up if I end up finishing it.
I hope this was helpful, as I had found a mix of the above steps, and some extra unnecessary things on other tutorials.
Wireguard
From DD-WRT Wiki
Contents
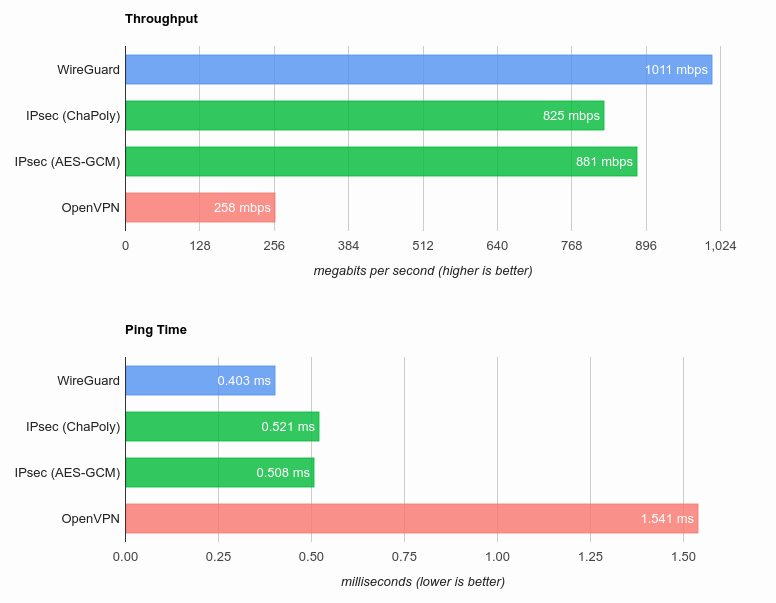
WireGuard® is an extremely simple yet fast and modern VPN that utilizes state-of-the-art cryptography. It aims to be faster, simpler, leaner, and more useful than IPsec, while avoiding the massive headache. It intends to be considerably more performant than OpenVPN.
Some key points about Wireguard:
[edit] How it works
Quick Start, Conceptual Overview
This tutorial shows the basics of securely creating a tunnel from a client device to DD-WRT. Before proceeding, verify a working reset button and configuration backup in case of problems.
[edit] What is a QR Code?
The «Quick Response» Code is a two-dimensional barcode with larger encoded data capacity and high fault tolerance. Since build 38581 in February 2019, a client config can be imported using a QR Code. The advantage of this approach is that there is no need to transfer sensitive information via potentially compromised data channels.
[edit] Install and Setup Guides
The WireGuard installation/downloads page has software and instructions per OS.
WireGuard Forum Guides:
These forum guides have the latest updated information and additional scripts such as:
[edit] Setup Instructions
Add Peers:
For simple configurations, just enter Peer Tunnel IP within the oet1 interface ip range (e.g. 10.10.0.2) and Peer Tunnel DNS (8.8.8.8). Peer Tunnel MTU will be calculated automatically (WAN mtu-40) but can then be edited. Click Save then the QR-Code button to generate it.
Masquerade the tunnel:
Wireguard must be unbridged, using Forwarding and NAT. Go to Networking, unbridge the oet1 interface (automatic since r42067), and enable Masquerade / NAT to have internet on the tunnel. Click Apply.
[edit] Note for Access Point mode
Add the following firewall rule under Administration/Commands and save as firewall then reboot:
[edit] Android/iOS config import
Android: Google Play Store, iOS: Apple Store (12.0 or later)
WireGuard app: press «+» in the lower right corner, select «Create from QR code», scan from DD-WRT peer, then the app will prompt to name the tunnel. Public IP can be checked here.
[edit] Linux config import
Review the Wireguard install page, distribution wiki (e.g. for Arch) and/or forums for more details.
Using a network manager with Wireguard and preshared key support is optional but much easier.
[edit] Windows config import
[edit] Options
Persistent Keep Alive: This is seconds between keep alive messages, and is optional. Default is 0 (Disabled). The recommended value for NAT’d devices is 25 seconds.
Allowed IPs: This is required and represents IP addresses that this peer is allowed to use inside the tunnel. Usually the peer’s tunnel IP addresses and the networks the peer routes through tunnel. Outgoing packets will be sent to the peer whose Allowed IPs contain the destination address, and for multiple matches, the longest matching prefix is chosen. Incoming packets are only accepted if traffic to their source IP would be sent to the same peer. May be specified multiple times.
Preshared Key: A base64 preshared key generated by wg genpsk. This is optional and may be omitted. This adds an additional layer of symmetric-key cryptography into the existing public-key cryptography, for post-quantum resistance.
[edit] Troubleshooting
If you find any bugs report to: team@wireguard.com
[edit] Useful console commands
Check the tunnel status:
Check if the oet1 network is NAT’d:
[edit] Dynamic WAN IP on router
After importing configs from DD-WRT to Android/iOS app, edit the Endpoint in the Peer section e.g.:
[edit] Adding a second peer breaks the first
Allowed IPs of 0.0.0.0/0 cannot be used for both peers as it causes a collision. Instead set separate peer IPs e.g. 10.10.0.2/32 and 10.10.0.3/32. The Allowed IP’s feature is for crypto routing. The key is valid for the entire allowed IP space.
[edit] Resolving local hostnames in the tunnel
Wireguard
From DD-WRT Wiki
Contents
WireGuard® is an extremely simple yet fast and modern VPN that utilizes state-of-the-art cryptography. It aims to be faster, simpler, leaner, and more useful than IPsec, while avoiding the massive headache. It intends to be considerably more performant than OpenVPN.
Some key points about Wireguard:
[edit] How it works
Quick Start, Conceptual Overview
This tutorial shows the basics of securely creating a tunnel from a client device to DD-WRT. Before proceeding, verify a working reset button and configuration backup in case of problems.
[edit] What is a QR Code?
The «Quick Response» Code is a two-dimensional barcode with larger encoded data capacity and high fault tolerance. Since build 38581 in February 2019, a client config can be imported using a QR Code. The advantage of this approach is that there is no need to transfer sensitive information via potentially compromised data channels.
[edit] Install and Setup Guides
The WireGuard installation/downloads page has software and instructions per OS.
WireGuard Forum Guides:
These forum guides have the latest updated information and additional scripts such as:
[edit] Setup Instructions
Add Peers:
For simple configurations, just enter Peer Tunnel IP within the oet1 interface ip range (e.g. 10.10.0.2) and Peer Tunnel DNS (8.8.8.8). Peer Tunnel MTU will be calculated automatically (WAN mtu-40) but can then be edited. Click Save then the QR-Code button to generate it.
Masquerade the tunnel:
Wireguard must be unbridged, using Forwarding and NAT. Go to Networking, unbridge the oet1 interface (automatic since r42067), and enable Masquerade / NAT to have internet on the tunnel. Click Apply.
[edit] Note for Access Point mode
Add the following firewall rule under Administration/Commands and save as firewall then reboot:
[edit] Android/iOS config import
Android: Google Play Store, iOS: Apple Store (12.0 or later)
WireGuard app: press «+» in the lower right corner, select «Create from QR code», scan from DD-WRT peer, then the app will prompt to name the tunnel. Public IP can be checked here.
[edit] Linux config import
Review the Wireguard install page, distribution wiki (e.g. for Arch) and/or forums for more details.
Using a network manager with Wireguard and preshared key support is optional but much easier.
[edit] Windows config import
[edit] Options
Persistent Keep Alive: This is seconds between keep alive messages, and is optional. Default is 0 (Disabled). The recommended value for NAT’d devices is 25 seconds.
Allowed IPs: This is required and represents IP addresses that this peer is allowed to use inside the tunnel. Usually the peer’s tunnel IP addresses and the networks the peer routes through tunnel. Outgoing packets will be sent to the peer whose Allowed IPs contain the destination address, and for multiple matches, the longest matching prefix is chosen. Incoming packets are only accepted if traffic to their source IP would be sent to the same peer. May be specified multiple times.
Preshared Key: A base64 preshared key generated by wg genpsk. This is optional and may be omitted. This adds an additional layer of symmetric-key cryptography into the existing public-key cryptography, for post-quantum resistance.
[edit] Troubleshooting
If you find any bugs report to: team@wireguard.com
[edit] Useful console commands
Check the tunnel status:
Check if the oet1 network is NAT’d:
[edit] Dynamic WAN IP on router
After importing configs from DD-WRT to Android/iOS app, edit the Endpoint in the Peer section e.g.:
[edit] Adding a second peer breaks the first
Allowed IPs of 0.0.0.0/0 cannot be used for both peers as it causes a collision. Instead set separate peer IPs e.g. 10.10.0.2/32 and 10.10.0.3/32. The Allowed IP’s feature is for crypto routing. The key is valid for the entire allowed IP space.
[edit] Resolving local hostnames in the tunnel
PiVPN Wireguard
List of commands
Creating new client configuration
Removing a client configuration
Asks you for the name of the client to remove. Once you remove a client, it will no longer allow you to use the given client config (specifically its public key) to connect. This is useful for many reasons but some ex: You have a profile on a mobile phone and it was lost or stolen. Remove its key and generate a new one for your new phone. Or even if you suspect that a key may have been compromised in any way, just remove it and generate a new one.
Listing clients
If you add more than a few clients, this gives you a nice list of their names and associated keys.
Creating a server backup
Creates a backup archive of your Wireguard Settings and Client certificates, and places it on your pivpn user home directory
Help with troubleshooting
Outputs setup information needed when troubleshooting issues
Importing client profiles
Windows
Use a program like WinSCP or Cyberduck. Note that you may need administrator permission to move files to some folders on your Windows machine, so if you have trouble transferring the profile to a particular folder with your chosen file transfer program, try moving it to your desktop.
Mac/Linux
Open the Terminal app and copy the config from the Raspberry Pi to a target directory on your local machine:
Android / iOS
Connecting to Wireguard
Windows/Mac
Download the WireGuard GUI app, import the configuration and activate the tunnel.
Linux
Install WireGuard following the instructions for your distribution. Now, as root user, create the /etc/wireguard folder and prevent anyone but root to enter it (you only need to do this the first time):
Move the config and activate the tunnel:
Run wg-quick down whatever to deactivate the tunnel.
Android/iOS
Pi-hole with PiVPN
You can safely install PiVPN on the same Raspberry Pi as your Pi-hole install, and point your VPN clients to the IP of your Pi-hole so they get ad blocking, etc. (replace 192.168.23.211 with the LAN IP of your Raspberry Pi).
if you install PiVPN after Pi-hole, your existing Pi-hole installation will be detected and the script will ask if you want to use it as the DNS for the VPN, so you won’t need to go through the following steps.
If you installed PiVPN before pi-hole:
New clients you generate will use Pi-hole but you need to manually edit existing clients:
Changing the public IP/DNS
New clients you generate will use the new endpoint but you need to manually edit existing clients:
Blocking internet access
Migrating PiVPN & Wireguard
/etc with the starting slash is a system directory
etc/ without starting slash and tailing slash means its a directory in your current working dir.
Resolving local hostnames
All you have to do is to use your router as DNS Server instead of using other public DNS providers. If you have already a working installation of WireGuard, all you need to do is to edit your client config and change the line DNS = [. ], [. ] to DNS = 192.168.23.1 (assuming 192.168.23.1 is your gateway IP).
Alternatively you can change /etc/hosts file and add Example:
Keep Wireguard connected / Connection issues / PersistentKeepalive
Per default Wireguard connects on-demand which is fine for most situations. It’s also the recommended configuration for mobile devices because of energy consumption.
But it might be useful to keep the Wireguard connection up to avoid certain connection issues that can occur e.g. when NAT is being used which forces undesired disconnections. Keeping the connection up can also reduce the reconnection time a bit, even though Wireguard usually connects in under a second.
A good value of thumb for this setting is 25 seconds. You may also put a lower number if required. Setting it to 0 turns the feature off, which is the default. (Wireguard Quickstart Guide)
The WireGuard client config file required the config parameter PersistentKeepalive = 25 in the [Peer] section.
This setting will be added automatically to the client config profiles when added to the /etc/pivpn/wireguard/setupVars.conf file ( pivpnPERSISTENTKEEPALIVE=25 ).
Updating Wireguard
if you installed PiVPN on or after March 17th 2020 WireGuard will be upgraded via the package manager (APT)
WireGuard Setup Guide for iOS
WireGuard is the new kid on the block when it comes to VPNs. I could try and explain what it is and why you should switch from OpenVPN or IPsec to it, but they do a great job of that themselves:
WireGuard® is an extremely simple yet fast and modern VPN that utilizes state-of-the-art cryptography. It aims to be faster, simpler, leaner, and more useful than IPSec, while avoiding the massive headache.
“Great” I hear you say, “but IPSec and OpenVPN are a pain to setup, let alone setup securely”. Fear not, WireGuard has you covered:
WireGuard aims to be as easy to configure and deploy as SSH. A VPN connection is made simply by exchanging very simple public keys – exactly like exchanging SSH keys – and all the rest is transparently handled by WireGuard.
This guide will walk you through how to setup WireGuard in a way that all your client outgoing traffic will be routed via another machine (server). This is ideal for situations where you don’t trust the local network (public or coffee shop wifi) and wish to encrypt all your traffic to a server you trust, before routing it to the Internet.
Server Setup Guide
I am making some assumptions here, such as using Ubuntu for your server OS, so please tweak to fit your situation.
First up, we need to make sure you’ve got the kernel headers installed, as well as enabling IPv4 forwarding:
Because WireGuard isn’t currently part of the distributed Ubuntu packages, we’ll add the helpful PPA repository to keep things easy and up to date.
With WireGuard now installed, we need to generate a public and a private key – fortunately, this is a simple one-liner:
Next up, we need to create a WireGuard config file:
We also need a DNS server running, to forward our requests from the clients rather than letting the clients go out to their local/ISP provided DNS. I have pinched most of this from ck’s Wireguard setup guide.
At this point, WireGuard on the server is complete and we could start it up if we wanted, but first, lets configure our client.
iOS Client Setup Guide
Our first client is an Apple iOS device. Currently WireGuard isn’t built into the operating system, unlike IPSec or IKEv2. However, we can easily overcome this hurdle thanks to the WireGuard iOS App which is currently in alpha and can be installed easily via TestFlight. Alternatively you can check out another 3rd party client produced by TunSafe which again can be installed via TestFlight.
With one of the two apps installed, lets generate a config server-side and we can transfer it later with a simple QR code. We could manually enter a config within the app, however moving around those keys can be a nightmare…
First up, client private and public keys:
However if you would rather run it as a service so that it is always brought up on start-up or after reboots, we can utilise systemctl :
You can get the current status of WireGuard by simply running wg :
With WireGuard successfully running, lets create a conf file for our iOS device which we will transfer via QR code. We can do all of this whilst we are still on our server.
To generate the QR code and display it on the screen:
A QR code generated from `mobile.conf`
Simply scan this code using one of the iOS apps mentioned previously, and you will be all setup! Enjoy routing all of your traffic via your server. You can verify this by visiting https://canihazip.com or similar on your device.
$ whoami I am Graham Stevens, a Cyber Security Specialist based in the South West of the UK. If you’re lucky, I very occasionally post updates on Twitter.
WireGuard (Virtual Private Network)
About WireGuard
WireGuard is an extremely simple yet fast and modern VPN that utilizes state-of-the-art cryptography. It can be a useful replacement for IPSec or OpenVPN.
Installation
You can install wireguard from the Apps section of the FreedomBox web interface.
Usage
Note: These steps are handled automatically on FreedomBox. So you only need to follow these steps on any Debian clients that will connect to FreedomBox, or Debian servers that FreedomBox will connect to.
The client can be configured in several ways:
This is self-explanatory, you actually create the config on the mobile device then transfer the relevant keys to the server’s config.
The mobile client as of version 0.0.20180724 supports QR code based input.
qrencode can be used to generate qr codes, even in a terminal/console using UTF8 characters.
This will generate a QR code that is readable by the mobile client.
The advantage of this approach is that there is no need to transfer sensitive information via data channels that can potentially be compromised and there is no need for any additional software.
Free Wireguard VPN service on AWS
The reasoning
The increase of Internet censorship by authoritarian regimes expands the blockage of useful internet resources making impossible the use of the WEB and in essence violates the fundamental right to freedom of opinion and expression enshrined in the Universal Declaration of Human Rights.
Article 19
Everyone has the right to freedom of opinion and expression; this right includes freedom to hold opinions without interference and to seek, receive and impart information and ideas through any media and regardless of frontiers.
The following is the detailed 6 steps instruction for non-IT people to deploy free* VPN service upon Wireguard technology in Amazon Web Services (AWS) cloud infrastructure, using a 12 months free account, on an Instance (virtual machine) run by Ubuntu Server 18.04 LTS.
I tried to make this walkthrough as friendly as possible to people far from IT. The only thing required is assiduity in repeating the steps described below.
Stages
Useful links
The authors
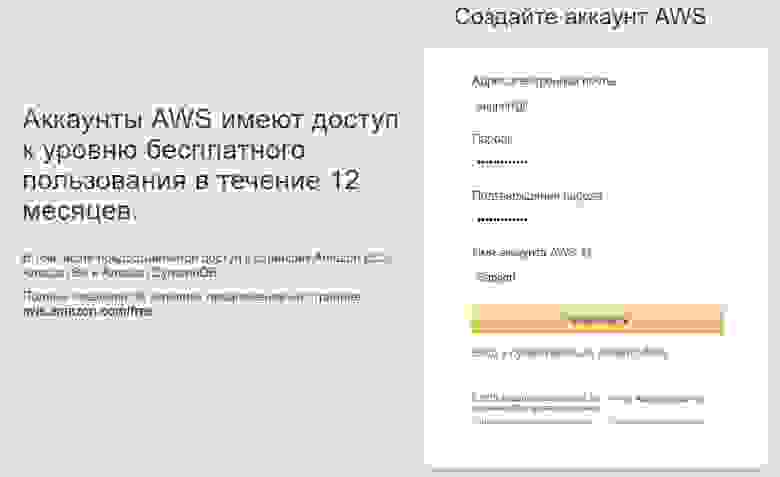
1. Register the AWS Free Account
To register an AWS account, you need to submit a valid phone number and a bank card (Visa or Mastercard). I recommend using virtual cards provided for free by Yandex.Money or Qiwi wallet.
AWS checks the validity of the card by deducting 1$ at registration followed by the refund.
1.1. Opening the AWS Management Console
Follow the link: https://aws.amazon.com/, click on the Create an AWS account button.
1.2. AWS account creation
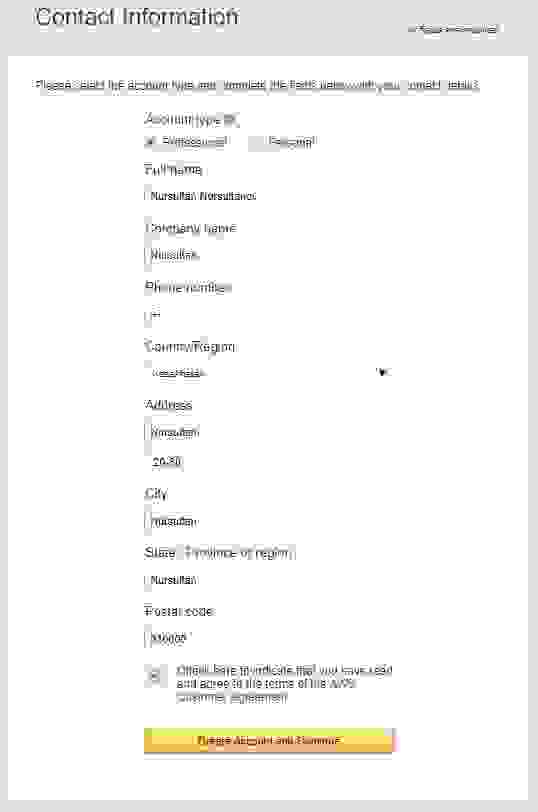
Fill in the data and click the Continue button.
1.3. Contact information for AWS account
1.4. Specify billing information
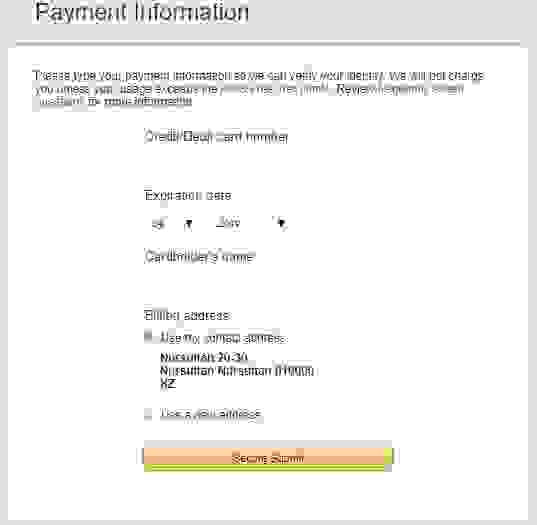
Card number, expiry date, and a cardholder name.
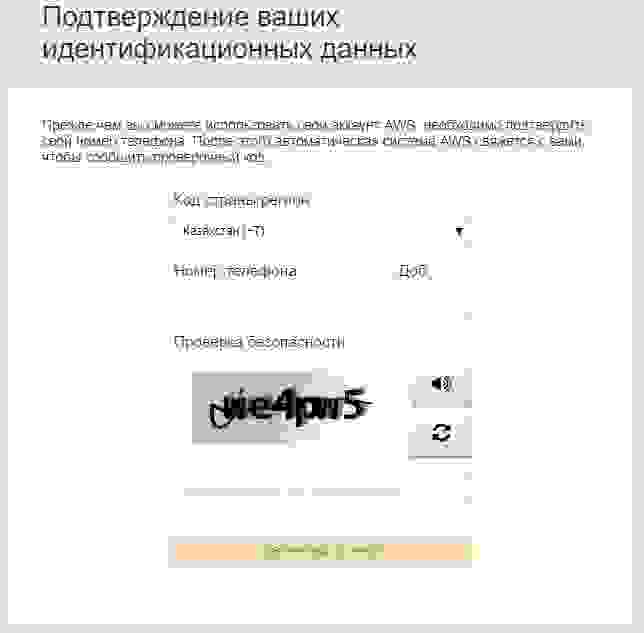
1.5. Account Verification
1.6. Choosing an AWS support plan
Choose a Basic plan (free).
Login into AWS Management Console
1.8. Choosing the location of the Datacenter
1.8.1. Internet speed testing
I recommended you to run a speed test to the nearest Datacenters at https://speedtest.net/ and choose the best to connect to.
The following are the speed test results from my location:
The Datacenter in London shows the best speed result, so I choose it to proceed with.
2. Create an AWS instance
2.1 Create a virtual machine (instance)
2.1.0. Follow the instance creation steps
2.1.0.1. Go to the Instance Launch page, choose EC-2 service
2.1.0.2. Launch a virtual server, known as Amazon EC-2 Instance
2.1.0.3. Choose Amazon machine Image (Operating System) — the Ubuntu Server 18.04 LTS
2.1.1. Choose Instance type
The t2.micro instance type is set by default and is the right one to go with. Click the Next: Configure Instance Details button to proceed.
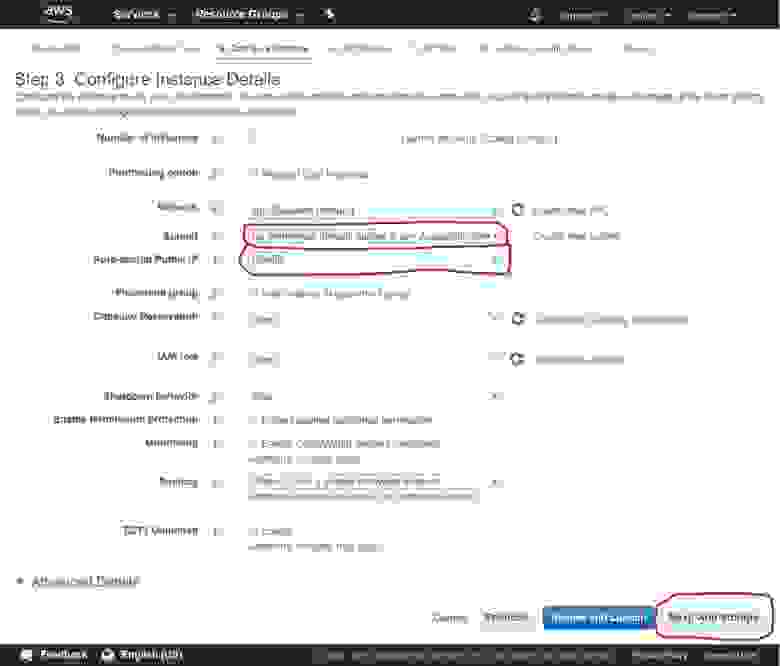
2.1.2. Configure Instance details
Disable the auto-assignment of the public IP as you will assign a static one to your Instance. Click the Next: Add Storage button.
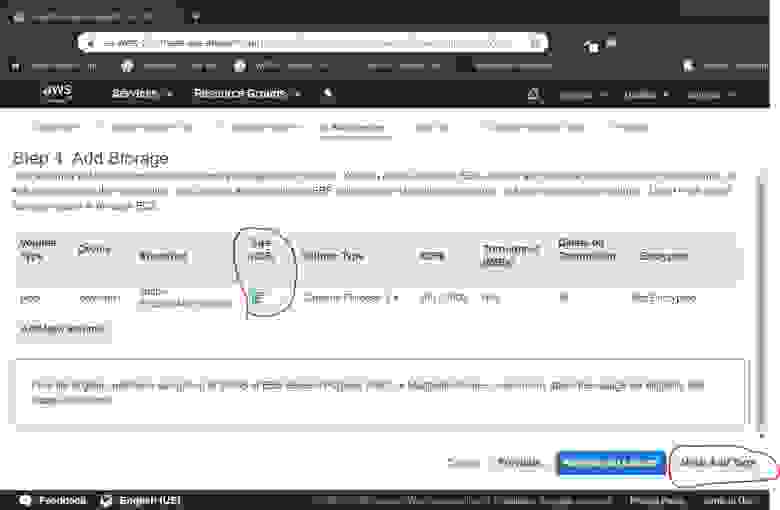
2.1.3. Add storage
Specify the size of the Drive — the 16GB is enough.
Click Next: Add Tags button.
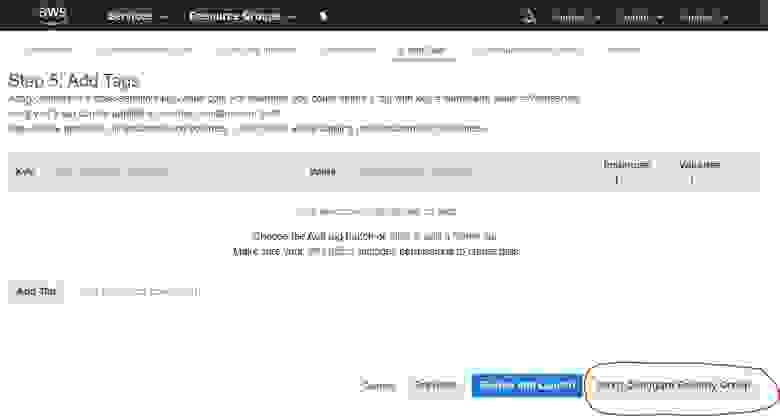
2.1.4. Add Tags
If you have several instances, you may group them by tags to enable better administration. Yet, this functionality is surplus. So we skip this by pressing the Next: Configure Security Group button.
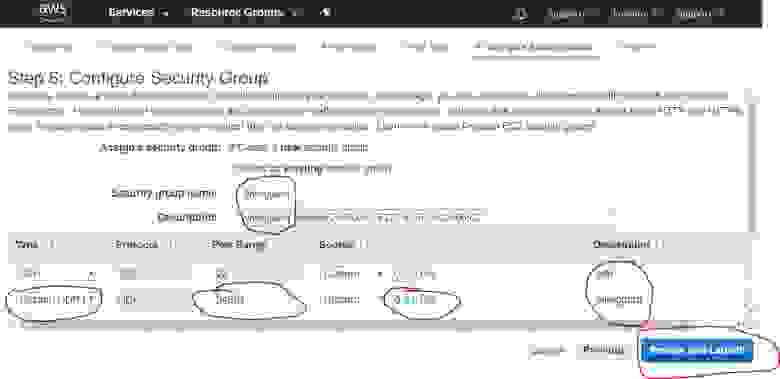
2.1.5. Opening ports
Configure the firewall by assigning open ports. The set of open ports is called the «Security Group». You need to create a new «Security Group», give it a name, a description and a UDP port (Custom UDP Rule).
In the Port Range field specify a port number from the range 49152 — 65535 of dynamic ports. In my case, I choose the 54321 port number.
Click the Review and Launch button to complete this step.
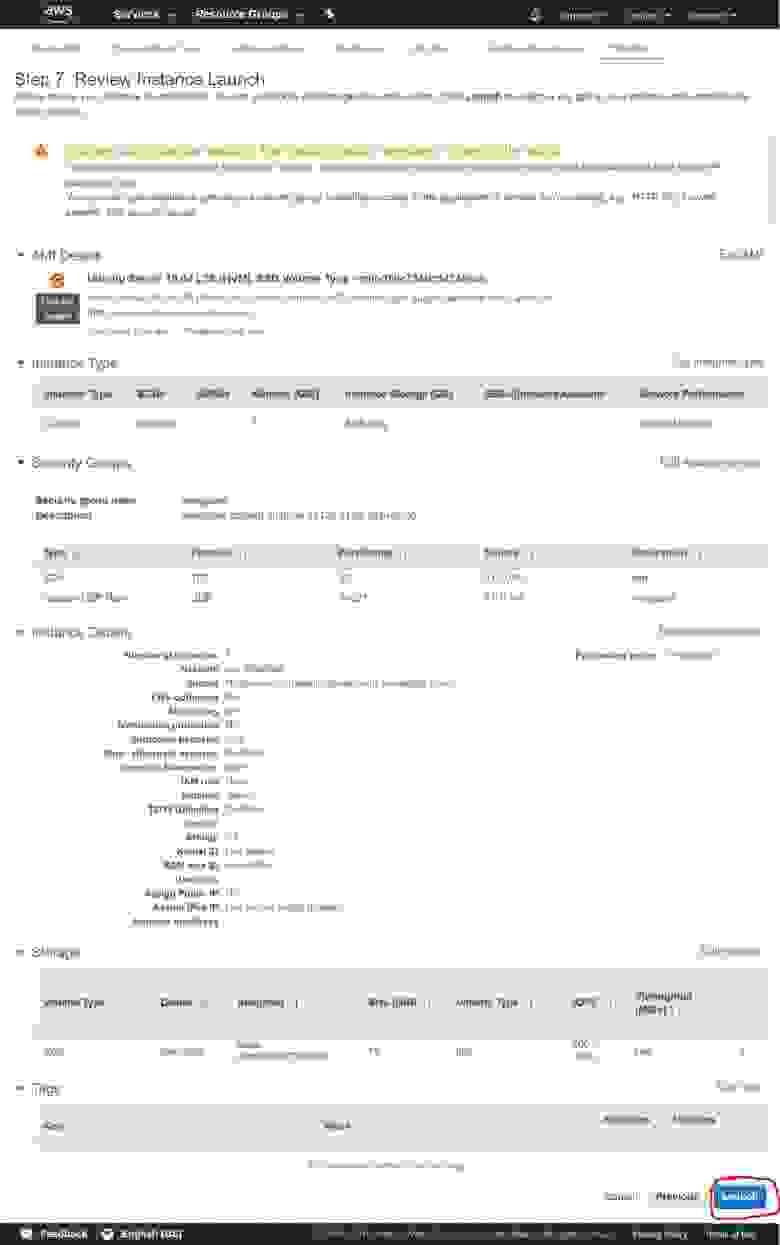
2.1.6. Review Instance Launch settings
Review and check all the settings for Instance Launch, and if all is OK click the Launch button.
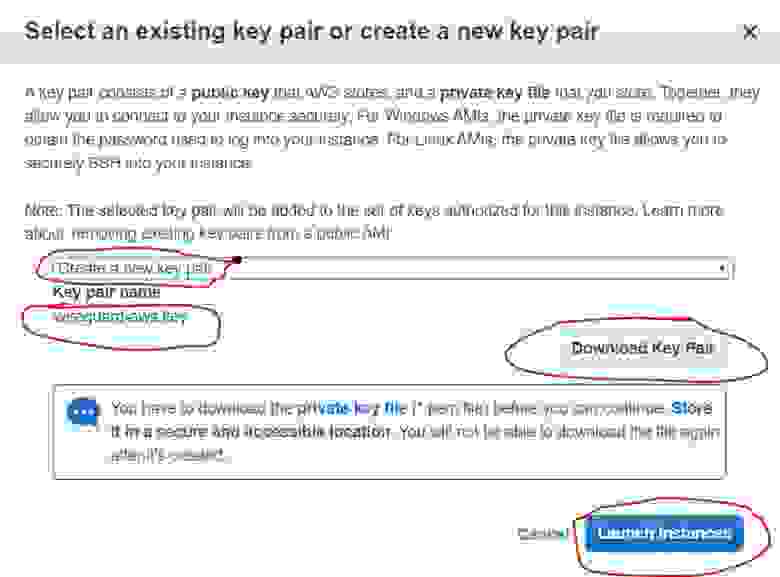
2.1.7. Creating access keys
Create or add an existing SSH key in the dialog box that you will use for remote connection to your instance.
Choose the «Create a new key pair» to generate a new key. Give it a name and click the Download Key Pair button to download the generated key to the PC drive. Click the Launch Instances button.
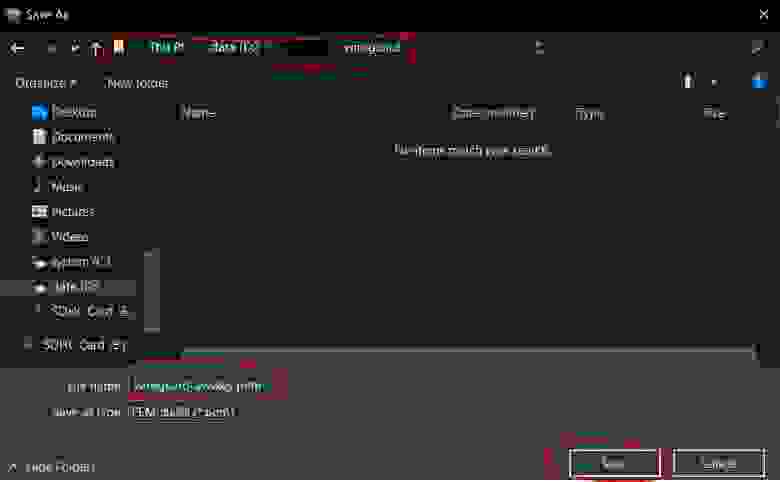
2.1.7.1. Save private keys (.pem)
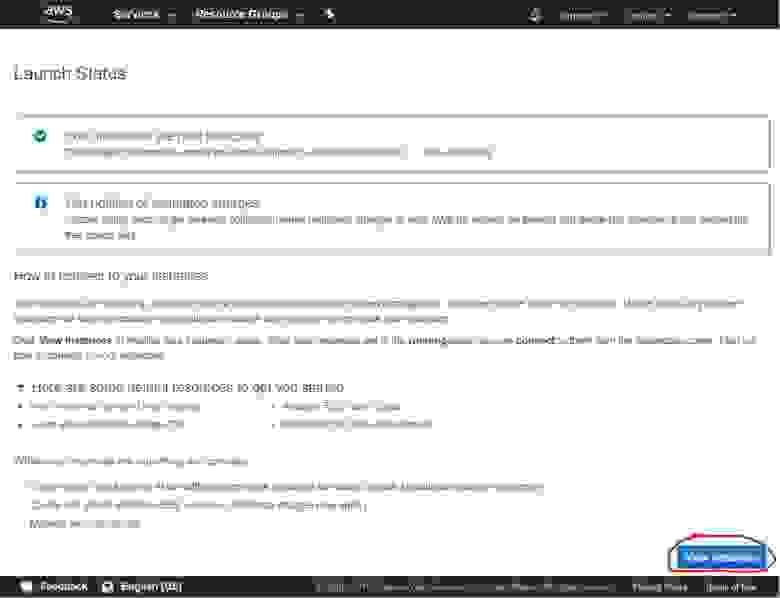
2.1.8. Instance Launch Summary
Next, you should see a message about the successful launch of the Instance that you have created. You can visit the list of your Instances by clicking the View instances button.
2.2. Creating an external IP address
2.2.1. Create an External IP
Next is the creation of an external IP address, that you will use to connect to the VPN server.
Find the Elastic IPs in the NETWORK & SECURITY category of the navigation panel. Click the Allocate new address button.
2.2.2. External IP setup
In the next step you need to enable the Amazon pool (which is by default), and click the Allocate button
2.2.3. IP address overview
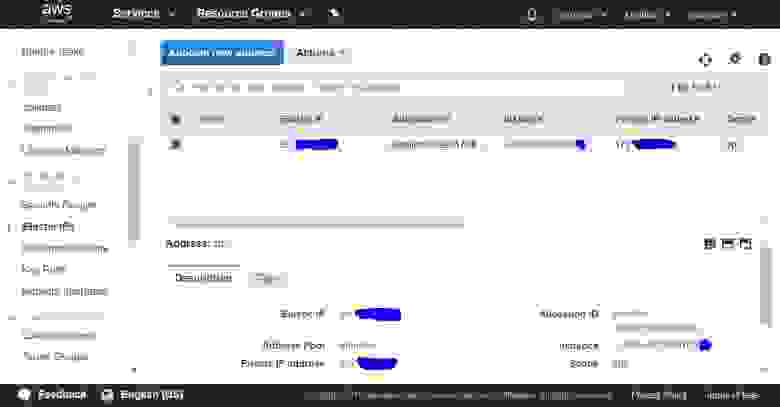
The next window displays an external IP address assigned by the Amazon pool. Write it down, as you will need it fo the configuration process and for VPN server setup. In this guide, as an example, I use the IP address 4.3.2.1.
Once you finish this step, click the Close button.
2.2.4. List of external IP addresses
Next, you should get a list of your public IP addresses (Elastics IPs).
2.2.5. Assign an external IP to Instance
Choose the IP address from the list (see 2.2.3), and click the mouse right button for a drop-down menu.
In this menu choose the Associate address to assign an IP to the created Instance.
2.2.6. Associate address with Instance
In the drop-down menu select the created Instance, and click the Associate button.
2.2.7. External IP assignment Summary
You should now have a created Instance with an assigned public IP address. This enables you to make a remote connection to the Instance from outside (from your PC) via SSH.
3. Connect to AWS instance
SSH is a secure protocol to manage remote computer devices.
3.1. Connect from a Windows PC via SSH
Download and install a Putty to make a connection from the Windows PC.
3.1.1. Import Private Key for Putty
3.1.1.1. Import AWS key into Putty
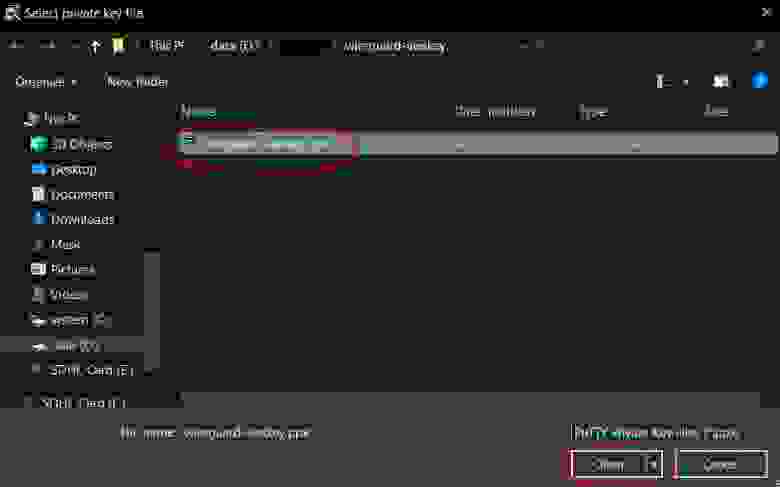
3.1.1.2. AWS key in PEM format
Next, choose the key that you dealt with in 2.1.7.1
In my case it is wireguard-awskey.pem.
3.1.1.3. Set the Key import parameters
At this step, you need to specify the import parameters of the Key — the key comment and the key passphrase. You will need these at every connection. Also it protects the key itself with a password from unauthorized access.
You may skip the password assignment. But this will make your connection less secure in case the key falls into the wrong hands.
Once you finish, click the Save private key button.
3.1.2. Create and configure a connection in Putty
3.1.2.1. Make a connection
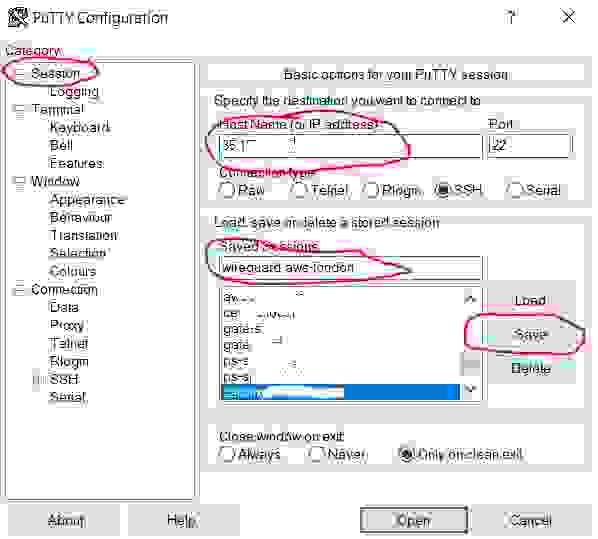
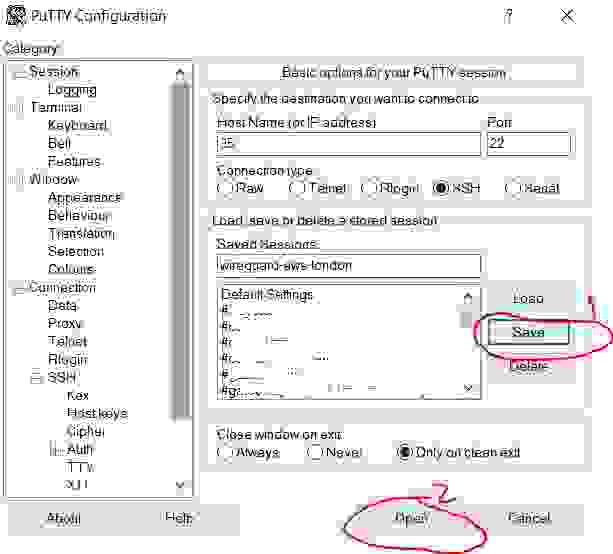
Run the Putty program, choose the Session category (it is open by default) and in the Host Name field enter the public IP address of the server. I remind that you got your public IP address in step 2.2.3.
Give any name to the connection in the Saved Session field (for me it is wireguard-aws-london ). Click the Save button.
3.1.2.2. Set a user auto-login
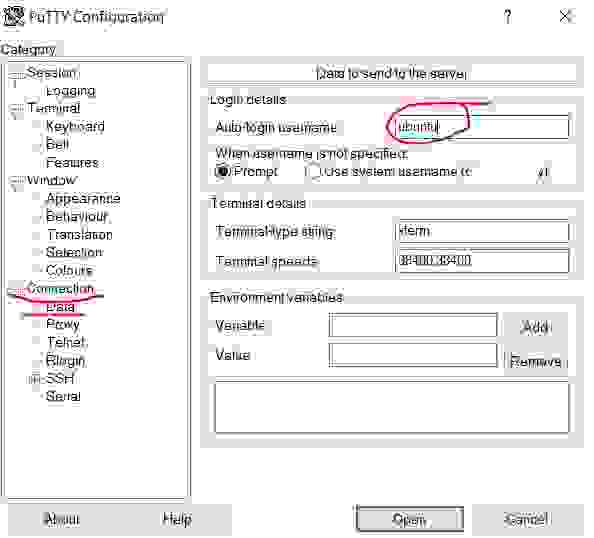
Choose the Data subcategory from the Connection category. Enter the Auto-login username ubuntu in the Auto-login username field. (ubuntu is the standard instance user on AWS with Ubuntu).
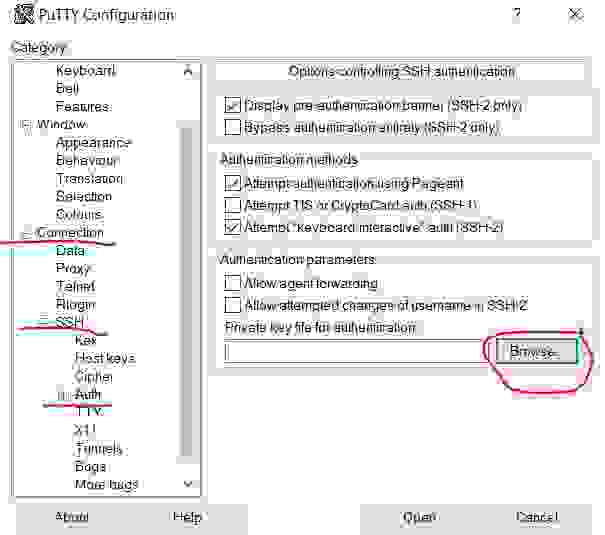
3.1.2.3. Use a private key for an SSH connection
3.1.2.4. Open the private key file
3.1.2.5. Save changes and launch an SSH remote connection
In the Session category of Putty configuration window press the Save button to apply all the changes you made in (3.1.2.2 — 3.1.2.4).
Click the Open button to launch the ready-to-go SSH remote connection.
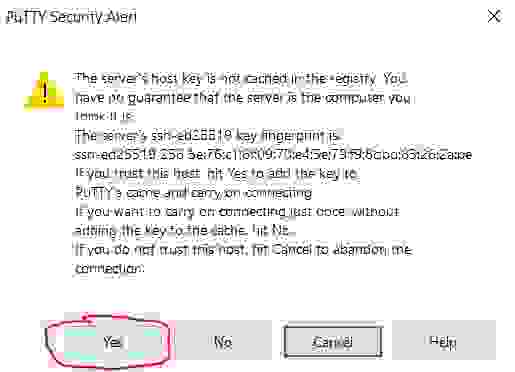
3.1.2.7. Set a trust between hosts
At the first connection, you should get a warning about the lack of trust between two computers (hosts). The system asks you whether you trust the remote host. Click Yes to add the remote host to the trust list.
3.1.2.8. Enter the password to activate the key
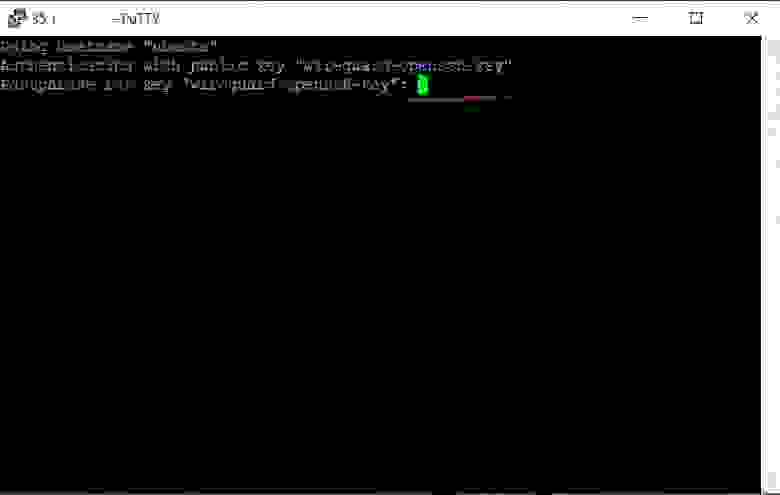
In a Putty terminal window enter the key password you set in step
3.1.1.3. When entering the password it does not show any action on the screen. No worries, if you make a mistake, you can use the backspace key.
3.1.2.9. Successful connection
Once you enter the correct password, you should get a welcome text. It informs you that the remote system is ready to execute your commands.
4. Configure Wireguard server
Below is the instruction for a script-driven Wireguard installation and management.
I keep the latest version of the instruction in the repository: https://github.com/pprometey/wireguard_aws
4.1. Install Wireguard
Enter the following commands in the Putty terminal.
You can copy them to the clipboard, and paste in the terminal by pressing the right mouse button.
4.1.1. Clone the scripts repository
Clone a Wireguard installation scripts repository:
4.1.2. Directory of scripts repository
Go to the directory of the cloned repository:
4.1.3 Initialization script
Run the Wireguard installation script under admin (root user) rights:
The script asks you to provide the following data to configure Wireguard.
4.1.3.1. Set connection endpoint (IP:port)
4.1.3.2. Set internal IP address
Enter the IP address of the Wireguard server in a secure VPN subnet. If you do not know what it is, press Enter key to set the default value ( 10.50.0.1 ).
4.1.3.3. Specify DNS Server
Enter the IP address of the DNS server, or press Enter key to set the default value 1.1.1.1 (Cloudflare public DNS).
4.1.3.4. Specify WAN Interface
Enter the name of the external network interface. This interface will sense the internal network interface of the VPN.
Press Enter to set the default for AWS ( eth0 )
4.1.3.5. Specify customer name
The Wireguard VPN server cannot start until you add at least one client. Enter a VPN username.
In my case, I entered Alex@mobil name.
After that, you should receive a QR code of an added client configuration. This QR applies the user config to Wireguard mobile client on Android or iOS.
The text of the configuration file is also displayed with QR. You will need in case of manual configuration of clients as discussed below.
4.2. Add new VPN user
To add a new user, you need to run the script add-client.sh in the terminal
The script asks for the username:
The username can go along as a script parameter (in my case, the username is Alex@mobile):
4.2.1. User configuration file
the result of command execution as follows:
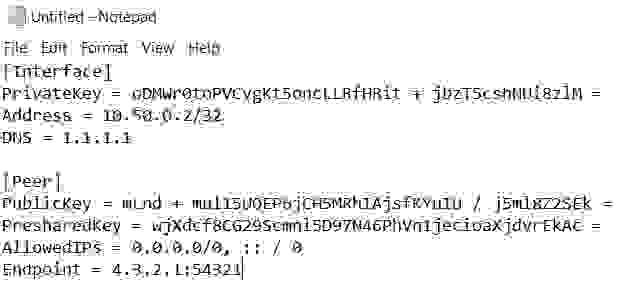
description of client configuration file:
4.2.2. Client configuration with QR code
5. Configure VPN Clients
5.1. Android mobile Client setup
Download the Wireguard mobile client for Android from the official GooglePlay store.
Scan the QR code to import the client configuration (see 4.2.2) and assign it a name.
After importing the configuration, you can enable the VPN tunnel. A little key symbol in the Android system confirms the VPN connection.
5.2. Windows Client Setup
Download and install the TunSafe, which is a Wireguard client for Windows.
5.2.1. Create a local text file to import configuration
Create a dummy text file on the desktop of your PC.
5.2.2. Copy the configuration file from the server
Copy the contents of the configuration file from the server.
Then, go back to the Putty terminal and display the contents of the user configuration file (see 4.2.1).
Use right-click of the mouse to copy the configuration text in the Putty terminal.
5.2.3. Paste the configuration text to a local text file
Paste the configuration text from the clipboard to dummy text file we created earlier on the desktop (see 5.2.1).
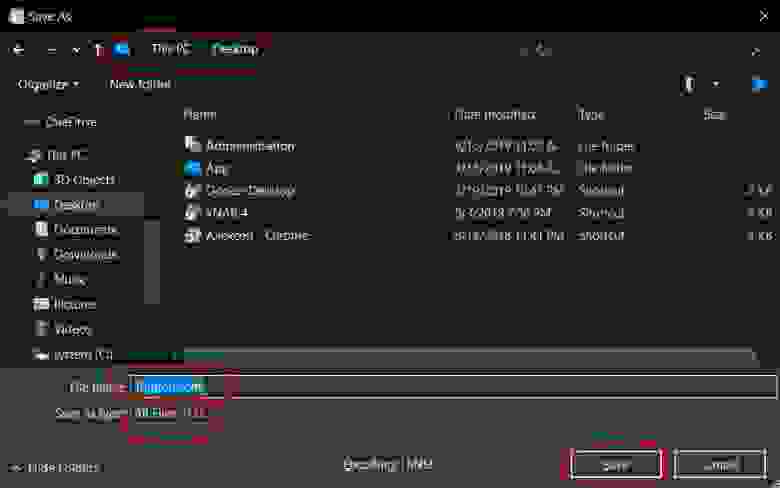
5.2.4. Save the local configuration file
Save the text file as the .conf format (in my case as london.conf )
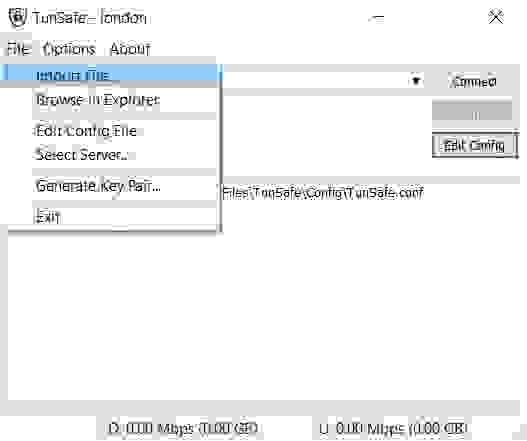
5.2.5. Import local configuration file
Import the configuration file into the TunSafe program.
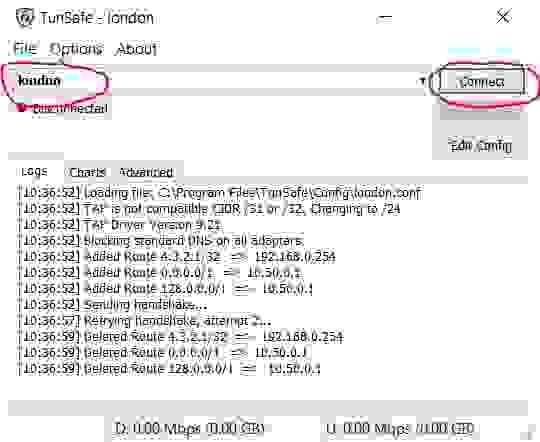
5.2.6. Establish a VPN connection
In TunSafe program select the imported configuration file and click the Connect button.
6. Verify VPN connection
Use https://2ip.ua/en/ resource to verify the VPN tunnel connection. If the displayed IP address matches the one we got in 2.2.3, so the VPN tunnel is up and running.
In a Linux terminal, you can check your IP address by executing the following command:
Securely tunnel smart phone traffic with WireGuard and OpenBSD
Posted on October 18, 2020
Table of Contents
Purpose
Learn how to securely tunnel smart phone traffic over a WireGuard VPN with an OpenBSD 6.8 endpoint using the newly released in-kernel wg(4) driver with only base utilities.
Introduction
Why tunnel internet traffic?
When you browse the internet, check emails, use social media, etc. on your laptop or smart phone, the traffic must go from your device, through the local network, then through the wider internet until it ultimately reaches the destination server. Whoever runs the local Wi-Fi or cell network can see what websites you visit, and if the connection to the website is not encrypted, exactly what you are sending and receiving from the site. Further, if the Wi-Fi network is not encrypted (an open insecure network with no password), then any user on the network can also read your traffic!
One way to keep your browsing and activity private and secured from the people on the local network is to tunnel it through an encrypted Virtual Private Network (VPN). I commonly do this when using public Wi-Fi at airports, libraries, restaurants, etc. to secure my internet traffic from potential eavesdroppers. Ways to obtain a VPN include buying one from a commercial VPN provider, but this shifts the issue of who can look at your traffic from people on the Wi-Fi to this provider. Instead, I setup my own VPN (using WireGuard) on a virtual private server (VPS) that I own on Vultr that runs on OpenBSD, my favorite operating system.
What is WireGuard?
WireGuard is becoming the go-to software to create a VPN. Compared to common alternatives (OpenVPN, IPsec) it is simpler, faster, and uses modern cryptography (making it arguably more secure). OpenBSD has had user-land support for WireGuard using WireGuard-go. OpenBSD 6.8 was released today (2020-10-18) and now includes an in-kernel WireGuard implementation wg(4). Being in-kernel, this implementation is faster. It also means we can skip using extra software and use base-only utilities for simple, easy configuration.
What will things look like at the end?
Your smart phone will enable the VPN through one-click on the WireGuard app. All traffic on your phone will then go over an encrypted tunnel to the OpenBSD endpoint server, after which, it will route to the rest of the internet. This will protect your traffic from anyone snooping on the Wi-Fi or cell network.
OpenBSD Configuration.
Below shows configuration for an OpenBSD server to be a WireGuard endpoint. All instructions below pertain to OpenBSD 6.8 released on 2020-10-18.
Network setup
Below will set-up some background configuration to allow tunneling of packets and configure the firewall:
Enable internet protocol (IP) forwarding
This will allow packets to move between the WireGuard interface and the egress interface.
First enable it on the running system:
Then make it be enabled after system reboot:
Configure OpenBSD’s firewall/packet filter, pf(4) to open the port for WireGuard, allow traffic between WireGuard peers, and forward tunneled traffic from the client to the internet. To do so, add the following lines to your pf.conf(5):
WireGuard Configuration
Previous to OpenBSD 6.8, configuration required the wireguard-tools packages. Now that WireGuard is in base, we can do all configuration with base utils. This is all nicely documented in the manual pages ( wg(4), ifconfig(4)) and summarised below:
Set-up wg0
Generate a end point private key
WireGuard uses a Curve25519 key that is 32 bytes in length and base64 encoded. A Curve25519 key needs 5 particular bits to be configured in a certain way to valid, but wg(4) can correct this from any randomly generated 32 bytes. Therefore, we just need a 32 bytes random base 64 encoded string and can use openssl(1) for that:
Bring up wg0 interface
Save end point public key
Bringing up the wg0 interface generates a public key from the private key. You will need to give this public key to the client (your laptop, smart phone etc), so save it for now:
Assign wg0 an IP address
This IP address will be the IP address your endpoint will have on the VPN. The OpenBSD endpoint will be reachable at 10.0.0.1 by clients (smartphone, laptop, etc) which will also be on the 10.0.0.0/24 subnet. I recommend picking an ip address range randomly to prevent any collision between a network you may join and your WireGuard network (eg 10.12.24.0/24). To keep things simple for this tutorial I’ll just use 10.0.0.0/24 subnet and give the end point the first IP address:
wg0 is now set up and functional.
Generate public/private key pair for client
Below is a bit of a hack so we can use base utilities only. It brings up a temporary wg interface with a generated private key just so we can extract the generated public key.
Generate a client private key
Bring up wg1 interface
Note, I’m picking a different port (this can be whatever you want) since wg0 is already up on 51820.
Save client public key
You will need to use this public key on the OpenBSD endpoint in order for the client to connect.
Remove the temporary wg1 interface
This will remove the temporary interface we created to extract keys:
Finalize setting up OpenBSD Endpoint
Now that we have the client’s public key, we can establish a WireGuard peer on the endpoint to allow the client to connect:
This will limit the IP address of the peer to 10.0.0.2. Changed the IP address to the IP address you would like on the subnet you picked.
Enable configuration to persist on reboot
With the above instructions, your endpoint works. However, it will not work once you reboot the operating system. Save this configuration with the below text in /etc/hostname.wg0 :
Make sure the permissions for /etc/hostname.wg0 are correct so users outside of root and those in the group wheel cannot read the keys:
Now, after a reboot OpenBSD will bring up the WireGuard endpoint for you automatically.
Smart phone configuration
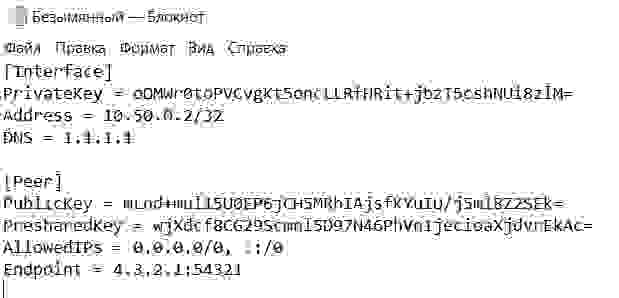
With the endpoint set-up, now you just need to configure your smart phone to use the tunnel. The authors of WireGuard provide apps for both Android and iOS. These applications make configuration easy. You just need to take a photo of a QR code made from a client.conf that you can write on your computer. The client.conf should have the following contents:
Next, generate a qr code with this information using the libqrencode package. If you do not want to install a package outside of base, you can enter the above info by hand into your phone instead. Then do the following to create the code:
If you have issues taking a photo from the QR code generated in your terminal, you can also save it as an image and take a photo of the image.
Open your WireGuard application and take a photo of the QR code, and the app is now configured! Toggle the switch in the app to turn it on. To verify it is working, go to a website like icanhazip.com to see your IP address. It should change when the WireGuard tunnel is up to the same address as your OpenBSD end point.
Once everything works, if you want, you can delete the key files and client.conf:
Enjoy securely tunneling your traffic with WireGuard!
Optional DNS Resolver
You can additionally setup unbound(8), to serve as a DNS cache and resolver. This will allow you to guarantee that your DNS queries are tunneled to your Wireguard server then sent to your preferred upstream DNS resolver. By setting up unbound, you also cache your DNS requests for some added speed compared to specifying a dedicated public resolver.
Credit goes to David Robert Newman for this part who suggested adding a DNS line to the client configuration.
To do so, you need to:
Setup unbound
Add DNS cache to wireguard config
This is easy, you just need to add a DNS line to your client configuration:
Comments, questions, input, concerns?
Please contact me with any questions or input on the article using any of the methods on my contact page.
Built with Zola & running on OpenBSD.
© 2020-2022 Thomas Ward. All work licensed under CC BY 4.0 unless otherwise noted.
psyhomb/wireguard-tools
Use Git or checkout with SVN using the web URL.
Work fast with our official CLI. Learn more.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
Full documentation about manual Wireguard installation and configuration process can be found here.
This script is created to ease manual process of Wireguard configuration and will help you to automatically generate all the required configuration files (client and server), PKI key pairs and preshared key.
Arch
Ubuntu
MacOS
Make sure to append following line to wgcg.conf file only if using MacOS.
By doing this we will force script to use GNU instead of BSD command line utilities (e.g. grep ) and prevent any possible incompatibility issues.
Copy wgcg.conf configuration file to wgcg directory.
Copy wgcg.sh script to /usr/local/bin directory.
It is also possible to specify custom configuration file by passing WGCG_CONFIG_FILE environment variable.
Print help and current default options.
wgcg-install-wireguard.sh module will do all required system preparations on the WireGuard server (running the module is idempotent operation):
Note: You have to run it only once!
Generate server keys and config.
Generate client config, PKI key pairs and update server config (add new Peer block)
or to generate multiple client configs at once, create client-configs.csv file
Global rewrite action mode
or per client line.
Note: It is also possible to protect individual client from regenerating config and key files by specifying norewrite action.
Remove client config, PKI key pairs and update server config (remove Peer block).
Synchronize local server configuration file with server (live update).
In order to send client configuration file to a person safely, you can use GPG symmetric encryption to encrypt data before sending it, then you can send configuration file to a person via one channel (webwormhole) and passphrase via different channel (ots).
Encrypt configuration file.
To test passphrase just run decrypt command, if everything is OK client configuration will be printed out on the standard output.
It is also possible to manage multiple clusters with single script.
Create configuration file and command alias for every cluster.
Note: Append following lines to
It is also possible to run the script inside of Docker container with already preinstalled dependecies.
Wireguard Android Client Setup [2022] – Simple and Secure VPN
Looking to setup Wireguard Client on Android? This step-by-step Wireguard Android client setup guide is exactly what you need.
Wireguard VPN as a protocol is a bit different than a traditional VPN. If you are new to it, I strongly suggest reading my Wireguard introduction for beginners.
In my Wireguard setup articles, I use the «server» and «client» terminology to simplify our understanding and make the transition to this idea a bit more comprehensible. The truth is, that Wireguard as a protocol simply creates secure «tunnels» between peer devices. How we interact with these tunnels, and how those tunnels connect is what gives Wireguard its flexibility.
Previously, I described Wireguard Mac OS client setup. In this post, let us look at how to setup Wireguard client on Android and configure it.
Table of Contents
Wireguard Android Client Setup
Other Posts in the Wireguard Series:
1. Install Wireguard Android App
Following the directions listed on the Wireguard website, download and install the Android Wireguard app via the Google Play Store or F-Droid App.
Launch the newly installed app, and we are greeted by an empty Wireguard window.
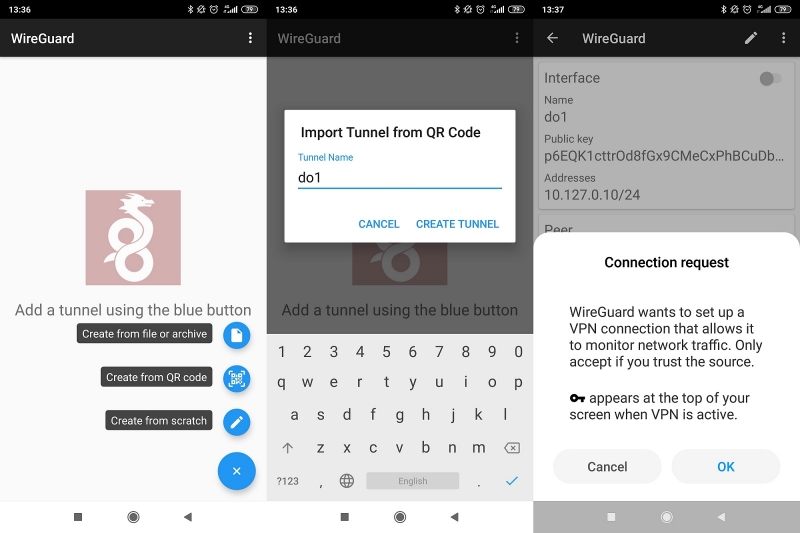
2. Create the Local Wireguard Adapter
Wireguard works by creating a virtual adapter to route your traffic through. There are 2 ways to connect your Android device as a client to a Wireguard server. Both require a set of configurations which can either be delivered to you as a single file/QR Code, or created through the Wireguard Android App itself. Let’s look at both ways.
Option 1a: Importing a Given Configuration via QR Code
QR Codes are a simple way to visually represent data. They are designed in such a way that cameras (along with basic software) can easily decode the data into something we recognize. This is often used to encode URL’s. For example: the website address of a menu at a restaurant might be QR encoded so you can just take a photo and get the URL to avoid typing in a long website address by hand.
Generate the QR Code
In our case, the Wireguard config file is simply a bunch of text in a small file. If we want to import the config to our Android phones from say a Linux server (or computer), we just need to install a QR encoding software and pass the config into it. For example, on an Ubuntu machine we would need to:
This will output a large QR code in your terminal. Leave it open while we import it from the Android device.
Scan the QR code into the Android Wireguard App
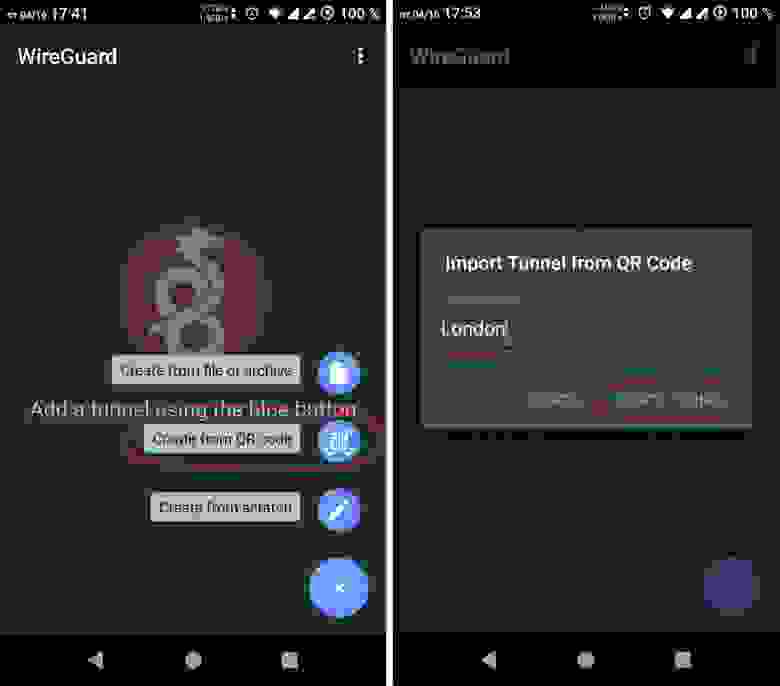
Now onto the Android device. As instructed, click the big blue (+) button in the bottom corner of the screen. Select «Scan from QR Code«:

If you haven’t yet given the Android Wireguard App permission to use the camera, you might get a security pop-up. When in doubt, select «Only this time«:
Your camera should now start. Point it at the QR Code. Make sure that the whole code fits inside the light-colored square on your screen.

Lastly, you are asked to give the newly created tunnel a name. I wasn’t feeling very creative and simply called mine «homeserver«:
Click «Create tunnel» when you are finished and move ahead to activating the tunnel.
Option 1b: Importing a Given Configuration via File
Begin by transferring the config file(s) to your Android device.
Now onto the Android device. As instructed, click the big blue (+) button in the bottom corner of the screen. Select «Import From File or Archive«:

We are greeted with a screen in which we must choose the config file. Navigate to the location it is stored, and open the file.
Edit the Interface (Optional)
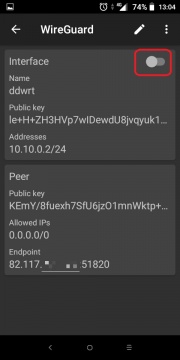
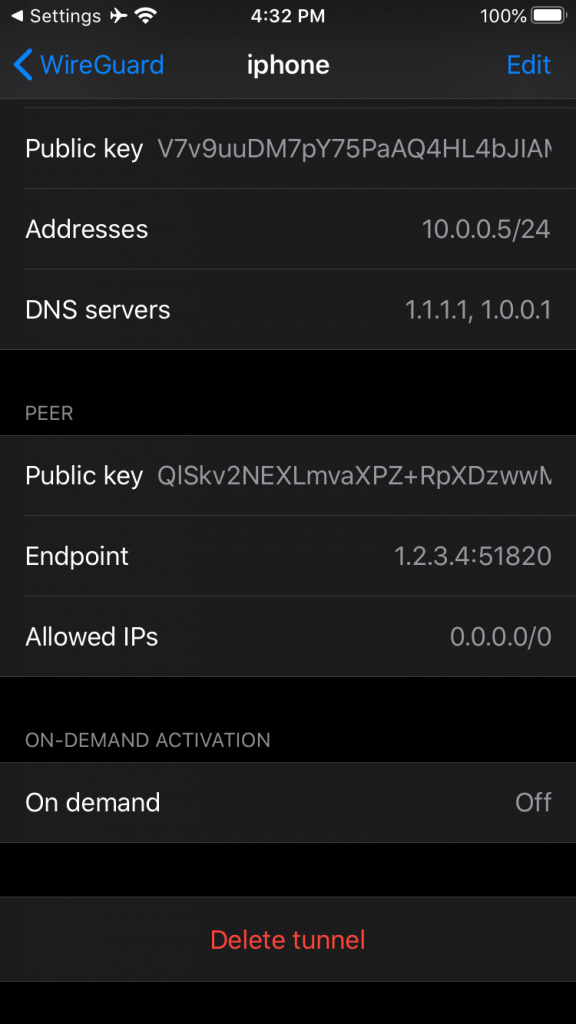
At this point you can click the toggle to the right of the tunnel name to get started. But before we do, let’s click on the name of the tunnel itself to see the details of the adapter. We are now shown a more verbose overview of the tunnel including the configuration settings we imported.
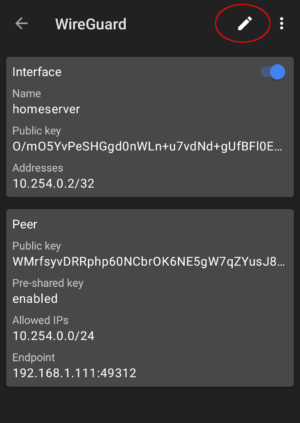
Here we can edit any details including the name if you would like something different than «homeserver». Click the «pencil» icon in the top right corner to begin editing the tunnel.
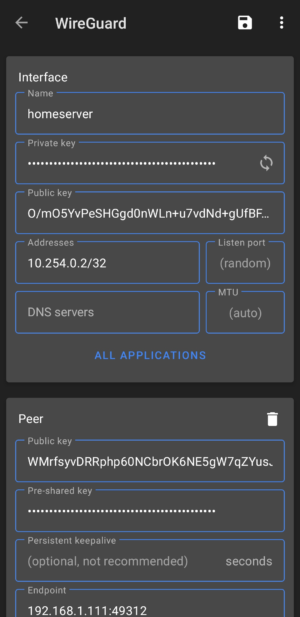
When finished, simply click the ‘Save‘ icon in the upper right corner. Continue to activating the tunnel.
Option 2: Create a Configuration of Your Own
In this scenario, we will create the configuration ourselves, and only pass the «Public Key» to the server to add it as a new [Peer]. You will need, however, a few details from the Wireguard server you intend to connect to: Public Key, Endpoint IP Address and Port, Allowed IP(s).
Create a new tunnel
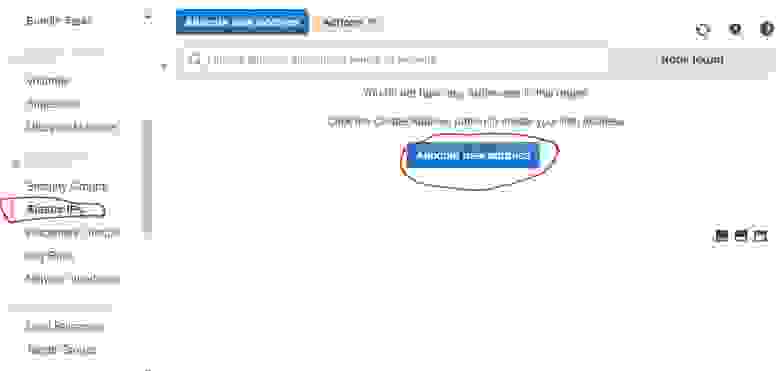
At the bottom of the Android Wireguard app screen, click the plus sign (+) and select ‘Create from Scratch‘:

We are greeted with a new screen.
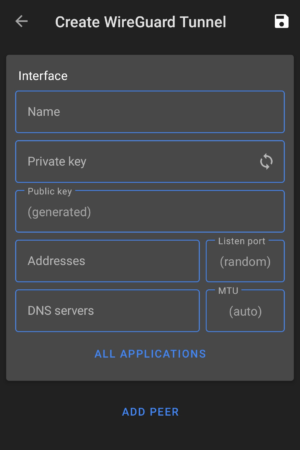
Add Known Information
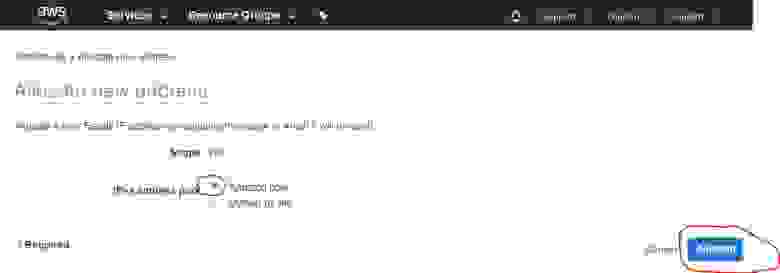
Moving to the next section, we need to add our server as a «Peer». Click the ‘Add Peer‘ heading at the bottom of the screen.
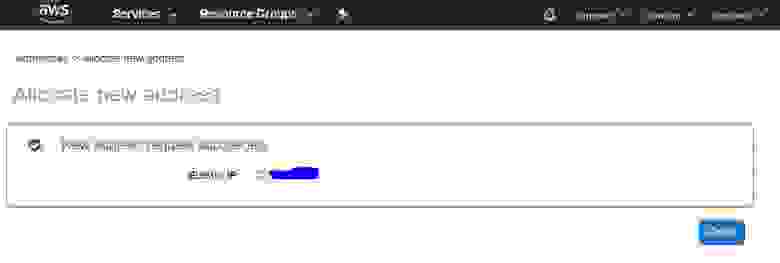
Click the «Save» icon to close the window.
3. Add Client Details to your Wireguard Server
Now that the Android Wireguard client is set, the few details need to be shared with the machine hosting the Wireguard VPN server. The client has to be added as a peer on the server. This has been described in our Linux Wireguard server guide.
At the very least, the server will need your client’s Public Key and Address. Once added to the server, we can continue!
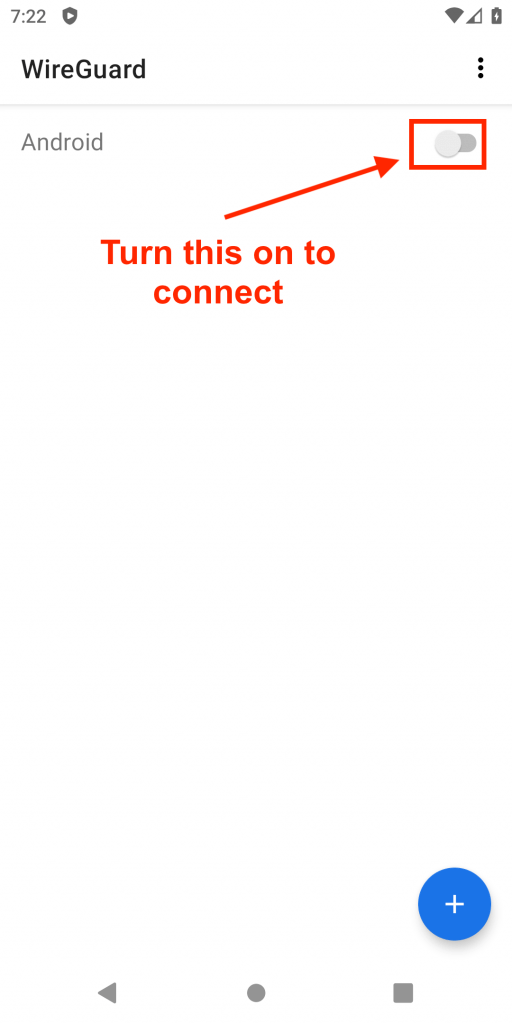
4. Activate the Tunnel!
Click the gray toggle switch to the right of the tunnel name and after a second or so you should see the toggle change to blue and a new «key» icon should appear in the upper notification bar.
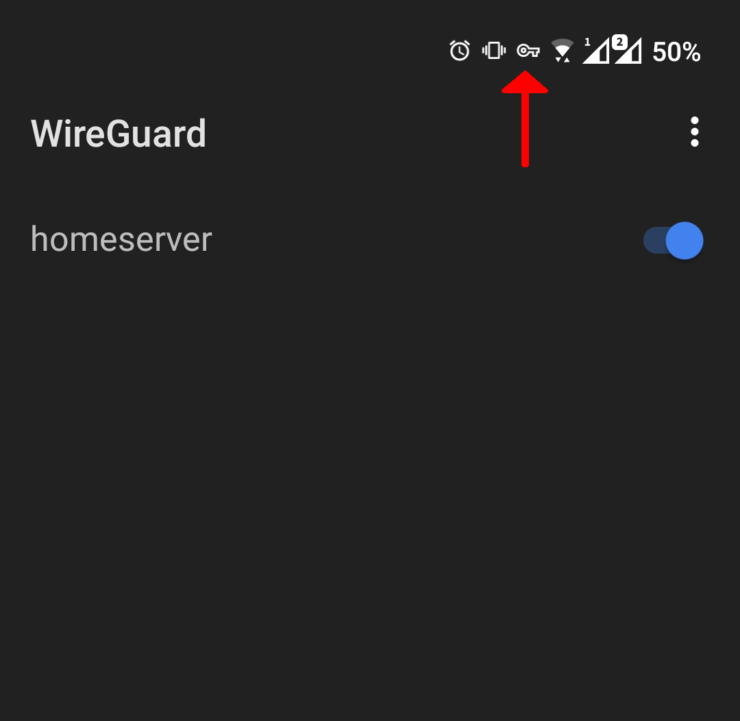
Test Your Connection
You can test to make sure your connection is working a few different ways. As Android is roughly based on the Linux kernel, we can use the same Terminal command ping. An example of an app that can act as a Terminal is Termux. In this case, since our server is running on IP address 10.254.0.1, we can simply ping the address and look for a response:
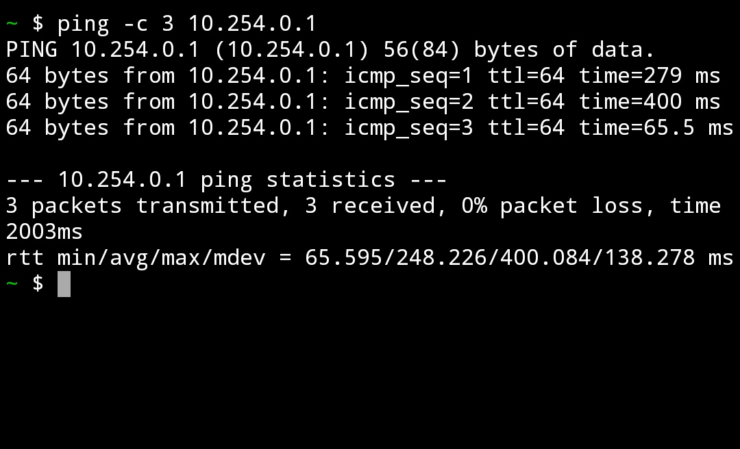
I had also setup a Jellyfin instance on my Wireguard Server to test with, and was easily able to access it using the Wireguard server IP:

Access Additional Local Resources
The setup above allows you to connect directly to your Wireguard server and access anything running on it. If you have IP forwarding setup on the server, you can also access other Wireguard peers who are connected to the same Wireguard server.
However, we might have other devices on the a local network that the Wireguard server is part of. To connect to those, we simply need to modify our interface just slightly so that the Android device knows to pass requests to those IP’s through the Wireguard tunnel (and not directly to the local network you are currently using).
The ‘AllowedIPs’ Section
Let’s say I have an additional device on my home network that isn’t attached directly to my Wireguard server; a Raspberry Pi running my Nextcloud server. It is running on our home network with the IP address 192.168.124.109.
Currently, we are at Friend’s house, and we type that address into our browser. Our Android device would not be able to find the Nextcloud server. This is because 192.168.124.109 isn’t included in the AllowedIPs section of our Wireguard interface. Our browser looks for the device in Friend’s network instead of through the Wireguard tunnel to our home network. Let’s modify our ‘AllowedIPs’ to make sure the request is passed through Wireguard:
Edit Our Wireguard Client Adapter Settings
Open your Android Wireguard App and edit the tunnel. Let’s add the IP of our Raspberry Pi at home: 192.168.124.109.
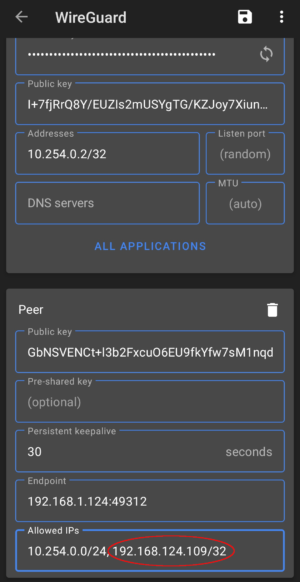
Click the ‘Save‘ icon in the upper right corner. We will see the a message at the bottom of the screen saying it was successfully saved.
Head to your browser (or app) and now we type in the 192.168.124.109 address to see if we can reach our Nextcloud.
User Defined DNS servers
This section applies to anyone using Pi-Hole/AdGuard Home or who wishes to set custom DNS for their Android device. If you decide not to route ALL of your traffic (described below) through your Wireguard server, you can still add DNS servers to your config. In this example, we add a declaration using Cloudflare’s DNS servers.
Open your Android Wireguard VPN App, and edit the tunnel. Add the following in the DNS servers box:
Your finished client configuration should look like below:
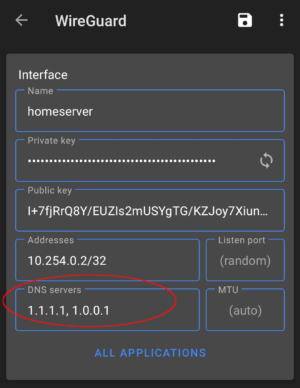
Click the ‘Save‘ icon and you will see a message at the bottom of the screen confirming the successful configuration change.
I wasn’t able to verify via Termux that the new DNS servers were in fact the ones being used due to a ‘feature’ of Termux. Termux by default uses Google’s DNS servers regardless of the device’s settings, leading you to believe it didn’t work properly. So digging around the internet for a few minutes showed me an app that can help called Network Info II.
Another easy way to verify is by using a DNS leak testing site like https://dnsleaktest.com.
Route All Traffic Through Wireguard Server
Routing all traffic through our Wireguard server is generally quite easy to accomplish from the Android Wireguard App. Open your Android Wireguard App, and edit the tunnel. Next we change AllowedIPs to 0.0.0.0/0.
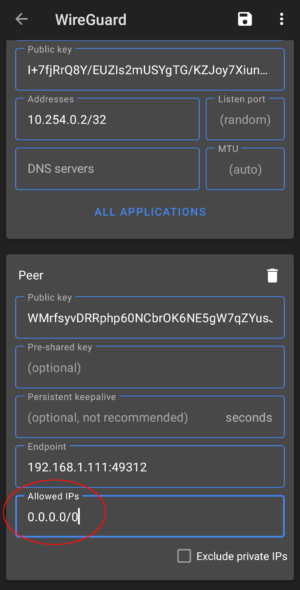
Excluding Private IP Ranges
Why can’t I connect to another device?
Can I have more than one Wireguard tunnel active at a time?
Some digging into the Wireguard Android code repository makes it look like it should be possible. However, it might not be available to non-rooted devices. No matter my settings, I was unable to get it to work (using the F-Droid version).
If your device is rooted you might be able to run multiple simultaneous tunnels as long as the address ranges do not overlap.
If rooted, using the Termux app, you can install the wireguard-tools package which will give you access to the wg-quick command. This should work the same as it does in the Linux clients and allow you to bring ‘up’ as many tunnels as you like.
How do I add better security with a Preshared Key?
While not strictly necessary, the Preshared Key adds a layer of security to better protect our tunnel against attacks by advanced threats. Again, not strictly necessary but easy to add in my opinion. The generated key will need to be included in both the server’s config file and in your Wireguard Android App.
Preshared Key Generated from Wireguard Server
If your Preshared Key was generated from the server, securely copy it to your Android device. Open your Android Wireguard App, and edit the tunnel. We will add it in the ‘Pre-shared key‘ box under the Peer section.
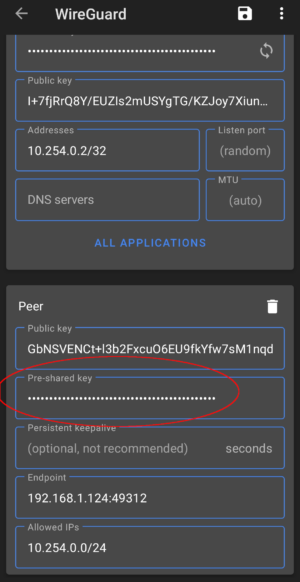
Preshared Key Generated on Android
To generate one from your Android you must use the CLI version of Wireguard. To use the CLI, you must install the wireguard-tools package. I installed it using Termux (as linked above) and installed the package with:
This next part follows the Wireguard Linux article, so I will not go in depth. The short version is to use your terminal to generate a Preshared Key (PSK), copy it into both your Android Wireguard App (shown above), and into the server config.
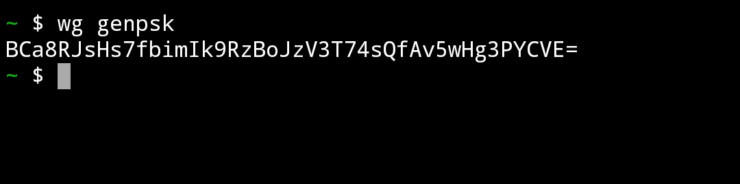
Can I use Wireguard for Android with IPv6?
Absolutely. Anywhere you see an IPv4 address, you can add a valid IPv6 address as well. Make sure your server can handle IPv6 requests or you might have trouble with the Wireguard tunnel.
How do I export my config if I generated it myself?
Why can’t I connect to the Internet after starting my Wireguard tunnel?
As the joke goes. «It’s Always DNS». If using 0.0.0.0/0, double check your server is able to resolve domain names (server is connected to the internet). Double check to see if your config settings were entered properly (like mixing keys). Try setting a DNS server as stated earlier in this article. You can also set it to the IP of the server itself if you have something like unbound running.
How do I Include/Exclude an app from using the Wireguard tunnel?
Open your Android Wireguard App, and edit the tunnel. Click on the «All Applications» button at the bottom of the Interface frame. Here you can select to allow/exclude certain apps from using the tunnel.
How can I automatically disconnect the tunnel when I am home, and automatically connect when I leave?
The Wireguard Android App doesn’t have this feature natively included (as of this writing). I haven’t tried it myself, but a common recommendation is using the Tasker App to automate actions based upon triggers (like joining/leaving a specific WiFi SSID).
Concluding Thoughts
The Wireguard for Android App is a great compliment to the family of Wireguard applications. I find it to be user friendly, but is lacking a bit if you install it with no other notion of how the Wireguard VPN protocol works.
Either way, I appreciate the simplicity and flexibility it offers while abstracting the more complex aspects of VPN’s. Wireguard has simplified the VPN setup process so much most enthusiasts and homelab beginners can now implement it easily.
Related Posts:
Kristopher
Kristopher is a tech enthusiast interested in teaching and simplifying technology for others. Online privacy and responsibility has become of upmost importance and he aims to help others reduce their reliance on tech giants.
burghardt/easy-wg-quick
Use Git or checkout with SVN using the web URL.
Work fast with our official CLI. Learn more.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
These instructions will get you a copy of the project up and running on your local machine. This machine (called hub) will act as VPN concentrator. All other peers connects to hub (as in a «road warrior» configuration).
Install Wireguard for your operating system on local machine, router, VPS or container. This will be your hub.
Fedora, RHEL, CentOS
Installing Wireguard tools (and modules)
This script requires only tools installed, but to use Wireguard module (or user-space implementation) is also required. Detailed install guide for various operating systems is available at wireguard.com/install.
Peers also requires Wireguard installed. Android and iOS are supported. OpenWRT clients are supported with UCI configuration fragments.
Note that you can use a short URL as well.
Or clone repository.
Script do not require any arguments. Just run it and it will create usable Wireguard configuration for hub and one peer. Any sequential invocation creates another peer configuration within same hub.
Passing an argument to script creates configuration file with name instead of sequence number to help remembering which config was for which device. Following command will create wgclient_client_name.conf file.
Using generated configuration
On hub configure Wireguard.
Or use saved QR code
To connect the whole network with a single Wireguard client running on an OpenWRT router, append generated UCI client configuration fragment to your router /etc/config/network file.
Disabling external interface autodetection
By default easy-wg-quick use interface with default routing done over it as external network interface of VPN hub. If autodetection fails or generation of configuration is done outside the hub (i.e. on air gapped laptop) user can set interface name in extnetif.txt file with command:
Disabling external IP address autodetection
By default easy-wg-quick uses IP address of interface that has default routing done over it as external IP address of VPN hub. This might not be true if hub is behind firewall or NAT/PAT/masquarading is done. User can set prefered IP address in extnetip.txt file with command:
In case of NAT/PAT/masquarading one can try to use service like ifconfig.co for autodetection:
Disabling random port assignment
By default easy-wg-quick use random port number from range 1025-65535. When using static port number is required for firewall configuration or other reasons user can set preferred port number (80 in this example) in portno.txt file with command:
Disabling randomly generated internal network addresses
By default easy-wg-quick use randomly generated internal network addresses for both IPv4 and IPv6. Custom network addresses can be set with the following commands.
Default masks are /24 for IPv4 and /64 for IPv6.
Setting network masks
To change default masks set new masks in files named intnetmask.txt (IPv4) and intnet6mask.txt (IPv6).
Setting interface’s maximum transmission unit (MTU) size
Setting custom DNS
Setting IPv4 resolver address
By default easy-wg-quick uses 1.1.1.1 as it’s internal DNS. You can use the command below to serve a custom IPv4 DNS to clients.
Setting IPv6 resolver address
By default easy-wg-quick uses 2606:4700:4700::1111 as it’s internal DNS. You can use the command below to serve a custom IPv6 DNS to clients.
Setting custom client’s AllowedIPs
Choosing firewall type
Firewall type is guessed from operating system. For Linux iptables and ip6tables are used. For FreeBSD basic pf NAT rules are implemented. File fwtype.txt contains name of firewall type. To override autodetection or disable any rules run one of the following commands:
If fwtype.txt contains word custom content of commands.txt is included in the wghub.conf file.
Format of commands.txt is:
Choosing if PostUp/PostDown should enable/disable IP forwarding
Sysctl command syntax is guessed from operating system. Linux and FreeBSD are supported. As enabling IP forwarding is required for hub to forward VPN traffic to the Internet it is managed by PostUp/PostDown settings by default. Some application (i.e. Docker) might require that IP forwarding is never disabled. In that case setting none in sysctltype.txt and managing IP forwarding settings elsewhere might be required.
File sysctltype.txt contains name of sysctl type. To override autodetection or disable any commands from being run use one of the following commands:
If a global unicast IPv6 address is detected on server tunnels will be created with inner IPv6 addresses allocated. This allows hub’s clients to connect over hub’s IPv6 NAT to IPv6 network.
If a global unicast IPv6 address is not detected, the existence of a file named forceipv6.txt can forcibly enable IPv6 support.
To use outer IPv6 addresses (i.e. connect client to hub over IPv6) just set EXT_NET_IF and EXT_NET_IP variables in script to external network interface name and IPv6 address (or edit wghub.conf ).
Enabling NDP proxy (instead of default IPv6 masquerading)
By default easy-wg-quick uses IPv6 masquerading to provide IPv6 connectivity to peers. This is easier to setup and require only single IPv6 global unicast address to work. On the other hand network address translation (NAT) has issues and limitations.
Neighbor Discovery Proxies (ND Proxy, NDP Proxy) allows end-to-end connectivity, but requires /64 network to be assigned to hub. From this /64 network, a subnetwork has to be divided (i.e. /112) and assigned to Wireguard interface.
To enable proxied NDP create file named ipv6mode.txt with proxy_ndp string.
When hub has 2001:19f0:6c01:1c0d/64 assigned, part of it can be assigned to Wireguard interface (i.e. 2001:19f0:6c01:1c0d:40/112).
Please note that NDP proxy mode in easy-wg-quick is supported only on Linux.
On Linux clients setting the same should improve the fairness of upload flows.
Persisting configuration with systemd
OpenVPN’s easy-rsa was an inspiration for writing this script.
About
Creates Wireguard configuration for hub and peers with ease
suquant/wgrest
Use Git or checkout with SVN using the web URL.
Work fast with our official CLI. Learn more.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
WGRest is a WireGuard REST API server. It operates wireguard through IPC and doesn’t require any dependencies. It aims to be simpler, faster, and usable on embedded devices such as routers or any other low power and low memory devices.
WireGuard is a simple and modern VPN. It is cross-platform (Windows, macOS, BSD, iOS, Android).
Wireguard qr code generate
Copy raw contents
Copy raw contents
Generate AllowedIPs Text / QR Code in Terminal For Granular WireGuard® Tunnel Exclusions
Hopefully you know by now, but WireGuard® is an extremely simple yet fast and modern VPN that utilizes state-of-the-art cryptography. You can read more about it here
Generate AllowedIPs Value As Text String or QR Code in Terminal For Granular WireGuard® Tunnel Exclusions
Given a list of IPv4 addresses (dotted quad, CIDR) print an inclusion list ( AllowedIPs string) suitable for the WireGuard® mobile app, optionally generating a QR code using ANSI escape characters in a standard terminal window. Useful for excluding only a partial set of LAN (or WAN) addresses from the WireGuard® tunnel. Currently, the only «easy» option for accessing a LAN is to opt all RFC1918/RFC3330 private addresses out of the tunnel, using the checkbox that the WireGuard® client provides. This script allows a more granular specification, and also allows the specification of specific WAN addresses as well
Quick-Start (See Usage For Detailed Instructions)
Generate a fine-grained AllowedIPs value that excludes only three specific LAN addresses to bypass the tunnel:
This command will generate a QR code which will be printed to your terminal/TTY containing the AllowedIPs value, and will also print a text version
Specific Use-Case (LAN + Security Concerns)
Consider a mobile user with an on-demand WireGuard® VPN connection for the purpose of both privacy and security that needs to access only a small subset of LAN hosts (or WAN hosts) outside of the tunnel. By using fine-grained addresses in the AllowedIPs parameter, this can be accomplished without hassle. The effect:
Natively Supported WireGuard® Options for LAN Access via Tunnel Bypass
One existing and very simple solution is to use the built-in «Exclude Private IPs» option in the WireGuard® mobile app, which generates a fixed list that simply generates an AllowedIPs address list that excludes all RFC1918/RFC3330 Private Addresses. However, this is a very broad range and is not trivial to tweak
Using this rinky-dink little app, you can specify granular exclusions, e.g. 192.168.1.2 192.168.1.3 192.168.1.4 for the WireGuard® tunnel and receive a list of networks suitable for the AllowedIPs
Allowing, e.g., only 192.168.1.2, 192.168.1.3 and 192.168.1.4 (as opposed to 192.168.0.0/16) effectively protects the rest of the 192.168.0.0/16 network from being exposed to the device. It also effectively protects the device from the rest of the 192.168.0.0/16 network (and 10/8 and 172.16/12 as well, if relevant)
Why Is Code Required? Can’t I Just Specify The List Myself?
In case it isn’t already clear, WireGuard® mobile only allows the client to specify IP addresses that are «allowed» to use the tunnel. It is an opt-in system, most easily used when performing a LAN-to-LAN tunnel. It does not allow the user to specify a blacklist- to do this, a long list of «non-blacklisted» networks must be generated. Because of this, you can’t briefly or easily say «all traffic except to/from host 192.168.1.3 should transit the tunnel easily». Instead, you need a list of CIDR notation networks that make up the entire IPv4 address space, excluding «192.168.1.3».
If you’re curious, the value for this specific example looks like this and is rather unwieldy, which is where the QR code functionality comes in handy:
This is a bit much to effectively specify just a single host for tunnel bypass, and is not so simple to construct in your head, unless you’re an advanced human subnet calculator
Caveat Emptor / NOTES
Given a list of dotted-quad and CIDR notation IPv4 networks on the command-line, generate the inverse in the format WireGuard® prefers. Optionally, produce a QR code on the terminal screen that scan be easily scanned into mobile devices
This was written to create an «Allowed IPs» list for the WireGuard® mobile app to allow granular tunnel bypass. WireGuard® currently doesn’t allow you to supply an «Excluded IPs» option, so you have to invert the networks that you want to bypass the tunnel. This overengineered app will do that for you. One very convenient feature is printing a QR code so that the Allowed IPs list will be easy to copy to a mobile device
Use WireGuard® tunnel for all networks except 192.168.1.0/24 and 192.168.2.0/24:
The same, but don’t route IPv6 through the tunnel (note the last network in the output):
Allow only 192.168.1.1 and 192.168.1.2 to bypass the tunnel:
NOTE: When using QR code, the ‘AllowedIPs =’ string literal will not be included in the QR data by design, so that the data can be pasted into the value box on the mobile app IMPORTANT: You may also need to specify the WireGuard® peer address as an exclusion, you should test this
QR Code Support Dependencies
There are two ways to generate QR codes. By default, the script will try to use the qrcode Python module if available. If not available, it will fall back to using the qrencode application if it is present on your system. If neither are found, it will report an error
(RECOMMENDED) Python Package: qrcode
The qrcode is a simple, excellent QR code generation Python package that supports output to terminal windows as well as image files
(RECOMMENDED) Install qrcode via pip
Install qrcode With Your OS Package Manager
This is not recommended as many distributions have dated versions of Python modules in their repositories. The distribution package is probably called python3-qrcode
OS Native / Package: qrencode
Use your distribution package manager to install qrencode
Debian / Ubuntu / Kali
$ sudo apt-get install qrencode
RHEL, Fedora, CentOS
$ sudo yum install qrencode
If you would like to use a different QR code generator, you can change the QR_ENCODE_COMMAND list in the script, or you can add code to use some other Python library. This isn’t recommended
Бесплатный VPN сервис Wireguard на AWS
Для чего?
С ростом цензурирования интернета авторитарными режимами, блокируются все большее количество полезных интернет ресурсов и сайтов. В том числе с технической информацией.
Таким образом, становится невозможно полноценно пользоваться интернетом и нарушается фундаментальное право на свободу слова, закрепленное во Всеобщей декларации прав человека.
Статья 19
Каждый человек имеет право на свободу убеждений и на свободное выражение их; это право включает свободу беспрепятственно придерживаться своих убеждений и свободу искать, получать и распространять информацию и идеи любыми средствами и независимо от государственных границ
В данном руководстве мы за 6 этапов развернем свой собственный бесплатный* VPN сервис на базе технологии Wireguard, в облачной инфраструктуре Amazon Web Services (AWS), с помощью бесплатного аккаунта (на 12 месяцев), на инстансе (виртуальной машине) под управлением Ubuntu Server 18.04 LTS.
Я старался сделать это пошаговое руководство как можно более дружественным к людям, далеким от ИТ. Единственное что требуется — это усидчивость в повторении описанных ниже шагов.
Этапы
Полезные ссылки
1. Регистрация аккаунта AWS
Для регистрации бесплатного аккунта AWS требуется реальный номер телефона и платежеспособная кредитная карта Visa или Mastercard. Рекомендую воспользоваться виртуальными картами которые бесплатно предоставляет Яндекс.Деньги или Qiwi кошелек. Для проверки валидности карты, при регистрации списывается 1$ который в дальнейшем возвращается.
1.1. Открытие консоли управления AWS
Необходимо открыть браузер и перейти по адресу: https://aws.amazon.com/ru/
Нажать на кнопку «Регистрация»
1.2. Заполнение персональных данных
Заполнить данные и нажать на кнопку «Продолжить»
1.3. Заполнение контактных данных
Заполнить контактные сведения.
1.4. Указание платежной информации.
Номер карты, срок окончания и имя держателя карты.
1.5. Подтверждение аккаунта
На этом этапе идет подтверждение номера телефона и непосредственное списание 1$ с платежной карты. На экране компьютера отображается 4х значный код, и на указанный телефон поступает звонок из Amazon. Во время звонка необходимо набрать код, указанный на экране.
1.6. Выбор тарифного плана.
Выбираем — Базовый план (бесплатный)
1.7. Вход в консоль управления
1.8. Выбор расположения дата-центра
1.8.1. Тестирование скорости
Прежде чем выбирать датацентр, рекомендуется протестировать через https://speedtest.net скорость доступа к ближайшим датацентрам, в моей локации такие результаты:
Лучшие результаты по скорости показывает датацентр в Лондоне. Поэтому я выбрал его для дальнейшей настройки.
2. Создание инстанса AWS
2.1 Создание виртуальной машины (инстанса)
2.1.0. Запуск пошагового мастера создания инстанса
2.1.0.1. Переход на страницу запуска инстанса
2.1.0.2. Запуск пошагового мастера создания инстанса
2.1.0.3. Выбор типа операционной стистемы инстанса
2.1.1. Выбор типа инстанса
По умолчанию выбран инстанс t2.micro, он нам и нужен, просто нажимаем кнопку Next: Configure Instance Detalis
2.1.2. Настройка параметров инстанса
В дальнейшем мы подключим к нашему инстансу постоянный публичный IP, поэтому на этом этапе мы отключаем автоназначение публичного IP, и нажимаем кнопку Next: Add Storage
2.1.3. Подключение хранилища
Указываем размер «жесткого диска». Для наших целей достаточно 16 гигабайт, и нажимаем кнопку Next: Add Tags
2.1.4. Настройка тегов
Если бы мы создавали несколько инстансов, то их можно было бы группировать по тегам, для облегчения администрирования. В данном случае эта фукнциональность излишняя, сразу нажимаем кнопку Next: Configure Security Gorup
2.1.5. Открытие портов
На этом этапе мы настраиваем брандмауэр, открывая нужные порты. Набор открытых портов называется «Группа безопасности» (Security Group). Мы должны создать новую группу безопасности, дать ей имя, описание, добавить порт UDP (Custom UDP Rule), в поле Rort Range необходимо назначить номер порта, из диапазона динамических портов 49152—65535. В данном случае я выбрал номер порта 54321.
После заполнения необходимых данных, нажимаем на кнопку Review and Launch
2.1.6. Обзор всех настроек инстанса
На данной странице идет обзор всех настроек нашего инстанса, проверяем все ли настройки в порядке, и нажимаем кнопку Launch
2.1.7. Создание ключей доступа
Дальше выходит диалоговое окно, предлагающее либо создать, либо добавить существующий SSH ключ, с помощью которого мы в дальнейшем будет удаленно подключатся к нашему инстансу. Мы выбираем опцию «Create a new key pair» чтобы создать новый ключ. Задаем его имя, и нажимаем кнопку Download Key Pair, чтобы скачать созданные ключи. Сохраните их в надежное место на диске локального компьютера. После того как скачали — нажимаете кнопку Launch Instances
2.1.7.1. Сохранение ключей доступа
Здесь показан, этап сохранения созданных ключей из предыдущего шага. После того, как мы нажали кнопку Download Key Pair, ключ сохраняется в виде файла сертификата с расширением *.pem. В данном случае я дал ему имя wireguard-awskey.pem
2.1.8. Обзор результатов создания инстанса
Далее мы видим сообщение об успешном запуске только что созданного нами инстанса. Мы можем перейти к списку наших инстансов нажав на кнопку View instances
2.2. Создание внешнего IP адреса
2.2.1. Запуск создания внешнего IP
Дальше нам необходимо создать постоянный внешний IP адрес, через который мы и будем подключатся к нашему VPN серверу. Для этого в навигационной панели в левой части экрана необходимо выбрать пункт Elastic IPs из категории NETWORK & SECTURITY и нажать кнопку Allocate new address
2.2.2. Настройка создания внешнего IP
На следующем шаге нам необходима чтобы была включена опция Amazon pool (включена по умолчанию), и нажимаем на кнопку Allocate
2.2.3. Обзор результатов создания внешнего IP адреса
На следующем экране отобразится полученный нами внешний IP адрес. Рекомендуется его запомнить, а лучше даже записать. он нам еще не раз пригодиться в процессе дальнейшей настройки и использования VPN сервера. В данном руководстве в качестве примера я использую IP адрес 4.3.2.1. Как записали адрес, нажимаем на кнопку Close
2.2.4. Список внешних IP адресов
Далее нам открывается список наших постоянных публичных IP адресов (elastics IP).
2.2.5. Назначение внешнего IP инстансу
В этом списке мы выбираем полученный нами IP адрес, и нажимаем правую кнопку мыши, чтобы вызвать выпадающее меню. В нем выбираем пункт Associate address, чтобы назначить его ранее созданному нами инстансу.
2.2.6. Настройка назначения внешнего IP
На следующем шаге выбираем из выпадающего списка наш инстанс, и нажимаем кнопку Associate
2.2.7. Обзор результатов назначения внешнего IP
После этого, мы можем увидеть, к нашему постоянному публичному IP адресу привязан наш инстанс и его приватный IP адрес.
Теперь мы можем подключиться к нашему вновь созданному инстансу из вне, со своего компьютера по SSH.
3. Подключение к инстансу AWS
SSH — это безопасный протокол удаленного управления компьютерными устройствами.
3.1. Подключение по SSH c компьютера на Windows
Для подключения к компьютера с Windows, прежде необходимо скачать и установить программу Putty.
3.1.1. Импорт приватного ключа для Putty
3.1.1.1. После установки Putty, необходимо запустить утилиту PuTTYgen идущую с ней в комплекте, для импорта ключа сертификата в формате PEM, в формат, пригодный для использования в программе Putty. Для этого в верхнем меню выбираем пункт Conversions->Import Key
3.1.1.2. Выбор ключа AWS в формате PEM
Далее, выбираем ключ, который мы ранее сохранили на этапе 2.1.7.1, в нашем случае его имя wireguard-awskey.pem
3.1.1.3. Задание параметров импорта ключа
На этом шаге нам необходимо указать комментарий для этого ключа (описание) и задать для безопасности пароль и его подтверждение. Он будет запрашиваться при каждом подключении. Таким образом мы защищаем ключ паролем от не целевого использования. Пароль можно не задавать, но это менее безопасно, в случае, если ключ попадет в чужие руки. После нажимаем кнопку Save private key
3.1.1.4. Сохранение импортированного ключа
3.1.2. Создание и настройка соединения в Putty
3.1.2.1. Создание соединения
Открываем программу Putty, выбираем категорию Session (она открыта по умолчанию) и в поле Host Name вводим публичный IP адрес нашего сервера, который мы получили на шаге 2.2.3. В поле Saved Session вводим произвольное название нашего соединения (в моем случае wireguard-aws-london), и далее нажимаем кнопку Save чтобы сохранить сделанные нами изменения.
3.1.2.2. Настройка автологина пользователя
Дальше в категории Connection, выбираем подкатегорию Data и в поле Auto-login username водим имя пользователя ubuntu — это стандартный пользователь инстанса на AWS с Ubuntu.
3.1.2.3. Выбор приватного ключа для соединения по SSH
Затем переходим в подкатегорию Connection/SSH/Auth и рядом с полем Private key file for authentication нажимаем на кнопку Browse. для выбора файла с сертификатом ключа.
3.1.2.4. Открытие импортированного ключа
Указываем ключ, импортированный нами ранее на этапе 3.1.1.4, в нашем случае это файл wireguard-awskey.ppk, и нажимаем кнопку Открыть.
3.1.2.5. Сохранение настроек и запуск подключения
Вернувшись на страницу категории Session нажимаем еще раз кнопку Save, для сохранения сделанных ранее нами изменений на предыдущих шагах (3.1.2.2 — 3.1.2.4). И затем нажимаем кнопку Open чтобы открыть созданное и настроенное нами удаленное подключение по SSH.
3.1.2.7. Настройка доверия между хостами
На следующем шаге, при первой попытке подключиться, нам выдается предупреждение, у нас не настроено доверие между двумя компьютерами, и спрашивает, доверять ли удаленному компьютеру. Мы нажимем кнопку Да, тем самым добавляя его в список доверенных хостов.
3.1.2.8. Ввод пароля для доступа к ключу
После этого открывается окно терминала, где запрашивается пароль к ключу, если вы его устанавливали ранее на шаге 3.1.1.3. При вводе пароля никаких действий на экране не происходит. Если ошиблись, можете использовать клавишу Backspace.
3.1.2.9. Приветственное сообщение об успешном подключении
После успешного ввода пароля, нам отображается в терминале текст приветствия, который сообщает что удаленная система готова к выполнению наших команд.
4. Конфигурирование сервера Wireguard
Наиболее актуальную инструкцию по установке и использованию Wireguard с помощью описанных ниже скриптов можно посмотреть в репозитории: https://github.com/pprometey/wireguard_aws
4.1. Установка Wireguard
В терминале вводим следующие команды (можно копировать в буфер обмена, и вставлять в терминале нажатием правой клавиши мыши):
4.1.1. Клонирование репозитория
Клонируем репозиторий со скриптами установки Wireguard
4.1.2. Переход в каталог со скриптами
Переходим в каталог с клонированным репозиторем
4.1.3 Запуск скрипта инициализации
Запускаем от имени администратора (root пользователя) скрипт установки Wireguard
В процессе установки будут запрошены определенные данные, необходимые для настройки Wireguard
4.1.3.1. Ввод точки подключения
4.1.3.2. Ввод внутреннего IP адреса
Введите IP адрес сервера Wireguard в защищенной VPN подсети, если не знаете что это такое, просто нажмите клавишу Enter для установки значения по умолчанию ( 10.50.0.1 )
Пример вывода:
4.1.3.3. Указание сервера DNS
Введите IP адрес DNS сервера, или просто нажмите клавишу Enter для установки значения по умолчанию 1.1.1.1 (Cloudflare public DNS)
Пример вывода:
4.1.3.4. Указание WAN интерфейса
Дальше требуется ввести имя внешнего сетевого интерфейса, который будет прослушивать внутренний сетевой интерфейс VPN. Просто нажмите Enter, чтобы установить значение по умолчанию для AWS ( eth0 )
Пример вывода:
4.1.3.5. Указание имени клиента
Введите имя VPN пользователя. Дело в том, что VPN сервер Wireguard не сможет запуститься, пока не добавлен хотя бы один клиент. В данном случае я ввел имя Alex@mobile
Пример вывода:
После этого на экране должен отобразится QR код с конфигурацией только что добавленного клиента, который надо считать с помощью мобильного клиента Wireguard на Android либо iOS, для его настройки. А также ниже QR кода отобразится текст конфигурационного файла в случае ручной конфигурации клиентов. Как это сделать будет сказано ниже.
4.2. Добавление нового VPN пользователя
Чтобы добавить нового пользователя, необходимо в терминале выполнить скрипт add-client.sh
Скрипт запрашивает имя пользователя:
Пример вывода:
Также, имя пользователям можно передать в качестве параметра скрипта (в данном случае Alex@mobile ):
4.2.1. Файл пользовательской конфигурации
Описание файла конфигурации клиента:
4.2.2. QR код конфигурации клиента
5. Конфигурирование VPN клиентов
5.1. Настройка мобильного клиента Андроид
Официальный клиент Wireguard для Андроид можно установить из официального магазина GooglePlay
После чего, необходимо импортировать конфигурацию, считав QR код с конфигурацией клиента (см. пункт 4.2.2) и дать ему имя:
После успешного импорта конфигурации, можно включить VPN тоннель. Об успешном подключении скажет заначок ключика в системной панели Андроид
5.2. Настройка клиента Windows
Первоначально необходимо скачать и установить программу TunSafe for Windows — это клиент Wireguard для Windows.
5.2.1. Создание файла конфигурации для импорта
Правой кнопкой мышки создаем текстовый файл на рабочем столе.
5.2.2. Копирование содержимого файла конфигурации с сервера
Дальше возвращаемся к терминалу Putty и отображаем содержимое конфигурационного файла нужного пользователя, как это описано на шаге 4.2.1.
Далее выделяем правой кнопкой мыши текст конфигурации в терминале Putty, по окончании выделения он автоматически скопируется в буфер обмена.
5.2.3. Копирование конфигурации в локальный файл конфигурации
Поле этого возвращаемся к созданному нами ранее на рабочем столе текстовому файлу, и вставляем в него из буфера обмена текст конфигурации.
5.2.4. Сохранение локального файла конфигурации
Сохраняем файл, с расширением .conf (в данном случае с именем london.conf )
5.2.5. Импорт локального файла конфигурации
Далее необходимо импортировать файл конфигурации в программу TunSafe.
5.2.6. Установка VPN соединения
Выбрать этот файл конфигурации и подключиться, нажав кнопку Connect.
6. Проверка успешности подключения
Чтобы проверить успешность подключения через VPN тоннель, необходимо открыть браузер и перейти на сайт https://2ip.ua/ru/
Отображаемый IP адрес должен совпадать с тем, который мы получили на этапе 2.2.3.
Если это так, значит VPN тоннель работает успешно.
Из терминала в Linux можно проверить свой IP адрес, введя команду:
Или можно просто зайти на порнохаб, если вы находитесь в Казахстане.
Как настроить WireGuard, ваш собственный VPN нового века
Напоминаем, что все действия, описанные в статье, пользователь делает на свой страх и риск. Материал приведен исключительно в ознакомительных целях. Если же вы собираетесь воспроизводить действия, описанные ниже, настоятельно советуем внимательно прочитать статью до конца хотя бы один раз. Редакция 3DNews не несет никакой ответственности за любые возможные последствия.
⇡#Что такое WireGuard и зачем он нужен?
WireGuard — это современный протокол для организации VPN, написанный с нуля, бесплатный и с открытыми исходниками. В отличие от «мастодонтов» вроде OpenVPN или IPSec, он намного проще и легче. Это касается и скорости (пере)подключения, и производительности, и требований к ресурсам, и процесса настройки, и объёма кода. Недавно было объявлено, что WireGuard войдёт в состав будущих ядер Linux, а впоследствии попадёт и во все популярные дистрибутивы, что косвенно указывает на зрелость этого решения.
Как и было заявлено в анонсе, мы рассматриваем сценарий защиты подключения к публичным и другим недоверенным сетям. Естественно, этим использование WireGuard не ограничивается. В качестве примера рассмотрим настройку клиентов и сервера (правда, в данном случае это условные понятия — в силу специфики протокола), работающего в облаке и на домашнем роутере Keenetic. Как показывает практика, многие публичные VPN-сервисы не отличаются щепетильностью в отношении данных клиентов, поэтому всегда лучше иметь что-то своё, подконтрольное только пользователю. В нашем случае мы рассматриваем установку и настройку WireGuard, используя для этого компьютер на Windows и облачную виртуальную машину на Ubuntu.
Нам понадобится полный набор PuTTY, так что лучше скачать сразу MSI-пакет с инсталлятором (доступен по предыдущей ссылке), который всё установит и создаст новую группу в главном меню. Там нам нужна утилита PuTTYgen. После запуска генерируем новую пару ключей с настройками по умолчанию (RSA-2048), нажав кнопку Generate и поводив с полминуты мышкой в окне утилиты. Осталось заполнить несколько полей: в Key comment можно ввести название ключа в качестве напоминания, а в Key passphrase и Confirm passphrase ввести один и тот же пароль.
⇡#Настройка сервера Vscale
Vscale — российский облачный провайдер, имеющий собственные площадки в Москве и Санкт-Петербурге и предлагающий неплохие конфигурации по низким ценам. Самый дешёвый сервер, мощностей которого вполне достаточно для наших задач, обойдётся в 200 руб./месяц. Хранение снапшота стоит ещё 40 руб./месяц. И его тоже можно перенести из одного региона в другой. Зато никаких ограничений по трафику нет.
Специально для читателей 3DNews Vscale подготовила промокод 3DNEWS500, чтобы можно было ознакомиться со всеми возможностями сервиса. После регистрации надо пополнить баланс хотя бы на 100 рублей или привязать банковскую карту. Затем промокод надо активировать на этой странице. Код будет действовать до 23:59:59 18.02.2020.
Интерфейс сервиса доступен на русском языке. Разобраться в нём просто, так что коротко опишем основные этапы. Для работы первым делом нужно в настройках аккаунта добавить публичный SSH-ключ, полученный в PuTTYgen. Затем в разделе серверов создать новый сервер с ОС Ubuntu 18.04, указав нужный регион, тариф и ключ. В течение минуты сервер будет готов и запущен.
Отдельного SSH-клиента для доступа к командной строке не требуется, так как Vscale предоставляет веб-консоль. Для входа вводим логин root и нажимаем Enter, далее по одной вводим нижеприведённые команды и на всё соглашаемся, нажимая Enter:
Пара замечаний на случай использования других облачных провайдеров. Во-первых, для Ubuntu 19.10 и более свежих версий ОС добавлять ppa не надо, достаточно будет первых двух команд. Во-вторых, доступ к командной строке возможен с помощью PuTTY. В поле Host Name надо ввести IP-адрес сервера, а в разделе Connection → SSH → Auth — путь до приватного ppk-ключа. Логин root, а пароль тот, что был указан при создании ключа (Key passphrase). Для удобства можно сохранить сессию (Save). По нажатии кнопки Open откроется окно консоли, при первом запуске предваряемое уведомлением о безопасности, с которым надо согласиться.
Обратите внимание, что даже за выключенным сервером сохраняются ресурсы, которые точно так же оплачиваются. Поэтому ненужный сервер надо удалять. Если VPN необходим не на постоянной основе, а лишь иногда, то можно сохранить все настройки, создав снапшот (бэкап). Сам снапшот можно перенести в другой регион и при создании нового сервера выбрать именно его в качестве основы. Создавать снапшот надо строго после завершения настройки VPN-сервера и весьма желательной в этом случае установки DDNS-клиента, выключив сервер непосредственно перед созданием бэкапа.
⇡#Настройка VPN-сервера WireGuard
Для настройки сервера WireGuard не будем мудрствовать лукаво, а воспользуемся открытым решением easy-wg-quick. Данный скрипт автоматически формирует файлы конфигурации и позволяет легко манипулировать настройками. Предварительно надо установить сам wireguard и некоторые дополнительные утилиты. В веб-консоли Vscale или в PuTTY вводим следующие команды, нажимая Enter после каждой:
При первом запуске скрипт по умолчанию создаст конфигурационный файл для сервера и для одного клиента, а также выведет QR-код, который можно отсканировать в мобильном приложении WireGuard, чтобы тут же получить все необходимые настройки.
Чтобы добавить настройки ещё для одного клиента (ноутбука, например), надо ещё раз выполнить эту же команду, указав имя нового профиля:
Например, для имени профиля win10 будет создан соответствующий файл wgclient_win10.conf. Его содержимое можно просмотреть командой cat, что пригодится при настройке клиента WireGuard в будущем.
После добавления всех нужных профилей осталось лишь добавить сервер WireGuard в автозапуск и включить его:
Для просмотра текущих подключений используйте эту команду:
⇡#Настройка VPN-клиента WireGuard
Клиенты для Windows, Android, iOS и других ОС можно скачать на сайте WireGuard. С мобильными версиями всё просто — достаточно отсканировать QR-код. Или же, как и для всех остальных клиентов, вручную скопировать настройки из файлов wgclient_*.conf. Из дополнительных опций там есть только возможность исключить доступ через VPN для выбранных пользователем приложений: Excluded Applications в настройках профиля.
В случае Windows-клиента в меню левой нижней кнопки надо выбрать Add empty tunnel, вставить в новом окне всё содержимое conf-файла, указать имя профиля (Name). Опционально можно включить функцию kill-switch для блокировки любого трафика вне VPN-подключения. Наконец, надо сохранить (Save) и активировать (Activate) соединение. Для проверки корректности подключения проще всего зайти на какой-нибудь сайт, определяющий текущий внешний IP-адрес.
В актуальных моделях роутеров Keenetic с прошивкой версии 3.3 или старше также появилась поддержка VPN-подключений WireGuard — нужно установить одноимённый компонент. Чтобы импортировать настройки соединения, нужно сохранить содержимое файла wgclient_*.conf (см. выше) в текстовый документ, а затем в разделе «Другие подключения» загрузить параметры из этого файла. Роутер создаст на их основе новое подключение, которое нужно активировать переключателем в левой части списка.
Для корректной работы надо сделать несколько небольших изменений (кстати, после каждого действия не забывайте нажимать кнопку «Сохранить» в нижней части веб-интерфейса). Во-первых, включить галочку «Использовать для входа в Интернет». Во-вторых, поле «Разрешенные подсети» привести к виду 0.0.0.0/0. В-третьих, в разделе «Приоритеты подключений» перетащить свежесозданное подключение выше всех остальных.
После этого все клиенты, подключённые к роутеру, по умолчанию будут выходить в Интернет через VPN-туннель. Если же необходим доступ только для некоторых устройств, то лучше завести отдельный профиль.
Обратите внимание, что для каждого клиента нужно будет сгенерировать и скопировать собственный conf-файл. Если на предыдущем этапе вы настроили DDNS-клиент на сервере, то в разделе Endpoint у всех клиентов надо будет прописать DDNS-имя вместо IP-адреса.
⇡#Настройка WireGuard для Keenetic: сервер и мобильный клиент
В самом начале мы уже упоминали, что принципиального различия между сервером и клиентом в случае WireGuard нет. И раз уже поддержка этого протокола доступна в прошивке, то можно настроить подключение клиентов к роутеру. В текущей версии не все настройки вынесены в веб-интерфейс, но ничего сложного всё равно нет. Единственное требование — наличие «белого» внешнего IP-адреса, пусть даже динамического (в этом случае поможет DDNS).
В разделе «Другие подключения» в секции WireGuard нужно добавить новое подключение. Указываем имя (любое) и ставим галочку «Генерация ключей» (Generate a random key pair). В поле «Адрес» надо ввести любой подходящий адрес из частного диапазона, но такой, чтобы он не пересекался с другими сетями на самом роутере. В качестве примера используем 10.11.12.1/24. Номер порта можно указать произвольный, лишь бы он не блокировался провайдером и не совпадал с уже открытыми портами для других сервисов. В нашем примере это 55555. Наконец, в поле DNS надо указать адрес любого публичного DNS-сервера.
Следующий этап — добавление пиров (клиентов) соответствующей кнопкой. Имя указываем любое, а в поле «Разрешённые подсети» вводим 0.0.0.0/0. Теперь открываем на смартфоне мобильное приложение WireGuard и добавляем новое подключение — Create from scratch. В разделе Interface указываем имя (любое) и жмём кнопку Generate. Содержимое поля Public Key копируем и вставляем в настройках пира на роутере в поле «Публичный ключ». В поле Addresses указываем частный IP-адрес из той же подсети, что и для роутера. В нашем примере у него был 10.11.12.1/24, так что для клиента возьмём просто следующий: 10.11.12.2/24. DNS опять же любой публичный.
В разделе Peers в поле Public keys копируем содержимое поля «Публичный ключ» роутера, в Allowed IPs вводим 0.0.0.0/0, а в Endpoint вводим внешний IP-адрес роутера (или DDNS-имя) и порт через двоеточие, то есть для нашего примера должна получиться конструкция вида xx.xx.xx.xx:55555. Опционально можно включить функцию поддержки активности подключения, указав время в секундах в поле Persistent keepalive на клиенте и в поле «Проверка активности» в параметрах пира на роутере. Обычно достаточно интервала от 3 до 30 секунд. Для остальных клиентов придётся повторить эту же процедуру добавления новых пиров.
Но это ещё не всё. После добавления пиров необходимо разрешить им доступ в локальную сеть и в Интернет. В разделе «Межсетевой экран» надо найти WireGuard-подключение — ориентируйтесь по имени, оно может быть в выпадающем меню сверху — и завести для него новое разрешающее правило (см. скриншот выше). Также надо будет подключиться к роутеру по telnet с помощью PuTTY и ввести несколько команд. Адрес по умолчанию my.keenetic.net, логин и пароль те же, что для доступа к веб-интерфейсу, команды приведены ниже:
Наконец, после всех этих действий надо активировать WireGuard-соединение. Если всё прошло успешно, то после подключения клиента напротив пира будет гореть зелёный кружочек и показываться статистика по трафику. Только учтите, что производительность роутера всё-таки намного меньше, чем у любого облачного сервера. Так что приличную скорость соединения он обеспечит ценой нагрузки на CPU маршрутизатора, что может повлиять на работу других сервисов.
Напоследок напомним «народную» мудрость: на VPN надейся, а сам не плошай. Проще говоря, надо всегда соблюдать осторожность и цифровую гигиену. К совсем уж подозрительным сетям и вовсе подключаться не надо, да и про базовые правила забывать не стоит. Их не так уж много: вовремя ставить обновления ОС и ПО, использовать двухфакторную аутентификацию, тщательно выбирать используемые программы, проверять разумность запросов ПО на доступ к различным ресурсам устройства, обзавестись современным антивирусом. Всё это касается и смартфонов, и планшетов, и ноутбуков, и десктопов.
Wireguard qr code generate
ljm42
October 12, 2019
Note: this community guide is offered in the hope that it is helpful, but comes with no warranty/guarantee/etc. Follow at your own risk. What can you do with WireGuard? Let’s walk t
kaiguy
October 12, 2019
Thanks for the quick writeup! I was scratching my head for a good 10 minutes until I realized I had to toggle Inactive to Active. Not sure why my mind read that as clicking inactive would inactivate i
Can0n
November 6, 2019
I found if you do someething strange in the set up and hit apply, you will lose access to the server. you will not be able to ping it or load the interface. to fix without rebooting after
WireGuard 4+
Official WireGuard VPN client
WireGuard Development Team
Screenshots
Description
WireGuard is a fast, modern, and secure VPN tunnel. This app allows users to manage and use WireGuard tunnels. The app can import new tunnels from archives and files, or you can create one from scratch. It is currently undergoing rapid development, and we are listening to our users in implementing new and exciting features. Please visit wireguard.com for a summary of the WireGuard protocol and how to set up your own WireGuard server for use with this app.
What’s New
Fixes for small bugs, and better on-demand handling.
Ratings and Reviews
A Perfect Implementation
This works more or less flawlessly. The protocol itself is incredibly fast and efficient, and this implementation maintains that.
It is completely integrated with macOS’s networking frameworks, so it can be managed in System Preferences like a normal VPN and run without keeping a separate application open. It seems to have almost no system overhead, either, and it is very easy to set up. It also properly stores credentials in Keychain Access, rather than trying to manage them itself.
There is one oddity, though: the configuration dialog consists of one text box that contains the config file, rather than a series of form fields like the iOS client. I don’t think it is worse, necessarily, but it’d make more sense if the UI was consistent across both platforms.
Great application
This is a fantastic bit of software. The initial setup can be someone of a bear and confusing but once you get the keys set up and single port forwarded its off to the races. Its amazingly fast compared to openvpn and more secure.
Some might be scared off by opening a port but dont be. If you run a port scan you cant even see the port is open. It only reports open when wireguard handshake is complete.
Pair it will a VPN provider and you have a fast and reliablie vpn setup. Highly recommend.
Amazing if you can get it to work
While the wireguard protocol does live up to its grand promises of being lightweight and fast, the abysmal lack of official documentation and especially troubleshooting suggestions makes it nearly impossible to fix your setup if it doesn’t work on the first try. Unless you’re skilled at networking or you have assistance from someone with a working installation, it’s next to impossible to troubleshoot a nonfunctional installation. That said, it fulfills all promises made about the protocol if you do manage to get it working.
App Privacy
Data Not Collected
The developer does not collect any data from this app.
Privacy practices may vary, for example, based on the features you use or your age. Learn More
Information
English, Catalan, Finnish, French, German, Indonesian, Italian, Japanese, Korean, Persian, Polish, Punjabi, Romanian, Russian, Simplified Chinese, Slovenian, Spanish, Traditional Chinese, Turkish
WireGuard 4+
Fast, modern, secure VPN
WireGuard Development Team
Screenshots
Description
WireGuard is a fast, modern, and secure VPN tunnel. This app allows users to manage and use WireGuard tunnels. The app can import new tunnels from archives and files, from QR codes, or you can create one from scratch. It is currently undergoing rapid development, and we are listening to our users in implementing new and exciting features. Please visit wireguard.com for a summary of the WireGuard protocol and how to set up your own WireGuard server for use with this app.
What’s New
Fix issues around iOS 15 upgrade.
Ratings and Reviews
great if you’re up to setting up your own backend
Wireguard is ideal for people who want to set up their own VPN infrastructure rather than trusting someone else’s. Much, much simpler than IPSec or OpenVPN, and very fast.
I like that the app can be configured to auto connect on WiFi, cellular, or both. And that you can whitelist or blacklist WiFi SSIDs.
However, since upgrading to iOS 13, I’ve found the VPN periodically stalls, preventing any traffic at all. I can get it going again by restarting the tunnel. Not sure if this is a bug in the app or in iOS 13, but it’s pretty frustrating. This wasn’t a problem in iOS 12.x.
Connection Problem
I’ve just downloaded Wireguard for iOS on my iPhone X. I found that it could not connect correctly. When I checked the log, I found «Failed to send handshake initiation», «no route to host» error messages.
When I further checked the problem, I found that there is no Wireless Setting option in the WireGuard settings page in the iOS settings. I understand that this setting will only appear in iOS devices with Cellular sold in China. Under normal circumstances, China region devices will pop up the user permission to use data when an app first runs or requests to access internet (You can select: off / WLAN Only / WLAN & Cellular Data), but WireGuard does not pop up this alert when it first runs, so the Wireless setting option does not appear in the iOS settings, it results in WireGuard can never use any network (WLAN and Cellular Data).
To solve this problem, I’m eagerly recommending that you add a «Import tunnel from url» option (or any option that can trigger internet access request from the app). It will not just function as a new method to import tunnel, but it will also trigger internet access request when used which will trigger the pop-up asking permission to access internet.
Please, please, please take this into your consideration! I’m looking forward to getting Wireguard connected on my iPhone and I believe many people have the same issue.
Thank you so much!
On-demand Not Working after iOS 15 update
This app was working great when I disconnected from my WiFi when I had prior versions of iOS; I had it set to automatically connect to the VPN and it did this seamlessly. After the iOS upgrade to iOS 15, this doesn’t automatically connect anymore and I have manually connect using the VPN button in my iPhone settings. I also have to manually disconnect from the VPN when I connect to my home WiFi. I don’t see any WiFi SSIDs show up on the list of WiFi network to exclude. I removed the app and reinstalled the latest version but this did not solve it. This is probably not the developers fault, but I hope they can fix it. It’s a fantastic app, otherwise.
App Privacy
Data Not Collected
The developer does not collect any data from this app.
Privacy practices may vary, for example, based on the features you use or your age. Learn More
Information
English, Catalan, Finnish, French, German, Indonesian, Italian, Japanese, Korean, Persian, Polish, Punjabi, Romanian, Russian, Simplified Chinese, Slovenian, Spanish, Traditional Chinese, Turkish
xei/wireguard-setup-scripts
Use Git or checkout with SVN using the web URL.
Work fast with our official CLI. Learn more.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
Setup WireGuard VPN and Pi-hole ad blocker like a piece of cake 🍰
Here you can find some useful shell scripts in order to setup WireGuard VPN server and Pi-hole network-wide ad blocker on a Linux server as easily as possible.
A VPN (Virtual private network) extends your private network (e.g. the LAN in your office) across a public network (usually the Internet) so that the remote or mobile users and branch offices can connect to the private network remotely through the Internet in a secure way and access to corporate applications and private resources such as IP cameras, fax machines, private servers, etc.
The major applications of VPNs are:
Among these all, WireGuard seems to be the most interesting. It is lite (about 4,000 lines of code), fast and secure. So in 2020, WireGuard was officially added to the Linux kernel 5.6 release (so also Android kernels) by Linus Torvalds.
Pi-hole is a Linux network-level advertisement and Internet tracker blocking application which acts as a DNS sinkhole, intended for use on a private network.
The application acts as a DNS server for a private network (replacing any pre-existing DNS server provided by another device or the ISP), with the ability to block advertisements and tracking domains for users’ devices without installing any client-side software.
Because Pi-hole blocks domains at the network level, it is able to block advertisements, such as banner advertisements on a webpage, but it can also block advertisements in unconventional locations, such as on Android, iOS and smart TVs.
Using VPN services, Pi-Hole can block domains without using a DNS filter setup in a router. Any device that supports VPN can use Pi-Hole on a cellular network or a home network without a DNS server configured.
Setup the server
Here you can follow the instructions step by step to setup a VPN/AdBlocker server using WireGuard and Pi-hole.
Buy a linux server
WireGuard and Pi-hole are really lite softwares so that you can run them on a lite Linux instance with 1 vCore and 1GB of RAM without any problem.
The scripts are tested on Ubuntu 20.04 but you can run them on Debian, Fedora, CentOS and Arch Linux.
You can buy a cheap Linux IaaS from these cloud providers for the VPN server:
| Cloud Provider | Location | Price (starting at) | Traffic |
|---|---|---|---|
| Vultr | Worldwide (USA is recommended because of sanctions!) | $3.50/month | — |
| Digital Ocean | Worldwide (USA is recommended because of sanctions!) | $5/month | — |
| Hetzner | Germany (Finland did not work as VPN server for me!) | €3/month | 20 TB |
Clone the repository
Run the following commands to download the scripts:
Setup WireGuard server
Run the following command to setup the WireGuard server:
You have to answer some questions in order to configure the server. However you can leave the default values.
When you see the message WireGuard is setup successfully. you can go on.
Setup Pi-hole DNS sinkhole
Run the following command to start Pi-hole installer:
For more information about installer wizard vistit the official documentation.
Create a new peer (client)
Run the following command to create a new client (here named xei-pc ):
This command will generate a QR code that can be scanned by Wireguard client mobile application. It also generate a config file in /etc/wireguard/peers/xei-mobile/ directory that can be used instead of the QR code.
You have to modify the client’s config file and change DNS section to something like 1.1.1.1 or 8.8.8.8 if you are not going to setup Pi-hole or other DNS servers.
Revoke a peer (client)
You can remove a client by running the following command:
xei-mobile is the name of the client you want to remove.
Remove WireGuard server
You can remove the WireGuard server completely by running the following command:
Note that the above script will remove the directory /etc/wireguard and its contents including all peers’ config files. Backup the direcory if it is necessary.
Note that the above script will not remove Pi-hole. In order to remove Pi-hole visit its official documentation.
WireGuard client applications
When you create a new peer (client) with the above command, a config file will be generated in /etc/wireguard/peers/client-name/ directory that should be imported to WireGuard client application.
WireGuard client application is available in almost all platforms:
This repository is heavily inspired by a great similar repository by angristan.
Give a ⭐ if this project helped you!
About
A set of shell scripts for setting up WireGuard VPN and Pi-hole ad blocker on a Linux server.
VPN на Wireguard для полных новичков
Это подробная инструкция по настройке личного VPN на протоколе Wireguard, чтобы обходить блокировки Роскомнадзора и защищаться от хакеров в чужих Wi-Fi с компьютеров и телефонов. По шагам, с картинками, для самых маленьких.
Если вы в России, у вас наверняка не работает LinkedIn или тормозит Twitter, а в месте с ним и половина интернета. VPN поможет нивелировать вредительство провайдеров и государственных органов. Кроме того, в общедоступных Wi-Fi точках, к которым вы подключаетесь в кафе, могут сидеть мамкины хакеры, которые перехватывают трафик и могут украсть у вас данные или подсунуть вирус. Достаточно включить VPN, и ваш трафик станет для таких вредителей недоступен.
Содержать VPN-сервер стоит денег, потому что где-то должен работать компьютер с серверной программой, и кто-то должен платить за электричетсво и работу инженеров. Если не платите вы, значит платит кто-то другой. В замен этот другой получает что-то ценное, например ваши персональные данные, которые затем можно использовать для мошенничества или шантажа. Не пользуйтесь бесплатными VPN-сервисами.
Конечно, у платных VPN есть свои плюсы, например быстрое переключение между локациями (чтобы сменить сервер с Германии на США, например), особо продвинутые средства обхода блокировок и тому подобное. К счастью, в России блокировки осуществляются довольно просто, и для их обхода такие сервисы избыточны.
Вам понадобится VPS — самый дешёвый хостинг в стране, где блокировок нет. Мои рекомендации:
Или любой другой сервер на Ubuntu за пределами России, к которому у вас есть root-доступ.
За каждого нового клиента на VPS по ссылкам, которые я указал вначале, мне перепадает несколько долларов. Этого как раз хватает на оплату хостинга для этого блога. Если вы зарегаетесь через мои ссылки — мне будет приятно.
Шаг 1 — Запустите VPS
Нужен самый простой сервер на Ubuntu 20.04 или новее.
Шаг 2 — Подключитесь к VPS
Шаг 3 — Установите Wireguard
Мы воспользуемся готовым скриптом от доброго человека.
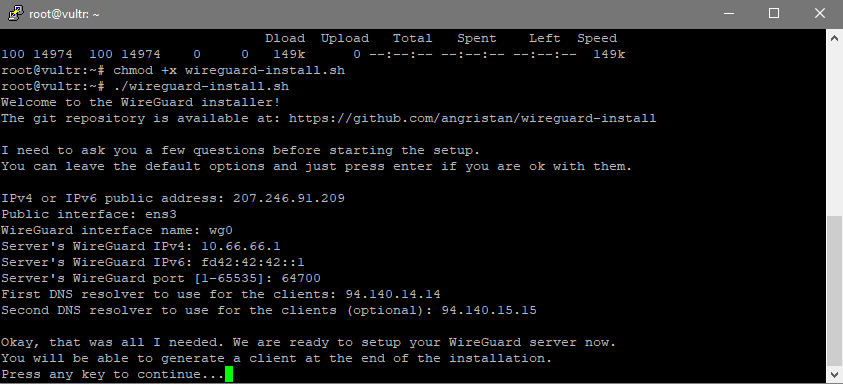
Шаг 4 — Создайте учётные записи
Сразу после установки WireGuard в консоли начнётся процесс создания учётной записи.
Кроме того, нужно сохранить текстовые данные к этой учётной записи для подключения с компьютера. Для этого откроем файл конфигурации:
Шаг 4.1 — Ещё одна учётная запись
Лучше давать каждому пользователю по учётной записи, чтобы при необходимости можно было точечно её отключить.
Чтобы добавить ещё одного пользователя, снова введите команду
./wireguard-install.sh
Скрипт спросит, что именно сделать. Введите единицу (Add a new user), нажмите Enter и вы снова увидите процесс создания нового пользователя.
Шаг 5 — Подключение к VPN
Windows / Mac
Android / iOS
Послесловие
От чего не защитит VPN
Именно по этой причине нужно делать отдельные учётные записи WireGuard для каждого пользователя, и никогда не выкладывать эти учётки в открытый доступ, иначе вам возможно придётся отвечать за действия какого-то анонима из интернета.
И, разумеется, VPN не сделает вас анонимным, если вы заходите в социальные сети под учёткой с вашим настоящим именем.
Wireguard qr code generate
You’ll first want to make sure you have a decent grasp of the conceptual overview, and then install WireGuard. After that, read onwards here.
Side by Side Video
Before explaining the actual comands in detail, it may be extremely instructive to first watch them being used by two peers being configured side by side:
Or individually, a single configuration looks like:
Command-line Interface
An IP address and peer can be assigned with ifconfig(8) or ip-address(8)
Or, if there are only two peers total, something like this might be more desirable:
The interface can be configured with keys and peer endpoints with the included wg(8) utility:
Finally, the interface can then be activated with ifconfig(8) or ip-link(8) :
There are also the wg show and wg showconf commands, for viewing the current configuration. Calling wg with no arguments defaults to calling wg show on all WireGuard interfaces.
Much of the routine bring-up and tear-down dance of wg(8) and ip(8) can be automated by the included wg-quick(8) tool:
Key Generation
WireGuard requires base64-encoded public and private keys. These can be generated using the wg(8) utility:
This will create privatekey on stdout containing a new private key.
You can then derive your public key from your private key:
This will read privatekey from stdin and write the corresponding public key to publickey on stdout.
Of course, you can do this all at once:
NAT and Firewall Traversal Persistence
By default, WireGuard tries to be as silent as possible when not being used; it is not a chatty protocol. For the most part, it only transmits data when a peer wishes to send packets. When it’s not being asked to send packets, it stops sending packets until it is asked again. In the majority of configurations, this works well. However, when a peer is behind NAT or a firewall, it might wish to be able to receive incoming packets even when it is not sending any packets. Because NAT and stateful firewalls keep track of «connections», if a peer behind NAT or a firewall wishes to receive incoming packets, he must keep the NAT/firewall mapping valid, by periodically sending keepalive packets. This is called persistent keepalives. When this option is enabled, a keepalive packet is sent to the server endpoint once every interval seconds. A sensible interval that works with a wide variety of firewalls is 25 seconds. Setting it to 0 turns the feature off, which is the default, since most users will not need this, and it makes WireGuard slightly more chatty. This feature may be specified by adding the PersistentKeepalive = field to a peer in the configuration file, or setting persistent-keepalive at the command line. If you don’t need this feature, don’t enable it. But if you’re behind NAT or a firewall and you want to receive incoming connections long after network traffic has gone silent, this option will keep the «connection» open in the eyes of NAT.
Demo Server
If you’d like to redirect your internet traffic, you can run it like this:
By connecting to this server, you acknowledge that you will not use it for any abusive or illegal purposes and that your traffic may be monitored.
Debug Info
If you’re using the Linux kernel module and your kernel supports dynamic debugging, you can get useful runtime output by enabling dynamic debug for the module:
© Copyright 2015-2022 Jason A. Donenfeld. All Rights Reserved. «WireGuard» and the «WireGuard» logo are registered trademarks of Jason A. Donenfeld.
This project is from ZX2C4 and from Edge Security, a firm devoted to information security research expertise.
Easily Extend a LAN to an Android Phone using Wireguard
VPN done right
VPN technologies like IPsec and OpenVPN have been around for a very long time. While they have proven to serve their purpose of securely establishing a tunnel between two networks, I have always found them very cumbersome to setup and run. OpenVPN connections have always been brittle, caused routing issues for me and have poor performance, both in terms of bandwidth and battery life (for mobile clients).
Recently a new, modern, VPN technology was developed with a focus on the following attributes:
A big reason why I personally like Wireguard’s approach, is because it really adheres to the Unix philosophy: it does one thing and does it well. Wireguard leaves related concerns, like user management, to other tools. The authors have also taken a very good look at the UX of other workhorse tools that get out of a user’s way, like OpenSSH and Mosh.
Wireguard was initially made available as a linux kernel module, but there is now a userspace golang implementation which brings it to a variety of other platforms, including the Mac, iOS and Android. This makes it the ideal technology to securely make some of my home automation services, which I can’t run on a cloud provider, accessible when I’m away from the local network.
Wireguard Basics
Wireguard does not really have the concept of a client and a server. Both endpoints of a tunnel are peers. Depending on how they are configured, a peer can act as a traditional server, client or something in between.
Wireguard uses a concept called Cryptokey Routing. Each Wireguard network interface has a private key and a list of peers. The peer is defined by its public and a range of IP addresses that should be routed through the tunnel. This setup is very similar to how OpenSSH works. By manipulating the ranges of allowed IPs a on peer, you can use Wireguard to peer 2 distinct network segments together, route all traffic through a remote server or add a single device into the network.
Wireguard on Ubuntu
The first thing we need to do on Ubuntu is install the kernel module and Wireguard tools:
Temporary Configuration Using Wireguard Tools
The simplest way to create a Wireguard tunnel is to use the wireguard tools that are installed alongside the kernel module. This allows you to experiment with the technology, but the network interface will not persist across a reboot of the machine.
All the command snippets are assuming that they are being executed as root.
The first step is to create a network interface that uses the wireguard driver
Next we set an IP address to our interface
The IP you chose will depend on what you want to achieve. If you just want to add the peer to the local network you should make this an IP from your current subnet that is not administered by dhcp. I have chosen to have my VPN clients arrive in a different subnet, so I can put some additional firewall protections in place.
We also need to create and set a private key to our interface. This can be done by writing it to a file first
The public key, needed to add this interface as a peer to another interface, can be generated from a private key using
The public key from an interface can be retrieved with the following command
Finally we should add at least one peer to the interface (this can also be done when the interface is already in the up state)
In this scenario we’re adding a peer with a single IP of which we don’t know the public endpoint. This means that only the peer can start the tunnel.
The interace is now ready to be used
All of this setup, except for the creation of the interface, can also be added to a configuration file. The above configuration would look like the following wireguard.conf :
You can then set this configuration on the interface by running a single command:
If you configured the interface by hand using the tools, you can ask wireguard to create the corresponding conf file for you:
Persistent Configuration Using /etc/network/interfaces
Once you’ve created these files, you can reload the server networking configuration with:
Wireguard Android Client
Now that we have a peer configured on ubuntu server, it’s time to configure the mobile client. The first thing is to get the Android app, which is currently in preview, either on the Play Store or FDroid. In case you run a custom rom that has the Wireguard module, the application will use it, otherwise it’ll default to the userland golang implementation. This is all transparent to the user.
The Android app is configured like any other Wireguard client. You can either add all the parameters by hand into UI, or you can create the config somewhere else and get it on the phone by scanning a QR code. Given that entering a random public key with an autocorrecting keyboard is probably not anybody’s idea of fun, we’ll be taking the latter option.
Wireguard config
Let’s dive straight in, and look at the config. We’ll explain the different parameters below:
Create a QR code
Since a QR code is just another way to render a random string, we can turn the config into one and scan it on the phone, so we don’t have to manually enter the entire configuration.
In order to do this we’re going to use the qrencode program on linux.
This will render a QR code in your terminal, which you can scan with the Android app.
Conclusions
We’ve covered extending a private LAN to a mobile device using Wireguard by configuring it on a Ubuntu server and using the Wireguard app on a mobile device. This really just scratches the surface of what is possible with Wireguard. It’s high performance, support for multiple platforms and the fact that it can be used inside a container allow for much more jessfraz type experiments. I really do hope more projects take a page out of Wireguard’s book, because this is how security related projects should work.
warner/wireguard-vanity-address
Use Git or checkout with SVN using the web URL.
Work fast with our official CLI. Learn more.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
Generate Wireguard keypairs with a given prefix string.

The Wireguard VPN uses Curve25519 keypairs, and displays the Base64-encoded public key in status displays. I found it hard to remember which key goes with which target, and the config file doesn’t really support comments or attaching human-memorable names to those keys.
So this tool lets you generate a few million keypairs and print out just the ones with a given string in the first few (10) letters, using a case-insensitive search to increase your chances.
The tool will run for a long time, printing out more and more candidates as it goes, so just interrupt the process with Control-C or SIGINT when you’ve seen something that you like. There is no saved state or config file, and the generation process is entirely memoryless, so you don’t lose any progress by interrupting it.
Once you’ve found a key that you like, copy the private half (on the left) into your wg0.conf config file as the [Interface] PrivateKey= field, and use the public half (on the right) on the other side of that VPN connection in a [Peer] PublicKey= entry.
On my 2017 laptop (quad-core 2.8GHz), this tool checks about 60 thousand keys per second per core. It uses rayon to parallelize across all available cores, achieving 240k keys per second.
Only a tiny fraction of those trial keys will match the search string. Each character of the target string reduces this fraction by a factor of about 32 (case-folded base64 encoding). By allowing the match to start anywhere in the first ten letters, we increase the hit rate by about 10x.
A four-character string like dave means only one out of every (roughly) 150k keys will match, while a five-character string like carol reduces that to one out of 5.6 million. Longer strings will yield fewer candidate keypairs for a given amount of runtime.
You can run this on multiple machines, but of course you then risk revealing your private VPN key to any of those machines. There is no support for managing clusters or anything like that: just install the tool on each worker machine and run it with the same argument.
Since Wireguard VPN keys are not really public identifiers (you wouldn’t publish them on a web page as you might with Tor’s «Onion Addresses», or Bitcoin addresses), my advice is to stick with a four or five character search string, and don’t try too hard to find a perfect pubkey. You only need something distinctive enough distinguish between a handful of VPN targets in a status display.
This is distributed under the MIT license, see LICENSE for details.
Setting up a WireGuard VPN on the Raspberry Pi
In this project, we will show you how to set up a WireGuard VPN on the Raspberry Pi.
WireGuard is a new VPN protocol that has recently been gaining a lot of popularity.
There are a couple of advantages to using the WireGuard VPN on your Raspberry Pi over OpenVPN.
WireGuard is much faster at making connections than OpenVPN, it can complete a connection within a tenth of a second.
The codebase for WireGuard is also drastically smaller then OpenVPN’s. This allows the software to be more secure thanks to the smaller attack surface and bugs being able to be dealt with easier.
For comparison sake, WireGuard only uses 4,000 lines of code compared to the 70,000+ lines of code that OpenVPN uses.
The only notable disadvantage of WireGuard is that it does store the connecting user’s IP addresses. It does this to improve the connection speed.
By the end of this tutorial, you will have a WireGuard powered VPN running on your Raspberry Pi.
Equipment List
Below is the list of equipment that we used to set up WireGuard on our Raspberry Pi.
Recommended
Optional
This project on setting up a WireGuard VPN was tested on a Raspberry Pi 4 running the latest available version of Raspberry Pi OS Lite.
Video
This video will walk you through the steps of installing the WireGuard VPN to your Raspberry Pi.
We will also show an example of adding a WireGuard tunnel to a device using the generated QR code.
If you run into any issues be sure to check out the written version of our guide below
Adblock blocking the video? Support us by subscribing to our ad-free service.
Preparing your Raspberry Pi to install the WireGuard VPN
In this section, we will do some initial preparatory work to make sure our Raspberry Pi is ready to install the WireGuard VPN software.
1. The first thing we need to do is ensure our Raspberry Pi is using the latest available packages.
We can do that by running the following two commands.
2. We need to install the only package that we require to run the install scripts we need.
While this package should be available on most distributions of the Raspbian operating system, we will make sure by running the command below.
Installing WireGuard on the Raspberry Pi
Within this section, we are going to make use of the PiVPN script to install WireGuard.
PiVPN makes the process of installing WireGuard on our Raspberry Pi a straightforward process. The script sets up the best defaults for our device.
Starting the PiVPN Install Script
1. Let us start the installation process by running the following command.
This command will use curl to download the PiVPN setup script from their website and then pipe it straight to bash.
You can verify this script’s contents by going directly to the install PiVPN domain in your web browser.
Installing WireGuard to your Raspberry Pi
1. The first screen you will be greeted with will let you know what this script is about to do.
To start the WireGuard installation process, press the ENTER key.
2. The first thing that we will be configuring through this script is a static IP address.
This screen explains why your Raspberry Pi should have a static IP address when operating as a WireGuard VPN server.
To proceed, press the ENTER key to proceed.
3. You will be asked if you are already using DHCP reservation.
Using DHCP reservation allows you to make your router assign an IP address to your Raspberry Pi.
In this guide, we are going to assume you haven’t used DHCP reservation and will move on to set a static IP address on the Pi itself.
Select the option and press the ENTER key to continue.
4. To set a static IP address for the WireGuard software. The installation script will want to use your default settings.
If the default IP address and gateway are correct to you, then you can safely select the option.
Continue with this WireGuard set up guide by pressing the ENTER key.
5. You will be warned that you can potentially run into IP conflicts when using this method.
The way around that is to use DHCP reservation. However, most routers should be smart enough to stop this from being a problem.
Press the ENTER key to continue.
6. This screen will tell you that you need to specify a local user to store the WireGuard configuration files.
Continue to the next screen by pressing the ENTER key.
7. You can now select from a list of available users.
Use the ARROW keys to highlight the user then the SPACEBAR to select it.
Once you are happy with the user you have selected, press the ENTER key.
8. Finally, we can select the VPN software we want to install.
As we want to install WireGuard to our Raspberry Pi, you can press the ENTER key to continue.
The reason for this is that default by the PiVPN script selects WireGuard.
9. This screen will allow you to change the port the WireGuard uses on your Raspberry Pi.
It is recommended to keep this the same unless you have a particular reason to change the port.
Press the ENTER key to confirm the specified port.
10. This screen just confirms the port that you set your Raspberry Pi WireGuard VPN to use.
Confirm that the port is still correct, then press the ENTER key to proceed.
11. We can now specify the DNS provider that we want to use for our VPN clients.
For our tutorial, we chose to use the Cloudflare one as it is relatively speedy, and they purge their logs every 24 hours.
Use the ARROW keys to navigate through this menu. Once you have found the DNS provider you want to use, press the SPACEBAR key.
If you are happy with your selection, press the ENTER key to confirm it.
12. You can specify two different ways you want to access your WireGuard VPN.
Using your public IP address is the easiest option. However, this should only be used if you have a static IP address.
The other option is to use a domain name. You can set up this option by following our dynamic DNS guide.
For this guide, we will be sticking with using our public IP address.
Once you have the option you want to be selected, press the ENTER key to proceed.
13. The PiVPN script will now generate the server key that WireGuard requires.
All you need to do here is press the ENTER key again.
14. This screen will give you a quick rundown about unattended-upgrades and why you should enable them.
Go to the next step by pressing the ENTER key.
15. You can now enable the unattended-upgrades by selecting the option.
We highly recommend that you enable these to ensure your Raspberry Pi will download security fixes regulary.
Not enabling this will potentially leave your WireGuard VPN vulnerable to attack.
Once you have the option you want to be selected, press the ENTER key to confirm it.
16. You have now successfully installed the WireGuard VPN software to your Raspberry Pi.
This screen will let you know that you still need to create profiles for the users, which we will cover in the next section.
Press the ENTER key to continue to the last two steps.
17. You will be asked whether you want to restart your Raspberry Pi before continuing.
We recommend that you choose the option.
Once you have selected to reboot, press the ENTER key twice to restart.
Creating your First WireGuard Profile on your Raspberry Pi
Now that we have successfully installed the WireGuard software to our Raspberry Pi, we can create a profile for it.
To be able to create this profile, we will be making use of the PiVPN script again.
1. To begin creating a new profile for WireGuard, we need to run the following command.
2. All you need to do is type in a name for the profile that you are creating.
For example, we will be calling our profile “ PiMyLifeUp “.
Once you have created a profile, it will be stored within the directory specified in the output.
If you followed the previous steps and used the pi user, you will be able to find the config file within the /home/pi/configs directory.
You can use the config file within here to set up your WireGuard clients. However, there is another method which we will go into in the next section.
Generating a QR Code for your WireGuard Profile
In this section, we will show you how to generate a QR code for the WireGuard profile we generated on our Raspberry Pi.
You will be able to scan this QR code using your device. This saves you from having to copy the config file from your device.
Luckily for us, the PiVPN software comes with a QR code generator that we can use.
1. To generate a QR code for your profile, you will need to start by running the following command.
Make sure you replace “ PROFILENAME ” with the name you set in the previous section. In our case, this will be “ PiMyLifeUp “.
2. You can then scan this QR code using your iOS or Android devices.
You can find the WireGuard app on both the Google Play Store and the Apple App Store.
When scanning the QR code, you will be asked to enter a name for the profile.
At this point, you should now have successfully got a WireGuard VPN running on the Raspberry Pi.
If you have run into any issues or have any feedback, please feel free to leave a comment below.
WireGuard
Updated 27 September 2021
WireGuard is an extremely simple but fast VPN, that uses the most efficient encryption algorithms. It was meant to be faster, easier, more efficient that IPsec and OpenVPN, while providing more functionality. WireGuard was originally designed as an all-in-one VPN to work on both built-in interfaces and supercomputers suitable for a bunch of different tasks. WireGuard first came as a component of the Linux kernel. It has since become cross-platform, supported on Windows, macOS, BSD, iOS, and Android devices.
WireGuard was designed to be easy to install and configure. It can be easily implemented in several lines of code and easily checked for security issues. Compared to such mammoths as Swan/IPsec and OpenVPN/OpenSSL, where code parsing is beyond the reach of even important security experts, anyone can parse the WireGuard code on their own. WireGuard uses the best encryption protocols, such as Noise protocol framework, Curve25519, ChaCha20, Poly1305, BLAKE2, SipHash24, HKDF. Combining ultimate high-speed encryption algorithms and being part of the Linux kernel results in highly efficient secure networking. Check the documentation for detailed info on the protocol: PDF.
Server configuration
Installation
To install the tools required by WireGuard, run:
WireGuard¶
WireGuard is a fast, modern, secure Virtual Private Network (VPN) tunnel. It can securely connect you to your home network, allowing you to access your home network’s local services from anywhere. It can also secure your traffic when using public internet connections.
Installing WireGuard under IOTstack¶
You increase your chances of a trouble-free installation by performing the installation steps in the following order.
Step 1: Update your Raspberry Pi OS¶
To be able to run WireGuard successfully, your Raspberry Pi needs to be fully up-to-date. If you want to understand why, see the read only flag.
Step 2: Set up a Dynamic DNS name¶
Before you can use WireGuard (or any VPN solution), you need a mechanism for your remote clients to reach your home router. You have two choices:
Step 3: Understand the Service Definition¶
This is the service definition template that IOTstack uses for WireGuard:
Unfortunately, that service definition will not work «as is». It needs to be configured.
Step 4: Decide what to configure¶
With most containers, you can continue to tweak environment variables and settings without upsetting the container’s basic behaviour. WireGuard is a little different. You really need to think, carefully, about how you want to configure the service before you start. If you change your mind later, you generally have to start from a clean slate.
Fields that you should always configure¶
TZ= should be set to your local timezone. Example:
SERVERURL= should be set to the domain name you have registered with a Dynamic DNS service provider. Example:
PEERS= should be a comma-separated list of your client devices (all the phones, tablets, laptops, desktops you want to use remotely to get back into your home network). Example:
You have several options for how your remote peers resolve DNS requests:
PEERDNS=auto with custom-cont-init
This configuration instructs WireGuard to forward DNS queries from remote peers to any host daemon or container which is listening on port 53. This is the option you will want to choose if you are running an ad-blocking DNS server (eg PiHole or AdGuardHome) in a container on the same host as WireGuard, and you want your remote clients to obtain DNS resolution via the ad-blocker, but don’t want your Raspberry Pi host to use it.
Acknowledgement: thanks to @ukkopahis for developing this option.
To activate this feature:
Start the WireGuard container by executing:
This ensures that the
/IOTstack/volumes/wireguard folder structure is created and remote client configurations are (re)generated properly.
Run the following commands:
The presence of use-container-dns.sh causes WireGuard to redirect incoming DNS queries to the default gateway on the internal bridged network. That, in turn, results in the queries being forwarded to any other container that is listening for DNS traffic on port 53. It does not matter if that other container is PiHole, AdGuardHome, bind9 or any other kind of DNS server.
Do note, however, that this configuration creates a dependency between WireGuard and the container providing DNS resolution. You may wish to make that explicit in your docker-compose.yml by adding these lines to your WireGuard service definition:
Once activated, this feature will remain active until you decide to deactivate it. If you ever wish to deactivate it, run the following commands:
A third possibility is if you have a local upstream DNS server. You can specify the IP address of that server so that remote peers receive DNS resolution from that host. For example:
Do note that changes to PEERDNS will not be updated to existing clients, and as such you may want to use PEERDNS=auto unless you have a very specific requirement.
The WireGuard service definition template follows the convention of using UDP port «51820» in three places. You can leave it like that and it will just work. There is no reason to change the defaults unless you want to.
To understand what each port number does, it is better to think of them like this:
These definitions are going to be used throughout this documentation:
The «public» port is the port number that your remote WireGuard clients (phone, laptop etc) will try to reach. This is the port number that your router needs to expose to the outside world.
The «external» port is the port number that Docker, running on your Raspberry Pi, will be listening on. Your router needs to forward WireGuard incoming traffic to the «external» port on your Raspberry Pi.
The «internal» port is the port number that WireGuard (the server process) will be listening on inside the WireGuard container. Docker handles forwarding between the «external» and «internal» port.
See Understanding WireGuard’s port numbers if you want more information on how the various port numbers are used.
Step 5: Configure WireGuard¶
There are two approaches:
Of the two, the first is generally the simpler and means you don’t have to re-run the menu whenever you want to change WireGuard’s configuration.
Method 1: Configure WireGuard by editing docker-compose.yml ¶
Choose the «Build Stack» option.
Method 2: Configure WireGuard using compose-override.yml ¶
The Custom services and overriding default settings for IOTstack page describes how to use an override file to allow the menu to incorporate your custom configurations into the final docker-compose.yml file.
Use your favourite text editor to create (or open) the override file. The file is expected to be at the path:
Define overrides to implement the decisions you took in Decide what to configure. For example:
Choose the «Build Stack» option.
Check your work by running:
and verify that the wireguard service definition is as you expect.
Step 6: Start WireGuard¶
To start WireGuard, bring up your stack:
Confirm that WireGuard has started properly by running:
Repeat the command a few times with a short delay in between. You are looking for signs that the WireGuard container is restarting. If the container seems to be restarting then this command is your friend:
See also discussion of the read-only flag.
Confirm that WireGuard has generated the expected configurations. For example, given the following setting in docker-compose.yml :
you would expect a result something like this:
Step 7: Save your WireGuard client configuration files (QR codes)¶
The first time you launch WireGuard, it generates cryptographically protected configurations for your remote clients and encapsulates those configurations in QR codes. You can see the QR codes by running:
WireGuard’s log is ephemeral, which means it resets each time the container is re-created. In other words, you can’t rely on going back to the log to obtain your QR codes if you lose them.
See ssh tutorial if you need help setting up SSH (of which SCP is a part).
For example, to copy all PNG files from your Raspberry Pi to a target system:
If you want to work in the other direction (ie from the GUI-capable system), you can try:
Step 8: Configure your router with a NAT rule¶
A typical home network will have a firewall that effectively blocks all incoming attempts from the Internet to open a new connection with a device on your network.
To use a VPN from outside of your home network (which is precisely the point of running the service!), you need to configure your router to allow incoming WireGuard traffic to reach the Raspberry Pi running WireGuard. These instructions assume you have the privileges to do that.
If you have not used your router’s administrative interface before, the default login credentials may be physically printed on the device or in its instruction manual.
If you have never changed the default login credentials, you should take the time to do that.
Routers have wildly different user interfaces but the concepts will be the same. This section describes the basic technique but if you are unsure how to do this on your particular router model, the best idea would be to search the web for:
A typical configuration process goes something like this:
The NAT component you are looking for probably has a name like «Port Redirection», «Port Forwarding», «NAT Forwarding» or «NAT Virtual Server».
The configuration screen will contain at least the following fields:
| Field | Value |
|---|---|
| Interface | router’s WAN interface |
| Private IP | x.x.x.x |
| Private Port | «external» |
| Protocol | UDP |
| Public Port | «public» |
| Service Name | WireGuard |
The fields in the above list are in alphabetical order. They will almost certainly be in a different order in your router and may also have different names:
Private Port (or Internal Port) needs to be the value you chose for «external» in the WireGuard service definition (51820 if you didn’t change it).
Yes, this does sound counterintuitive but it’s a matter of perspective. From the router’s perspective, the port is on the private or internal part of your home network. From Docker’s perspective, the port is «external» to container-space.
Protocol will usually default to «TCP» but you must change it to «UDP».
Step 9: Configure your remote WireGuard clients¶
This is a massive topic and one which is well beyond the scope of this guide. You really will have to work it out for yourself. Start by Googling:
You will find the list of client software at WireGuard Installation.
For portable devices (eg iOS and Android) it usually boils down to:
Understanding WireGuard’s port numbers¶
Here’s a concrete example configuration using three different port numbers:
You also need to make a few assumptions:
Here’s a reference model to help explain what occurs:
The remote WireGuard client:
You configure a NAT port-forwarding rule in your router which accepts incoming traffic on the «public» UDP port (51620) and uses Network Address Translation to change the destination IP address to the Raspberry Pi and destination port to the «external» UDP port (51720). In other words, each incoming packet is readdressed to 192.168.203.60:51720.
Docker is listening to the Raspberry Pi’s «external» UDP port 51720. Docker uses Network Address Translation to change the destination IP address to the WireGuard container and destination port to the «internal» UDP port (51820). In other words, each incoming packet is readdressed to 172.18.0.6:51820.
The packet is then routed to the internal bridged network, and delivered to the WireGuard server process running in the container which is listening on the «internal» UDP port (51820).
A reciprocal process occurs when the WireGuard server process sends packets back to the remote WireGuard client.
The following table summarises the transformations as the client and server exchange information:
Even if you use port 51820 everywhere (the default), all this Network Address Translation still occurs. Keep this in mind if you are trying to debug WireGuard because you may actually find it simpler to understand what is going on if you use different numbers for the «public» and «external» ports.
This model is a slight simplification because the remote client may also be also operating behind a router performing Network Address Translation. It is just easier to understand the basic concepts if you assume the remote client has a publicly-routable IP address.
Debugging techniques¶
Monitor WireGuard traffic between your router and your Raspberry Pi¶
If tcpdump is not installed on your Raspberry Pi, you can install it by:
After that, you can capture traffic between your router and your Raspberry Pi by:
Press ctrl c to terminate the capture.
Monitor WireGuard traffic between your Raspberry Pi and the WireGuard container¶
First, you need to add tcpdump to the container. You only need to do this once per debugging session. The package will remain in place until the next time you re-create the container.
To monitor traffic:
Press ctrl c to terminate the capture.
Is Docker listening on the Raspberry Pi’s «external» port?¶
There will be a short delay. The expected answer is either:
Success implies that the container is also listening.
Is your router listening on the «public» port?¶
There will be a short delay. The expected answer is either:
The read-only flag¶
The :ro at the end of the following line in WireGuard’s service definition means «read only»:
The basic idea of containers is that processes are contained, include all their own dependencies, can be added and removed cleanly, and don’t change the underlying operating system.
Writing into /lib/modules is not needed on a Raspberry Pi, providing that Raspberry Pi OS is up-to-date. That is why the first step in the installation procedure tells you to bring the system up-to-date.
If WireGuard refuses to install and you have good reason to suspect that WireGuard may be trying to write to /lib/modules then you can consider removing the :ro flag and re-trying. Just be aware that WireGuard will likely be modifying your operating system.
Updating WireGuard¶
To update the WireGuard container:
If a new image comes down, then:
Getting a clean slate¶
If WireGuard misbehaves, you can start over from a clean slate. You may also need to do this if you change any of the following environment variables:
The procedure is:
If WireGuard is running, terminate it:
Erase the persistent storage area (essential):
Erasing the persistent storage area:
This will generate new client configurations and QR codes for your devices.
Remember to re-activate PEERDNS=auto with custom-cont-init if you need it.
How to Set Up WireGuard VPN Client on Android Phone
0. Prerequisites
You need a working WireGuard VPN server. Learn how to set that up here: How to Set Up WireGuard VPN Server on Ubuntu
1. Install
You can get the official app from: WireGuard Google Play Store.
2. Configure2.0. Keys
You can use your one of below host machine;
Run the following command to generate the public and private keys:
This places our keys under our /etc/wireguard/clients directory that we just created. As usual, DO NOT share your private key with anyone else, otherwise your VPN will be compromised.
You can view these files with cat :
2.1. mobile.conf File
Create configuration file,
and add following settings:
2.2. Add Mobile Client to Server
The last configuration step is to add your dekstip client’s public key and IP address to your server:
2.3. Configure Your Phone Connection
There are 2 ways of doing it and as we can see the last one is the easiest and preferred one.
2.3.1. Configure From Scratch2.3.2. Configure via QR Code
We are going to use qrencode package. First install it;
Then create QR Code from mobile.conf file that we created above;
In your WireGuard Android app;
3. Start WireGuard
Start WireGuard connection from toggle button on the main screen of your android app.
4. Test WireGuard
You can now check you IP searching on the browser what is my ip.
You should now see your YOUR_SERVER_IP_ADDRESS instead of your your local IP which your ISP provided.
Changelog
Установка WireGuard VPN на Ubuntu 20.04
Разберем установку и настройку WireGuard. Это бесплатный и быстрый VPN с открытым исходным кодом.
Подключаемся к нашему серверу через ssh и выполняем следующие команды.
Для начала обновим список пакетов на нашем сервере и установим их командами:
Теперь можно установить WireGuard:
Первое, что необходимо сделать, это сгенерировать пару ключей для сервера:
Создаем конфиг сервера:
Конфиге прописываем следующие строчки:
В PrivateKey прописываем содержимое из файла /etc/wireguard/privatekey. Так же в ListenPort можно подставить другое значение, если вы не хотите использовать номер порта по умолчанию. Address — это адрес сервера при соединении по VPN. PostUp и PostDown команды которые будут выполняться при активации и деактивации сетевого интерфейса wg0. Это команды для файрволла включающие форвардинг пакетов.
Так же не забудьте подставить вместо ens3 название вашего сетевого интерфейса, если он отличается.
Узнать названия сетевых интерфейсов можно командой:
Включаем поддержку IP форвардинга. Для этого открываем файл sysctl.conf.
Находим в нем строчку net.ipv4.ip_forward=1 и разкомментируем ее (убираем перед ней символ #).
Перезапускаем сервис, чтобы применить настройки:
Теперь включаем через systemctl демон WireGuard и запускаем его:
Выставляем для приватного ключа и конфига настройки доступа только для чтения:
Теперь займемся настройками клиентов. На официальном сайте WireGuard берем клиента для используемой вами операционной системы. Для телефонов на Android и iOS.
Генерируем ключи для клиента:
Открываем конфиг WireGuard
Дописываем ниже следующие строки:
В PublicKey подставляем содержимое созданного файла /etc/wireguard/client_publickey.
Перезагружаем в systemd сервис wireguard:
Теперь создадим конфиг client.conf для локальной машины клиента. Пропишем в него следующее:
В секции [Interface] в PrivateKey прописываем приватный ключ клиента /etc/wireguard/client_privatekey. В Address приписываем тот же адрес, что записывали в wg0.conf для этого клиента. В DNS можно прописать другие dns сервера (например 1.1.1.1) через запятую.
В секции [Peer] в PublicKey прописываем публичный ключ сервера из /etc/wireguard/publickey. В Endpoint вставим ip вашего сервера и порт для подключения, который вы указали в настройках. AllowedIPs указываем ip адреса с которых разрешено подключатся к серверу. Если оставить все нули, то весь трафик с компьютера будет идти через WireGuard. Опция PersistentKeepalive указывает через сколько секунд посылать пакеты на сервер, служит для поддержания соединения.
Теперь сохраняем этот конфиг на локальном компьютере и открываем его в клиенте WireGuard’а.
Как поставить персональный VPN WireGuard за 3 минуты
Помимо разработки обучающих материалов, я люблю копаться в различных технологиях, которые значительно упрощают жизнь в интернет пространстве. Одной из таких технологий является WireGuard — VPN, который сможет поставить абсолютно каждый.
Использование бесплатных VPN сервисов грозит тем, что ваши данные практически гарантированно будут переданы третьим лицам, так что ни о какой безопасности речи и быть не может.
Выбор сервера
Использовать WireGuard бесплатно не получится, для него требует сервер, который в наше время можно арендовать чуть ли не за копейки. Я рекомендую использовать сервер, который расположен в Германии — высокая скорость работы и минимум интернет ограничений.
Из всех поставщиков подобных серверов я рекомендую DigitalOcean, который отличается простой установкой, выгодной ценой (5$ в месяц) и высокой скоростью работы. Ссылка для регистрации:
DigitalOcean (по этой ссылке бесплатно получите 100$ для тестов).
Пройдя простую регистрацию, пополняете баланс на 5-10$, что в рублях на момент написания статьи составляет 370-740 рублей, после чего создаете каплю, то бишь Droplet:
Выбираете Ubuntu 20, план Basic, сервер за 5$ в месяц:
Далее выбираете страну, в которой будет создан сервер (Германия). В настройках также ставите галочки на IPv6, а также Monitoring (эту по желанию). Включив IPv6, вы сможете через свой VPN гулять по сайтам, которые уже поддерживают новый формат IP адресов:
Далее придумываете пароль и нажимаете “Create Droplet”:
Ждете несколько секунд — сервер создан и готов к использованию.
Подключение к серверу
Для подключения к серверу будем использовать программное обеспечение с открытым исходным кодом — Snowflake. Скачать его можно вот здесь:
Установив ПО, запускаем и добавляем новое подключение:
Нажимаем “New site” и заполняем данные для подключения к серверу:
Где “Host” пишем IP адрес, который нужно взять здесь:
В “User” пишем root, а в “Password” тот пароль, который вы придумали для своего сервера. В итоге должно получиться примерно так:
После чего нажимаем “Connect”. При подключении вы встретите окно примерного содержания:
Нажимаете “Yes” и вот, вы уже подключены к своему серверу.
Установка WireGuard
Для установки нужно перейти в Terminal:
Сама же установка WireGuard будет происходить из этого репозитария — GitHub.
Сначала установим инструмент curl:
Вставка в SnowFlake происходит по комбинации CTRL + SHIFT + V.
Затем скачиваем сам скрипт установки:
Делаем скрипт исполняемым:
И запускаем установку VPN:
В момент установки VPN система может запросить изменение конфига, соглашаемся, введя латинскую букву “y”:
В процессе установки скрипт также будет спрашивать, какие настройки ему следует использовать. Просто нажимаете “Enter”, что приведет к применению рекомендуемых настроек:
После применения рекомендуемых параметров, скрипт запросит у вас название для клиента:
Рекомендую писать туда название устройства, на котором будет применяться данный VPN. В процессе вы сможете создать еще несколько профилей для каждого из устройства. Это нужно для того, чтобы учитывать статистику трафика каждого девайса.
Подключение к WireGuard
После установки вы получите QR-код, который требуется отсканировать нужным устройством:
Выбираете “Создать из QR-кода” и сканируете код, который получили в Snowflake:
После чего в приложении появится ваш VPN, который уже можно включать и успешно пользоваться:
Если же VPN потребуется на компьютере, то следует скачать нужное ПО с официального сайта — https://www.wireguard.com/install/:
После чего нужно создать еще один клиент. Делается это всё с помощью данной команды:
Вводим цифру 5 — “Add WireGuard Peer” и также придумываем для клиента название:
После того, как новый клиент будет создан, переходим во вкладку “Files” и нажимаем на эту стрелочку:
Скачиваем его на компьютер и добавляем в ранее скаченную программу WireGuard:
Нажимаем “Подключить” и вуоля, всё работает.
Статистика
Статистику по трафику можно смотреть через терминал с помощью команды “wg”:
Учет статистики ведется от лица сервера, где:
Sent — количество принятой вашим устройством информации;
Received — количество отправленной вашим устройством информации.
ИП Мурзин Артем Сергеевич | ИНН 243001628387 | ОГРНИП 321246800063540
xei / wireguard-setup-scripts Goto Github PK
A set of shell scripts for setting up WireGuard VPN and Pi-hole ad blocker on a Linux server.
License: MIT License
wireguard-setup-scripts’s Introduction
Setup WireGuard VPN and Pi-hole ad blocker like a piece of cake 🍰
Here you can find some useful shell scripts in order to setup WireGuard VPN server and Pi-hole network-wide ad blocker on a Linux server as easily as possible.
A VPN (Virtual private network) extends your private network (e.g. the LAN in your office) across a public network (usually the Internet) so that the remote or mobile users and branch offices can connect to the private network remotely through the Internet in a secure way and access to corporate applications and private resources such as IP cameras, fax machines, private servers, etc.
The major applications of VPNs are:
Among these all, WireGuard seems to be the most interesting. It is lite (about 4,000 lines of code), fast and secure. So in 2020, WireGuard was officially added to the Linux kernel 5.6 release (so also Android kernels) by Linus Torvalds.
Pi-hole is a Linux network-level advertisement and Internet tracker blocking application which acts as a DNS sinkhole, intended for use on a private network.
The application acts as a DNS server for a private network (replacing any pre-existing DNS server provided by another device or the ISP), with the ability to block advertisements and tracking domains for users’ devices without installing any client-side software.
Because Pi-hole blocks domains at the network level, it is able to block advertisements, such as banner advertisements on a webpage, but it can also block advertisements in unconventional locations, such as on Android, iOS and smart TVs.
Using VPN services, Pi-Hole can block domains without using a DNS filter setup in a router. Any device that supports VPN can use Pi-Hole on a cellular network or a home network without a DNS server configured.
Setup the server
Here you can follow the instructions step by step to setup a VPN/AdBlocker server using WireGuard and Pi-hole.
Buy a linux server
WireGuard and Pi-hole are really lite softwares so that you can run them on a lite Linux instance with 1 vCore and 1GB of RAM without any problem.
The scripts are tested on Ubuntu 20.04 but you can run them on Debian, Fedora, CentOS and Arch Linux.
You can buy a cheap Linux IaaS from these cloud providers for the VPN server:
| Cloud Provider | Location | Price (starting at) | Traffic |
|---|---|---|---|
| Vultr | Worldwide (USA is recommended because of sanctions!) | $3.50/month | — |
| Digital Ocean | Worldwide (USA is recommended because of sanctions!) | $5/month | — |
| Hetzner | Germany (Finland did not work as VPN server for me!) | €3/month | 20 TB |
Clone the repository
Run the following commands to download the scripts:
Setup WireGuard server
Run the following command to setup the WireGuard server:
You have to answer some questions in order to configure the server. However you can leave the default values.
When you see the message WireGuard is setup successfully. you can go on.
Setup Pi-hole DNS sinkhole
Run the following command to start Pi-hole installer:
For more information about installer wizard vistit the official documentation.
Create a new peer (client)
Run the following command to create a new client (here named xei-pc ):
This command will generate a QR code that can be scanned by Wireguard client mobile application. It also generate a config file in /etc/wireguard/peers/xei-mobile/ directory that can be used instead of the QR code.
You have to modify the client’s config file and change DNS section to something like 1.1.1.1 or 8.8.8.8 if you are not going to setup Pi-hole or other DNS servers.
Revoke a peer (client)
You can remove a client by running the following command:
xei-mobile is the name of the client you want to remove.
Remove WireGuard server
You can remove the WireGuard server completely by running the following command:
Note that the above script will remove the directory /etc/wireguard and its contents including all peers’ config files. Backup the direcory if it is necessary.
Note that the above script will not remove Pi-hole. In order to remove Pi-hole visit its official documentation.
WireGuard client applications
When you create a new peer (client) with the above command, a config file will be generated in /etc/wireguard/peers/client-name/ directory that should be imported to WireGuard client application.
WireGuard client application is available in almost all platforms:
This repository is heavily inspired by a great similar repository by angristan.
donaldzou / WGDashboard Goto Github PK
Simplest dashboard for WireGuard VPN written in Python w/ Flask
License: Apache License 2.0
WGDashboard’s Introduction
Beta testing on v3.1
If anyone would love to try out the beta version of v3.1, you can do the following. Let me know if you encountered any issues. 😉
Please note that I still do push on this branch, and it might crash or not finish yet on some functionality 😉
Note: This project is not affiliate to the official WireGuard Project 😉
🎉 New Features
🪚 Bug Fixed
🧐 Other Changes
And many other small changes for performance and bug fixes! 😆
If you have any other brilliant ideas for this project, please shout it in here #129 ❤️
For users who is using v2.x.x please be sure to read this before updating WGDashboard 😉
Table of Content
Recommend the following OS, tested by our beloved users:
If you have tested on other OS and it works perfectly please provide it to me in #31. Thank you!
WireGuard and WireGuard-Tools ( wg-quick ) are installed.
WeeJeWel/wg-easy
Use Git or checkout with SVN using the web URL.
Work fast with our official CLI. Learn more.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
You have found the easiest way to install & manage WireGuard on any Linux host!
1. Install Docker
If you haven’t installed Docker yet, install it by running:
And log in again.
2. Run WireGuard Easy
To automatically install & run wg-easy, simply run:
💡 Replace YOUR_SERVER_IP with your WAN IP, or a Dynamic DNS hostname.
💡 Replace YOUR_ADMIN_PASSWORD with a password to log in on the Web UI.
💡 Your configuration files will be saved in
Are you enjoying this project? Buy me a beer! 🍻
To update to the latest version, simply run:
donaldzou/WGDashboard
Use Git or checkout with SVN using the web URL.
Work fast with our official CLI. Learn more.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
Beta testing on v3.1
If anyone would love to try out the beta version of v3.1, you can do the following. Let me know if you encountered any issues. 😉
Please note that I still do push on this branch, and it might crash or not finish yet on some functionality 😉
Note: This project is not affiliate to the official WireGuard Project 😉
🎉 New Features
🪚 Bug Fixed
🧐 Other Changes
And many other small changes for performance and bug fixes! 😆
If you have any other brilliant ideas for this project, please shout it in here #129 ❤️
For users who is using v2.x.x please be sure to read this before updating WGDashboard 😉
Table of Content
Recommend the following OS, tested by our beloved users:
If you have tested on other OS and it works perfectly please provide it to me in #31. Thank you!
WireGuard and WireGuard-Tools ( wg-quick ) are installed.
How to configure a WireGuard Android VPN Client
In this section of the Gain Flexibility & Increase Privacy with WireGuard VPN mini-course, we are going to be configuring WireGuard VPN on an Android device.
This is what it looks like:
Download the WireGuard App
Configure your connection
Once the app is downloaded, we need to add a new configuration file.
Rather than typing in everything manually, let’s use the QR code we generated from my other post to quickly import.
It will ask for camera permission, then you should be able to scan your code.
You’ll be prompted to confirm your action, but you should definitely press OK.
Add your client to your server
Your client is configured, but you need to authorize it on your server.
ON YOUR SERVER run this command:
IMPORTANT: You need to replace YOUR_CLIENT_PUBLIC_KEY and YOUR_CLIENT_VPN_IP
Getting connected
All you need to do now when you want to connect is open your WireGuard app and turn it on.
Test your connection
The easiest way to test your connection is visiting fast.com and dnsleaktest.com to make sure that everything is performing well.
It’s really that easy!
I hope you found this post to be helpful. If you have any questions, you can ask me in the comments below or ask me on Twitter. If you like content like this, sign up on our mailing list.
Support future content
Written By Jay
Like this? Subscribe
We’re privacy advocates. We will never spam you and we only want to send you emails that you actually want to receive. One-click unsubscribes are instantly honored.

You’ve enjoyed another post by Server Side Up (hosted by Vultr).
net/wireguard: Generate QR-Code with qrencode? #1868
Comments
white-rabbit07 commented May 30, 2020 •
The text was updated successfully, but these errors were encountered:
fabianfrz commented May 31, 2020
Just a short response for @mimugmail:
rendering QR-Codes in OPNsense is already possible. There is a jQuery plugin in the frontend which is used for 2FA:
if @mimugmail wants to, he can create the config file (maybe via backend API) and use the existing QR code rendering lib to render it.
mimugmail commented Jun 1, 2020
Due to Corona my time is very limited and currently I’m working on different projects. I don’t plan any new features this year, but if anyone else wants to jump in I’m happy to help/test.
EneOli commented Jun 1, 2020
I looked into the plugin code and it shouldn’t be that hard to implement it. I also tried to implement this feature, but the opnsense_bootgrid_plugin.js that is responsible for rendering the table seems to be very limited. Is there an option to add a custom command or a custom cell with own html to it?
EneOli commented Jun 1, 2020
I did a mistake. Generating the client config in opnsense is impossible because of the missing client private key.
Generating the server config is useless, because it is already applied in opnsense.
The only option is to also generate client keys in the server and store them temporarily while creating the client config. But I don’t think that’s a good solution. Maybe asking for the key in the ui before generating the config is an option?
mimugmail commented Jun 2, 2020
I think the only way it makes sense is when OPN also handles client keys, but this would break most of the open-ness of the system.
white-rabbit07 commented Jun 2, 2020
pkejval commented Jul 7, 2020
But WG client can generate its private key from given public key in config, isn’t it? There’s no need to store clients private keys on the firewall. I am pretty sure that I saw this implemented in OpenWRT and DD-WRT.
mimugmail commented Jul 7, 2020
ChristianUlbrich commented Aug 3, 2020
The twist is, the keys would not needed to be stored; but the frontend could generate them locally. Basically it would involve integrating something like https://www.wireguardconfig.com/ into the plugin.
AdSchellevis commented Dec 16, 2020
This issue has been automatically timed-out (after 180 days of inactivity).
For more information about the policies for this repository,
please read https://github.com/opnsense/plugins/blob/master/CONTRIBUTING.md for further details.
If someone wants to step up and work on this issue,
just let us know, so we can reopen the issue and assign an owner to it.
How to install and configure your own VPN server in GCP with Wireguard
Security is one of the most important things now days specifically in enterprise environments, a vpn helps to encrypt traffic from client to internet. Wireguard is a vpn protocol than works on the kernel side and acts like a network interface, is one of the most modern vpn protocols it’s based in public and private key exchange just like ssh does. A vpn can connect different host with encrypted connection throught internet, this topology can connect a simple client in an android app or even connect different hosts across datacenters, for example to connect workers in Kubernetes/swarm cluster in different datacenters regions with encrypted connection without open any public API on internet, wireguard also can be used to connect different home based host across internet only opening one UDP port and use the vpn server as encrypted bridge between clients.
In this tutorial we focus on implementation of vpn server on Google Cloud Platform (GCP) with wireguard, this setup will use a centos 8 on the server-side, and the configuration of one client in android device.
Server-side setup
In the server side we will use CentOS 8 in GCP, the steps are:
Create virtual host in GCP
In this step we need to have an account in Google Cloud Platform and create a vm instance in compute engine. In this step you need to select the vm resource of you preference, in my case I choose a general purpose virtual machine with E2 series processor, I select the e2-small configuration with 2 vCPU and 2GB of ram, finally I choose centos 8 with 20 GB of ssd storage, the configuration is showed in next image.
Setup ssh keys
In order to access to our virtual machine, we need to create a ssh key, the ssh key are create with this command
Exit fullscreen mode
And, restrict the access of the key
Exit fullscreen mode
Get public ssh key and copy
Copy directly from command line output
Exit fullscreen mode
Copy with xclip from command line
Exit fullscreen mode
Exit fullscreen mode
Install Wireguard
Before install wireguard we need to update the system
Exit fullscreen mode
Then, we need to install some repositories
Exit fullscreen mode
Finally, install wireguard kmod and wireguard tools
Exit fullscreen mode
Configure Wireguard Server
Before creating the wireguard config file is necessary to generate public and private key
First change to root user
Exit fullscreen mode
Go to /etc/wireguard directory
Exit fullscreen mode
Limit default file permission of root user
Exit fullscreen mode
Generate public and private key
Exit fullscreen mode
Create a wireguard config file in /etc/wireguard/wgserver.conf and add the following lines
Exit fullscreen mode
Add firewall rules in GCP
Enable wireguard server at boot with systemd
ngoduykhanh/wireguard-ui
Use Git or checkout with SVN using the web URL.
Work fast with our official CLI. Learn more.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
A web user interface to manage your WireGuard setup.
Using binary file
Download the binary file from the release and run it with command:
Using docker compose
You can take a look at this example of docker-compose.yml. Please adjust volume mount points to work with your setup. Then run it like below:
| Variable | Description |
|---|---|
| SESSION_SECRET | Used to encrypt the session cookies. Set this to a random value. |
| WGUI_USERNAME | The username for the login page. (default admin ) |
| WGUI_PASSWORD | The password for the user on the login page. (default admin ) |
| WGUI_ENDPOINT_ADDRESS | The default endpoint address used in global settings. (default is your public IP address) |
| WGUI_DNS | The default DNS servers (comma-separated-list) used in the global settings. (default 1.1.1.1 ) |
| WGUI_MTU | The default MTU used in global settings. (default 1450 ) |
| WGUI_PERSISTENT_KEEPALIVE | The default persistent keepalive for WireGuard in global settings. (default 15 ) |
| WGUI_FORWARD_MARK | The default WireGuard forward mark. (default 0xca6c ) |
| WGUI_CONFIG_FILE_PATH | The default WireGuard config file path used in global settings. (default /etc/wireguard/wg0.conf ) |
| BASE_PATH | Set this variable if you run wireguard-ui under a subpath of your reverse proxy virtual host (e.g. /wireguard)) |
Defaults for server configuration
These environment variables are used to control the default server settings used when initializing the database.
| Variable | Description |
|---|---|
| WGUI_SERVER_INTERFACE_ADDRESSES | The default interface addresses (comma-separated-list) for the WireGuard server configuration. (default 10.252.1.0/24 ) |
| WGUI_SERVER_LISTEN_PORT | The default server listen port. (default 51820 ) |
| WGUI_SERVER_POST_UP_SCRIPT | The default server post-up script. |
| WGUI_SERVER_POST_DOWN_SCRIPT | The default server post-down script. |
Defaults for new clients
These environment variables are used to set the defaults used in New Client dialog.
In order to sent the wireguard configuration to clients via email, set the following environment variables:
Auto restart WireGuard daemon
WireGuard-UI only takes care of configuration generation. You can use systemd to watch for the changes and restart the service. Following is an example:
alectrocute/wg-api
Use Git or checkout with SVN using the web URL.
Work fast with our official CLI. Learn more.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
wg-api is an API endpoint for a Wireguard® VPN server. It allows you to make HTTP GET requests with JSON responses, enabling you to create & revoke peers (eg. clients), access QR/plaintext/JSON config files and receive realtime server info.
It also currently includes an installer script to configure your Wireguard® interface correctly as per wg-api’s construction.
Use a fresh Ubuntu 18.* install with up-to-date apt dependencies, with Node and NPM installed and Wireguard uninstalled.
Then get your Wireguard® server up and running:
Быстрая установка Wireguard в Ubuntu 16.04
Установим и настроим Wireguard за несколько минут
До недавнего времени я пользовался исключительно OpenVPN, о поднятии которого я писал ранее:
И ввиду относительно невысокой скорости моего интернета я полагал, что мне его будет достаточно. Но все познается в сравнении.
Для общего развития решил поднять у себя Wireguard и был приятно удивлен. Например, скорость подключения Wireguard — она моментальная, тогда как OpenVPN требуется секунд 5-7. Ну и сама скорость соединения, конечно. С Wireguard я не вижу разницы — подключен VPN или нет, скорость практически одинаковая. На OpenVPN просадка была даже больше чем в 2 раза.
Как обстоят дела с высокоскоростными подключениями я на своем опыте не скажу, но никто не мешает взглянуть на многочисленные сравнения Wireguard с OpenVPN, о которых написано немало.
Теперь об установке. Можно все составлять руками, достаточно открыть документацию Wireguard. Но я нашел на гитхаб скрипт быстрой настройки конфига.
Для начала нужно добавить репозиторий WireGuard:
И выполнить обновление пакетов:
Теперь установим Wireguard и другие необходимые пакеты:
Затем качаем сам скрипт:
И даем ему права на выполнение:
Теперь запустим скрипт командой:
После первого запуска скрипт создаст файл конфигурации для сервера и для одного клиента, а так же выведет QR код, который можно отсканировать в мобильном приложении WireGuard
Если нужно добавить еще клиентов — просто запускаем скрипт еще раз, конфиг будет создан.
Все конфиги будут лежать в том каталоге, откуда запускаем скрипт. Конфиги будут с именами wgclient_10.conf, wgclient_11.conf и т.д., по порядку.
Так же можно задать имя конфига при выполнении скрипта, для удобства:
Теперь добавляем сервис WireGuard в автозапуск:
Для просмотра подключений используется команда:
После добавления новых клиентов обновляем конфиг и выполняем перезагрузку сервиса:
Update 23.03.2022:
Все пользователи (peer) и их ключи перечислены в файле wghub.conf. Вот так он выглядит после создания первого:
Чтобы удалить определенного клиента — peer, удаляем запиь о нем (на скрине выше выделил красным) из файла wghub.conf
Сохраняем, обновляем конфиг и перезапускаем WireGuard командами:
axllent/wireguard-vanity-keygen
Use Git or checkout with SVN using the web URL.
Work fast with our official CLI. Learn more.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
WireGuard vanity keygen
A command-line vanity (public) key generator for WireGuard. It only matches the prefix of generated public keys, and not whether the search matches anywhere in the public key. The concept is based on wireguard-vanity-address, however I wanted something a little more streamlined.
What characters can I search for?
Why does test & tes1 show different probabilities despite having 4 characters each?
How accurate are the estimated times?
They are not (and cannot be) accurate. Keys are completely randomly generated, and the estimate is based on a law of averages. For instance, you could find a match for a one in a billion chance on the very first hit, or it could take you 5 billion attempts. It will however give you an indication based on your CPU speed, word count, case sensitivity, and use of numbers or characters.
Why do I need this?
You don’t. I wrote it because I run a WireGuard server, which does not provide any reference as to who the key belongs to ( wg on the server). Using vanity keys, I can at least identify connections. I also wanted to learn more about multi-core processing in Golang.
linuxserver/docker-wireguard
Use Git or checkout with SVN using the web URL.
Work fast with our official CLI. Learn more.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md





The LinuxServer.io team brings you another container release featuring:






WireGuard® is an extremely simple yet fast and modern VPN that utilizes state-of-the-art cryptography. It aims to be faster, simpler, leaner, and more useful than IPsec, while avoiding the massive headache. It intends to be considerably more performant than OpenVPN. WireGuard is designed as a general purpose VPN for running on embedded interfaces and super computers alike, fit for many different circumstances. Initially released for the Linux kernel, it is now cross-platform (Windows, macOS, BSD, iOS, Android) and widely deployable. It is currently under heavy development, but already it might be regarded as the most secure, easiest to use, and simplest VPN solution in the industry.
We utilise the docker manifest for multi-platform awareness. More information is available from docker here and our announcement here.
Simply pulling lscr.io/linuxserver/wireguard:latest should retrieve the correct image for your arch, but you can also pull specific arch images via tags.
The architectures supported by this image are:
| Architecture | Available | Tag |
|---|---|---|
| x86-64 | ✅ | amd64- |
| arm64 | ✅ | arm64v8- |
| armhf | ✅ | arm32v7- |
During container start, it will first check if the wireguard module is already installed and loaded. Kernels newer than 5.6 generally have the wireguard module built-in (along with some older custom kernels). However, the module may not be enabled. Make sure it is enabled prior to starting the container.
With regards to arm32/64 devices, Raspberry Pi 2-4 running the official ubuntu images or Raspbian Buster are supported out of the box. For all other devices and OSes, you can try installing the kernel headers on the host, and mapping /usr/src:/usr/src and it may just work (no guarantees).
This can be run as a server or a client, based on the parameters used.
If the environment variable PEERS is set to a number or a list of strings separated by comma, the container will run in server mode and the necessary server and peer/client confs will be generated. The peer/client config qr codes will be output in the docker log. They will also be saved in text and png format under /config/peerX in case PEERS is a variable and an integer or /config/peer_X in case a list of names was provided instead of an integer.
To add more peers/clients later on, you increment the PEERS environment variable or add more elements to the list and recreate the container.
Do not set the PEERS environment variable. Drop your client conf into the config folder as /config/wg0.conf and start the container.
If you get IPv6 related errors in the log and connection cannot be established, edit the AllowedIPs line in your peer/client wg0.conf to include only 0.0.0.0/0 and not ::/0 ; and restart the container.
Road warriors, roaming and returning home
If you plan to use Wireguard both remotely and locally, say on your mobile phone, you will need to consider routing. Most firewalls will not route ports forwarded on your WAN interface correctly to the LAN out of the box. This means that when you return home, even though you can see the Wireguard server, the return packets will probably get lost.
This is not a Wireguard specific issue and the two generally accepted solutions are NAT reflection (setting your edge router/firewall up in such a way as it translates internal packets correctly) or split horizon DNS (setting your internal DNS to return the private rather than public IP when connecting locally).
Both of these approaches have positives and negatives however their setup is out of scope for this document as everyone’s network layout and equipment will be different.
Maintaining local access to attached services
When routing via Wireguard from another container using the service option in docker, you might lose access to the containers webUI locally. To avoid this, exclude the docker subnet from being routed via Wireguard by modifying your wg0.conf like so (modifying the subnets as you require):
to the additional subnets you’d like to add, comma separated and excluding the peer IP (ie. «192.168.1.0/24,192.168.2.0/24» ). Replace
with either the name or number of a peer (whichever is used in the PEERS var).
Keep in mind that this var will only be considered when the confs are regenerated. Adding this var for an existing peer won’t force a regeneration. You can delete wg0.conf and restart the container to force regeneration if necessary.
Don’t forget to set the necessary POSTUP and POSTDOWN rules in your client’s peer conf for lan access.
Here are some example snippets to help you get started creating a container.
WireGuard VPN Road Warrior Setup
WireGuard is a relatively new open-source software for creating VPN tunnels on the IP layer using state of the art cryptography. I attended a self-organized session by the creator and developer Jason Donenfeld at the 34c3 who explained how WireGuard works and how it can be used. I was quite impressed by it’s simplicity and gave it a try. It worked more or less out of the box. Now I created a more advanced setup for accessing my home network.
In this blog post, I will describe how you can use it to remotely access your home or corporate network from any external network as a so-called road warrior.
WireGuard VPN Software
Here is a good talk from the WireGuard developer Jason Donenfeld explaining what WireGuard can do and how it works: https://www.youtube.com/watch?v=eYztYCbV_8U:
Some key features from this talk:
More infos, a whitepaper, setup instructions or demos can be found on the project website: https://www.wireguard.com/.
At some point, WireGuard will be integrated directly into the Linux kernel. Linus Torvalds said “it’s a work of art” and hopes it will be merged soon into the kernel: https://lists.openwall.net/netdev/2018/08/02/124.
Road Warrior Scenario
A road warrior is a person that uses a mobile client (e.g. notebook or mobile phone) to connect to their corporate or home network.
Features of this setup:
Note: If the road warrior establishes a VPN connection with the mobile phone and uses the mobile phone as a WiFi hotspot for another device (like a notebook), the traffic from the WiFi hotspot is not routed through the VPN. I’m not sure why this is the case but this is maybe a limitation of the OS on the mobile phone.
WireGuard Software Installation
Install WireGuard according to the installation instructions (https://www.wireguard.com/install/).
Debian
Adding the WireGuard repo and install the wireguard package:
Raspberry Pi
On a Raspberry Pi, you have to compile it manually according to these installation instructions: https://github.com/adrianmihalko/raspberrypiwireguard. However, you don’t need to install the kernel headers via rpi-soruce as mentioned. The following commands are enough for the installation on a Raspberry Pi:
Arch Linux
Installing two wireguard packages from the official repositories and the linux-headers package (this is needed because the Wireguard module is installed as a DKMS module):
Android
Install the WireGuard app from the play store: https://play.google.com/store/apps/details?id=com.wireguard.android&hl=en. This application implements WireGuard in the userspace. Therefore, the phone does not have to be rooted in order to use WireGuard.
Installation Test
You can test if the kernel module wireguard is loaded:
Server Key Generation
To ensure that all the files have the correct permissions (only readable and writeable by the file owner, which in this case is the user root), the umask has to be set to 077:
The configuration is performed in the /etc/wireguard directory. Generate a private and public key for the server:
Example server keys:
Client Key Generation
Generate a private and public key for every client. Note: These keys can also completely be generated on the client.
The same for the mobile phone:
Server Configuration
WireGuard
Create a new configuration file for the server in /etc/wireguard/wg0.conf. The filename specifies the name of the VPN network interface. In this case, the new network interface will be named wg0.
Configuration explanation Interface section:
Configuration explanation Peer section:
IP Forwarding
IP forwarding has to be enabled on both IPv4 and IPv6. Creating the configuration file /etc/sysctl.d/wireguard.conf:
Loading the configuration:
Client Configuration
Routing all Traffic (Default Route)
Configuration file which will route all traffic through the VPN:
Configuration explanation Interface section:
Configuration explanation Peer section:
Split Tunneling
Configuration file which will route only the traffic for the VPN (10.23.5.0/24 and fc00:23:5::/64) and for the remote network (192.168.1.0/24) through the VPN.
The only difference is the AllowedIPs directive, which creates a split tunneling VPN setup. Only the traffic for the provided networks is routed through the VPN.
Considerations when using NAT or stateful Firewalls
If the server is behind a NAT or a stateful firewall and the client does not send any traffic to the server for a certain time, the NAT router/firewall will remove the host state from the connection table. When now a server sends a packet to the client, the client would not be able to receive this packet anymore, because the NAT router/firewall does not know what to do with this packet. To fix this issue, the PersistentKeepalive option can be used to periodically send an empty authenticated packet to the server to keep the connection open. WireGuard proposes a value of 25 seconds that would work with a wide variety of firewalls. (Thanks Ramesh for the comment on that.)
So, if the server is behind a NAT or stateful firewall, the following option should be added in the Peer section of the client configuration:
Server Usage
Start/Stop Manually
Starting the VPN server manually:
Stopping the service again:
Start/Stop using systemd
Starting the service:
Showing details about the service:
Stopping the service again:
The service is now stopped:
Automatically start the service when the system is started:
Disable the service on startup again:
Verifying
A new network interface wg0 is created when the service is started:
The route is sent according to the AllowedIPs directive:
Showing the current configuration:
More data are shown if the clients are connected:
Showing the detailed interface configuration:
Client Usage
Copying the client configuration file to /etc/wireguard:
Starting the service in the same way as on the server:
A new network interface was created:
Showing the connection:
Because the AllowedIPs directive is configured to 0.0.0.0/0 and ::/0, all traffic is routed through the VPN:
Both IPv4 and IPv6 works through the tunnel:
Stoppping the VPN:
Starting via a systemd service:
Stopping via systemd:
Mobile Client Usage
Generating a QR code for the mobile client:
Adding a new VPN connection by selecting Create from QR code:
Scanning the QR code:
Enabling the VPN:
A new network interface was created with the configured IP addresses:
Accessing the remote network:
It’s also possible to reach other VPN clients (the firewall does not prevent that):
Because split tunneling is used, the normal network traffic does not go through the VPN box:
Debugging (Update from 2019-03-23)
Wireshark
Wireshark has a dissector for WireGuard:
More infos on how to decrypt data within Wireshark by providing key logs can be fond here: https://github.com/Lekensteyn/wireguard-dissector.
Using nftables (Update from 2021-04-18)
If you want to use nftables instead of iptables on the Wireguard server, you can do this without problems. You have to configure nftables accordingly.
Because several commands are used to configure nftables, it makes sense to use own scripts in the Wireguard server configuration:
This script allows forwarding between the Wireguard VPN and the LAN connected interface and adds the NAT rules for IPv4 and IPv6.
This script removes the added rules. The NAT rules have to be removed via a handler ID because it’s at the moment not possible to remove them via the same syntax as they were added (like in iptables).
Restart your Wireguard server and you are ready to go.
How to configure a WireGuard iOS client
This is a coniutation of my free “mini-course” called Gain Flexibility & Increase Privacy with WireGuard VPN. Start there if you are new to WireGuard.
What you’ll achieve
This is what it looks like:
Prerequisites
Download WireGuard app from the App Store
Add a tunnel
We need to add a tunnel:
We then want to choose “Create from QR code”:
Using the QR code that we generated on our server, we can now hold our camera up to our QR code to import it. Give it a descriptive name for your connection.
You may be prompted to add this VPN configuration. Be sure to allow it so you can access it through the iOS settings page.
You’ll see it automatically imports everything, similar to our other clients that we have been working with.
You can set the On demand to be “on” if you want to always use your VPN (over LTE and Wi-Fi).
Add your client to your server
Before you can connect, you need to add the client to your server. I go through this on why we need to do this here, but here is the quick solution.
ON YOUR SERVER run this command:
IMPORTANT: You need to replace YOUR_CLIENT_PUBLIC_KEY and YOUR_CLIENT_VPN_IP
Connecting to the VPN
You can now access the VPN from the “Settings” page of iOS.
tusc/wireguard-kmod
Use Git or checkout with SVN using the web URL.
Work fast with our official CLI. Learn more.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
WireGuard kernel module for UnifiOS (UDM, UDR, UXG)
Author: Carlos Talbot (Tusc00 on reddit, @tusc69 on ubnt forums)
The tar file in this repository is a collection of binaries that can be loaded onto a UDM/UDM Pro to run WireGuard in kernel mode. WireGuard is a high performance vpn solution developed by Jason Donenfeld ( https://www.wireguard.com/ ). «WireGuard» and the «WireGuard» logo are registered trademarks of Jason A. Donenfeld.
Please see below for instructions on how to install the prebuilt kernel module and associated utils.
Table of Contents
The Unifi UDM is built on a powerful quad core ARM64 CPU that can sustain up to 800Mb/sec throughput through an IPSec tunnel. There has been a large interest in a kernel port of WireGuard since performance is expected to be similar if not more. This kernel module was built using the WireGuard backport as the UDM runs an older kernel(4.1.37). If you want to compile your own version, there will be a seperate build page posted soon. This was built from the GPL sources Ubiquiti sent me. I have a seperate github page for the Ubiquiti UDM GPL source code: https://github.com/tusc/UDM-source-code/blob/main/README.md
We first need to download the tar file onto the UDM. Connect to it via SSH and type the following command to download the tar file. You need to download the following tar file. NOTE: always check this link for the latest release.
From this directory type the following to extract the files:
For the UDM, UDM-Pro, UDM-SE, or UXG-Pro, extract the files into /mnt/data/wireguard
For the UDR, extract the files into /data/wireguard
Once the extraction is complete, cd into /mnt/data/wireguard (or /data/wireguard for UDR) and run the script setup_wireguard.sh as shown below
This will setup the symbolic links for the various binaries to the /usr/bin path as well as create a symlink for the /etc/wireguard folder and finally load the kernel module. You’ll want to run dmesg to verify the kernel module was loaded. You should see something like the following:
The script will first try to load the built-in wireguard module if it exists. If it doesn’t exist, the external module provided by this package will be loaded instead. You can set LOAD_BUILTIN=0 at the top of the setup_wireguard.sh script to always load the external module. Note that only recent UDM releases since 1.11.0 have the built-in module, and it is not always up-to-date.
The tar file includes other useful utils such as htop, iftop and qrencode.
Build from source
To build this package please follow this README
Please Note: you will need to run setup_wireguard.sh whenever the UDM is rebooted as the symlinks have to be recreated.
You can safely download new versions and extract over prior releases.
Issues loading module
If you see the following then you are running a firmware that currently doesn’t have a module built for it.
Please reach out and send me a copy of the output from above.
There’s a sample WireGuard config file in /etc/wireguard you can use to create your own, provided you update the public and private keys. You’ll want to copy the sample config and use VI to edit it. You can also just copy an existing config from another server you want to use.
There are various tutorials out there for setting up a client/server config for WireGuard (e.g. https://www.stavros.io/posts/how-to-configure-wireguard/ ). A typical config might be to allow remote access to your internal LAN over the WAN from a mobile phone or romaing laptop. For the purpose of this example, the UDM is the server and the phone/laptop the client. For this you would need to setup a config file on the UDM similar to the following:
The corresponding config on the phone/laptop (client) would look like this:
You’ll need to generate keys on both systems. This can be done with the following command:
Finally, don’t forget to open a port on the firewall in order to allow remote access to the wireguard link. You’ll want to create this rule on the UDM under the WAN LOCAL section of the firewall settings. The default port is 51820 which can be adjusted in the wireguard config file, just make sure to update the firewall rule accordingly. An example of a rule is available here: WireGuard Rule. Note: you’ll need to create a port group which can be done during rule creation: Port Group.
Once you have a properly configured conf file, you need to run this command from the cli:
you should see output similar to the following:
You can also execute the wg binary for status on the tunnel:
I’m currently testing throughput using iperf3 between a UDM Pro and an Ubuntu client over 10Gb. With the UDM as the iperf3 server I’m seeing up to 1.5Gb/sec.
Finally, in order to shutdown the tunnel you’ll need to run this command:
The built-in dnsmasq on UnifiOS is configured to only listen for requests from specific interfaces. The wireguard interface name (e.g.: wg0) needs to be added to the dnsmasq config so it can respond to requests from the tunnel. You can run the following to add wg0 to the dnsmasq interface list:
You can also those commands to PostUp in your wireguard config’s Interface section to automatically run them when the tunnel comes up, e.g.:
If you have mutliple WANs or are using the UniFi Redundant WAN over LTE, you’ll notice the WireGuard connection stays active with the failover link when the primary WAN comes back. A user has written a script to reset the WireGuard tunnel during a fail backup. You can find it at the link below. Just drop it in the startup directory /mnt/data/on_boot.d just like the setup script above.
If you gererate the client keys on the UDM you can use qrencode which has been provided for easy configuration on your IOS or Android phone. Just pass the client configuration file to qrencode as shown below and import with your mobile WireGuard client:
Wireguard qr code generate
WireGuard – VPN протокол с открытым исходным кодом, обеспечивающий высокую скорость при минимальной нагрузке.
В современном мире VPN нужен практически всем. Ведь не только для доступа к заблокированным ресурсам можно получить доступ, но и для объединения разных устройств подключенных к интернету и расположенных географически в разных местах.
Особенности WireGuard
Установка
Установка wireguard будет производится на VPS с ОС Debian 11.
Для начала подключаемся к нашему серверу по ssh.
Ставим последние обновления.
Теперь можно устанавливать WireGuard
Для Debian 10 необходимо будет добавить backport репозиторий.
И после установки скорее всего потребуется перезагрузка для Debian 10
На одноранговом узле, который будет действовать как «сервер», необходимо включить пересылку IPv4 с помощью sysctl
Настройка firewall
Нужно открыть порт 51820/UDP
Настройка WireGuard на сервере
Генерируем публичный и приватный ключ сервера.
Создаём конфиг файл.
И добавим в него следующее:
Запуск сервиса wireguard
Теперь пробуем поднять наш wireguard интерфейс. Запускаем службу и сразу смотрим статус или всё запустилось.
Если запустилось нормально, можем ставить в автозагрузку:
Также можно посмотреть статус именно нашего интерфейса wg0 и подключенных к нему пиров.
Настройка клиента linux
Устанавливаем wireguard пакет
Archlinux
Ubuntu/Debian
На сервере генерируем ключи для клиента:
И теперь обновим на сервере файл wg0.conf
И добавим туда новый раздел с новым клиентом
Перезапускаем сервис после добавления нового клиента
Запускаем сервис и сразу смотрим статус на клиенте:
Также созданный файл для клиента можна импортировать через GUI Network менеджера.
Настройка клиента Android
Устанавливаем из андроид маркета офф. приложение wireguard
На сервере делаем ключи для клиента:
Добавляем на сервере в файл wg0.conf новый пир:
Перезапускаем сервис на сервере:
Создаем конфиг файл для телефона. Подставив ключи и IP адреса.
Нужно перенести этот конфиг на смартфон, но значительно удобнее использовать QR код.
Для этого нужно установить qrencode
Дальше указываем конфиг файл и генерируем QR код.
После этого в консоли мы увидим QR код и нам остается только отсканировать его через WireGuard на мобильном приложении.
Настройка клиента Mikrotik
Для роутеров Mikrotik поддержка wireguard есть только в 7 версии routerOS, а она пока что в стадии development(не для продакшена).
Поставил версию 7.1rc4 на MikroTik hAP lite (RB941-2nD), пока работает стабильно.
На момент написания поста доступна версия 7.1rc4
Добавляем wireguard интерфейс.
Добавляем пир. Указав созданный интерфейс, публичный ключ нашего сервера, IP адрес сервера, порт, разрешенные сети( 0.0.0.0/0 для всего трафика или только для доступа к нашей сети 10.0.0.0/24 ) и KeepAlive.
И обязательно добавляем ip адрес на наш wireguard интерфейс.
IP > Addresses
Нажимаем ‘+’, вписываем наш ip, который мы выбрали для клиента(например 10.0.0.3/24), и выбираем наш интерфейс.
Wireguard qr code generate
Copy raw contents
Home Assistant Community Add-on: WireGuard
WireGuard® is an extremely simple yet fast and modern VPN that utilizes state-of-the-art cryptography. It aims to be faster, simpler, leaner, and more useful than IPsec, while avoiding the massive headache.
It intends to be considerably more performant than OpenVPN. WireGuard is designed as a general-purpose VPN for running on embedded interfaces and supercomputers alike, fit for many different circumstances.
Initially released for the Linux kernel, it is now cross-platform (Windows, macOS, BSD, iOS, Android) and widely deployable, including via an Hass.io add-on!
WireGuard is currently under heavy development, but already it might be regarded as the most secure, easiest to use, and the simplest VPN solution in the industry.
WireGuard is pretty simple, however, can be quite complex for user that isn’t familiar with all terminology used. The add-on takes care of a lot of things for you (if you want).
Follow the following steps for installation & a quick start:
Click the Home Assistant My button below to open the add-on on your Home Assistant instance.
Click the «Install» button to install the add-on.
Save the configuration.
Start the «WireGuard» add-on
Check the logs of the «WireGuard» add-on to see if everything went well.
Forward port 51820 (UDP!) in your router to your Home Assistant instance.
Download/Open the file /ssl/wireguard/myphone/qrcode.png stored on your Home Assistant instance, e.g., using Samba, Visual Studio Code or the Configurator add-on.
Install the WireGuard app on your phone.
Add a new WireGuard connection to your phone, by scanning the QR code.
Now, for starters, don’t get scared by the number of options and difficult terms this add-on provides. WireGuard can be a complex piece of software, but the add-on only has a few, simple, required settings. All the rest is handled by the add-on. However, If you would like to set up a more complex configuration, the add-on would allow that, too.
If you are familiar with WireGuard, please note the following: The configuration of WireGuard looks very similar to all terms used in the WireGuard configuration. There is, however, one big difference: The add-on is able to generate configurations for the add-on, but also for the peers (clients).
Note: Remember to restart the add-on when the configuration is changed.
A little more extensive example add-on configuration:
Note: This is just an example, don’t copy and paste it! Create your own!
This configuration option is the hostname that your clients will use to connect to your WireGuard add-on. The host is mainly used to generate client configurations and SHOULD NOT contain a port. If you want to change the port, use the «Network» section of the add-on configuration.
DO NOT attempt to use a URL such as a Nabu Casa endpoint, the entry needs to be either a DNS entry or IP address that is accessible by the clients.
A list of IP (IPv4 or IPv6) addresses (optionally with CIDR masks) to be assigned to the server/add-on interface.
It is strongly advised to create/use a separate IP address space from your home network, e.g., if your home network uses 192.168.1.x then DO NOT use that for the add-on.
Option: server.dns (optional)
A list of DNS servers used by the add-on and the configuration generated for the clients. This configuration option is optional, and if no DNS servers are set, it will use the built-in DNS server from Hass.io.
If you are running the AdGuard add-on, you can add 172.30.32.1 as a DNS IP address in the list. This will cause your clients to use those. What this does, it effectively making your clients to have ad-filtering (e.g., your mobile phone), while not at home.
Option: server.private_key (optional)
Option: server.public_key (optional)
If you don’t supply one, the add-on will calculate one based on the private key that was supplied via the server.private_key or, in case no private key was supplied, calculate it from the generated private key.
Option: server.fwmark (optional)
A 32-bit fwmark for outgoing packets. May be specified in hexadecimal by prepending «0x». If you don’t know what this is, then you probably don’t need it.
Option: server.table (optional)
Controls the routing table to which routes are added. Setting it to off disables the creation of routes altogether. When not provided, the add-on adds routes to the default table and enables special handling of default routes.
Option: server.pre_up (optional)
Allows you to run commands before WireGuard is started.
Option: server.pre_down (optional)
Allows you to run commands before WireGuard is stopped.
Option: server.post_up (optional)
Allows you to run commands after WireGuard has been started. This is useful for modifying things like routing. If not provided, the add-on will by default route all traffic coming in from the VPN through your home network.
By default it executes the following:
Option: server.post_down (optional)
Allows you to run commands after WireGuard has been stopped. This is useful for modifying things like routing. If not provided, the add-on will by default remove the default rules created by the post_up defaults.
By default it executes the following:
Option: server.mtu (optional)
The MTU is automatically determined from the endpoint addresses or the system default route, which is usually a sane choice.
However, to manually specify an MTU to override this automatic discovery, this value may be specified explicitly.
This name is also used for creating the directory in /ssl/wireguard where the generated client configuration and QR codes are stored. Therefore, a name has a maximum of 32 characters, can only contain A-Z (or a-z) and 0-9. Names may contain a hyphen (-) but must not start or end with one.
A list of IP (IPv4 or IPv6) addresses (optionally with CIDR masks) to be assigned to the peer.
This is used in the client configuration, but also for used by the add-on to set the allowed IPs (unless overriden by the peers.allowed_ips option.)
Option: peers.private_key (optional)
Technically, the add-on does not need this, however, since the add-on can generate client configurations, it can be helpful.
If no private key and no public key is provided, the add-on will generate one for you and store it in: /ssl/wireguard/
Private keys, in general, should only be known by client, while this add-on supports setting or generating one for your client is helpful and easy, it isn’t the best security practice. The best practice is to provide just the peers.public_key option below, the add-on will honor that.
Option: peers.public_key (optional, but recommended!)
If you don’t supply one, the add-on will calculate one based on the private key that was supplied via the peer.private_key or, in case no private key was supplied, calculated it from the generated private key for this peer.
While this add-on can generate public/private keypairs, from best security practice perspective, it is strongly advised to manually provide a public key for each of your peers. In that case, the add-on will not generate or configure a private key by itself.
Option: peers.allowed_ips (optional)
This configuration only valid for the add-on/server end and does not affect client configurations!
A list of IPs (IPv4 or IPv6) addresses (optionally with CIDR masks) from which incoming traffic for this peer is allowed and to which outgoing traffic for this peer is directed.
The catch-all 0.0.0.0/0 may be specified for matching all IPv4 addresses, and ::/0 may be specified for matching all IPv6 addresses.
Option: peers.client_allowed_ips (optional)
This configuration only valid for the peer end/client configuration and does not affect the server/add-on!
A list of IPs (IPv4 or IPv6) addresses (optionally with CIDR masks) from which incoming traffic from the server is allowed and to which outgoing traffic for this peer is directed.
The catch-all 0.0.0.0/0 may be specified for matching all IPv4 addresses, and ::/0 may be specified for matching all IPv6 addresses.
If not configured, the add-on will use 0.0.0.0/0 in the generated client configuration, routing all traffic on your client through the VPN tunnel.
Option: peers.persistent_keep_alive (optional)
A seconds interval, between 1 and 65535 inclusive, of how often to send an authenticated empty packet to the peer for the purpose of keeping a stateful firewall or NAT mapping valid persistently.
For example, if the interface very rarely sends traffic, but it might at anytime receive traffic from a peer, and it is behind NAT, the interface might benefit from having a persistent keepalive interval of 25 seconds.
By default or when unspecified, this option is set to 25 seconds. This is different from the WireGuard default, since the use case for this add-on is most likely to be installed in home setups behind a NAT.
If set to «off», this option is disabled.
Option: peers.endpoint (optional)
An endpoint IP or hostname, followed by a colon, and then a port number. This is used by the add-on/server to connect to its peer.
This is completely optional as the endpoint will be updated automatically to the most recent source IP address and port of correctly authenticated packets from the peer/client.
Option: peers.pre_shared_key (optional)
Option: peers.fwmark (optional)
This configuration only valid for the peer end/client configuration and does not affect the server/add-on!
A 32-bit fwmark for outgoing packets. May be specified in hexadecimal by prepending «0x». If you don’t know what this is, then you probably don’t need it.
Option: log_level (optional)
The log_level option controls the level of log output by the addon and can be changed to be more or less verbose, which might be useful when you are dealing with an unknown issue. Possible values are:
Finding generated client configurations
Each peer/client will have its own folder, by the name specified in the add-on configuration. The add-on additionally generates an image for each client containing a QR code, to allow a quick an easy set up on, e.g., your mobile phone.
Using on a Generic Linux/Debian/Ubuntu-based Hass.io system
The HassOS operating system for Hass.io by default has installed WireGuard support in its Linux kernel. However, if you run Hass.io on a generic Linux installation (e.g., based on Ubuntu or Debian), WireGuard support is not available by default.
This will cause the add-on to throw a large warning during the start up. However, the add-on will work as advertised!
When this happens, the add-on falls back on a standalone instance of WireGuard running inside the add-on itself. This method has drawbacks in terms of performance.
In order to run WireGuard optimal, you should install WireGuard on your host system. The add-on will pick that up automatically on the next start.
Источники:
- http://barzunov.ru/2022/03/create-qr-code-for-wireguard/
- http://causa-arcana.com/blog/2021/09/14/wireguard.html
- http://github.com/pbengert/wireguard-config-generator
- http://wiki.archlinux.org/title/WireGuard
- http://github.com/mzpqnxow/generate-wireguard-allowed-qr
- http://zach.codes/setting-up-wireguard/
- http://wiki.dd-wrt.com/wiki/index.php/Wireguard
- http://forum.dd-wrt.com/wiki/index.php/Wireguard
- http://docs.pivpn.io/wireguard/
- http://grh.am/2018/wireguard-setup-guide-for-ios/
- http://wiki.debian.org/FreedomBox/Manual/WireGuard
- http://habr.com/en/post/449234/
- http://thomasward.com/openbsd-wireguard/
- http://github.com/psyhomb/wireguard-tools
- http://www.smarthomebeginner.com/wireguard-android-client-setup/
- http://github.com/burghardt/easy-wg-quick
- http://github.com/suquant/wgrest
- http://github.com/mzpqnxow/generate-wireguard-allowed-qr/blob/master/README.md
- http://habr.com/ru/post/448528/
- http://3dnews.ru/1002719/wireguard-vpn-setup
- http://forums.unraid.net/topic/84226-wireguard-quickstart/
- http://apps.apple.com/us/app/wireguard/id1451685025?mt=12
- http://apps.apple.com/us/app/wireguard/id1441195209
- http://github.com/xei/wireguard-setup-scripts
- http://blog.wtigga.com/wireguard-2021/
- http://www.wireguard.com/quickstart/
- http://wdullaer.com/blog/2019/01/07/easily-extend-a-lan-to-an-android-phone-using-wireguard/
- http://github.com/warner/wireguard-vanity-address
- http://pimylifeup.com/raspberry-pi-wireguard/
- http://wiki.calculate-linux.org/wireguard
- http://sensorsiot.github.io/IOTstack/Containers/WireGuard/
- http://tech.serhatteker.com/post/2021-01/how-to-set-up-wireguard-client-on-android/
- http://barzunov.ru/2022/03/setup-wireguard-vpn-on-ubuntu/
- http://rercon.net/2021/03/20/wireguard/
- http://githubhelp.com/xei/wireguard-setup-scripts
- http://githubhelp.com/donaldzou/wireguard-dashboard
- http://github.com/WeeJeWel/wg-easy
- http://github.com/donaldzou/WGDashboard
- http://serversideup.net/how-to-configure-a-wireguard-android-vpn-client/
- http://github.com/opnsense/plugins/issues/1868
- http://dev.to/ivanmoreno/how-to-install-and-configure-you-own-vpn-server-in-gcp-with-wireguard-2af0
- http://github.com/ngoduykhanh/wireguard-ui
- http://github.com/alectrocute/wg-api
- http://kvvhost.ru/2020/02/26/wireguard-ubuntu-16-04/
- http://github.com/axllent/wireguard-vanity-keygen
- http://github.com/linuxserver/docker-wireguard
- http://emanuelduss.ch/2018/09/29/wireguard-vpn-road-warrior-setup/
- http://serversideup.net/how-to-configure-a-wireguard-ios-client/
- http://github.com/tusc/wireguard-kmod
- http://unixawesome.com/blog/wireguard-ustanovka-i-nastrojka/
- http://github.com/hassio-addons/addon-wireguard/blob/main/wireguard/DOCS.md